The deluge of patches in April dried up considerably in Might, as Microsoft on Tuesday launched 59 patches touching 11 product households. Home windows as common takes the lion’s share of patches with 48, with the remaining unfold amongst .NET, 365 Apps for Enterprise, Azure, Bing Seek for iOS, Dynamics 365, Intune, Workplace, Energy BI, SharePoint, and Visible Studio. There is only one critical-severity difficulty, affecting SharePoint.
At patch time, two points, each important-severity faults affecting Home windows, are identified to be beneath energetic exploit within the wild. Ten extra important-severity vulnerabilities in Home windows and SharePoint are by the corporate’s estimation extra prone to be exploited within the subsequent 30 days. Eight of the problems are amenable to detection by Sophos protections, and we embrace data on these in a desk under.
Along with these patches, the discharge consists of advisory data on six patches associated to the Edge browser; two associated to Visible Studio however managed by GitHub, not Microsoft; and 4 from Adobe. We don’t embrace advisories within the CVE counts and graphics under, however we offer data on all of them in an appendix on the finish of the article. We’re as common together with on the finish of this publish three different appendices itemizing all Microsoft’s patches, sorted by severity, by predicted exploitability, and by product household.
By the numbers
- Complete Microsoft CVEs: 59
- Complete Edge / Chrome advisory points lined in replace: 6
- Complete non-Microsoft Visible Studio advisory points lined in replace: 2
- Complete Adobe points lined in replace: 4
- Publicly disclosed: 2
- Exploited: 2
- Severity
- Crucial: 1
- Essential: 57
- Reasonable: 1
- Influence:
- Distant Code Execution: 25
- Elevation of Privilege: 17
- Data Disclosure: 7
- Spoofing: 4
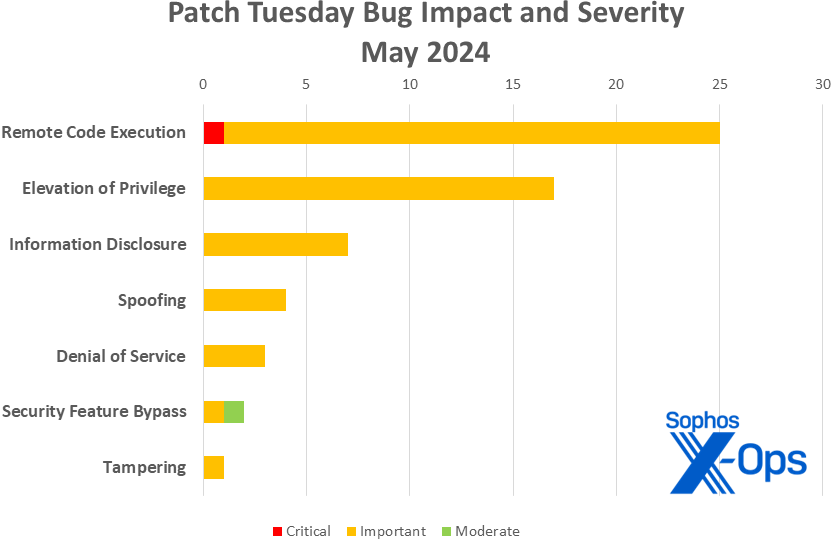
- Denial of Service: 3
- Safety Function Bypass: 2
- Tampering: 1
Determine 1: Might continues the earlier month’s emphasis on RCE points, although all seven of Microsoft’s common impression classes put in an look
Merchandise
- Home windows: 48
- Dynamics 365: 2
- SharePoint: 2
- Visible Studio: 2 (together with one shared with .NET; as well as, two advisory points apply to VS)
- .NET: 1 (shared with Visible Studio)
- 365 Apps for Enterprise: 1 (shared with Workplace)
- Azure: 1
- Bing Seek for iOS: 1
- Intune: 1
- Workplace: 1 (shared with 365 Apps for Enterprise)
- Energy BI: 1
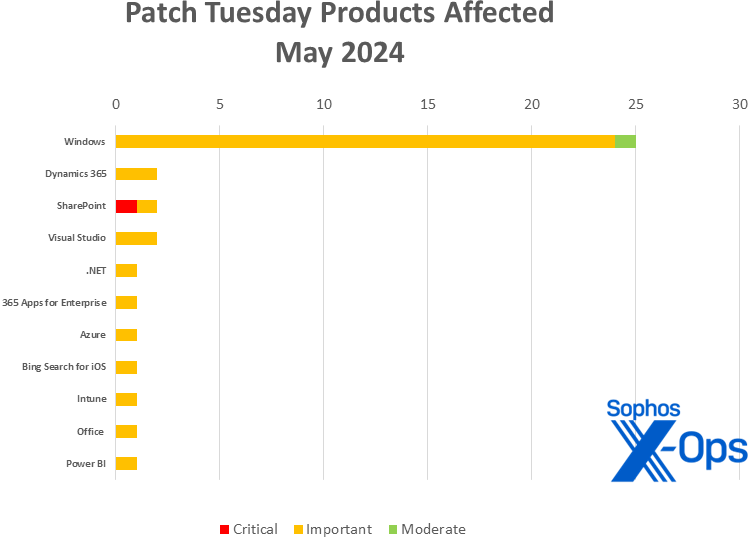
Determine 2: Home windows takes the overwhelming variety of Might patches, however solely SharePoint has a critical-severity difficulty to handle
Notable Might updates and themes
Along with the problems mentioned above, just a few particular gadgets benefit consideration.
CVE-2024-4559 – Chromium: CVE-2024-4671 Use after free in Visuals
Are we actually main this part with an advisory this month? Sure. This Chrome bug was technically patched Friday (in the future after an nameless researcher reported it to Google), and it’s talked about in Microsoft’s Patch Tuesday launch merely to guarantee Edge customers that the newest model addresses this high-severity difficulty. That stated, Edge – and all browsers utilizing Chromium OSS – must patch instantly, as this one was discovered within the wild. Go.
CVE-2024-30040 – Home windows MSHTML Platform Safety Function Bypass Vulnerability
CVE-2024-30051 — Home windows DWM Core Library Elevation of Privilege Vulnerability
Two extra points have been detected beneath exploit within the wild. The MSHTML difficulty has a base CVSS worth of 8.8; the bug bypasses a function in Microsoft 365 known as OLE Auto-Activation Block, which permits admins to forestall abuse of OLE/COM. An attacker would abuse this bug by sending the focused person a maliciously crafted file after which convincing them, to cite the bulletin, “to govern the specifically crafted file, however not essentially click on or open the malicious file.” The DWM Core Library difficulty has a decrease 7.8 base CVSS – and shares the stage with three different fixes addressing that part – however the checklist of credited finders is numerous and startling, together with researchers from Kaspersky, Google Risk Evaluation Group, Google Mandiant, and DBAPPSecurity WeBin Lab.
CVE-2024-30050 – Home windows Mark of the Net Safety Function Bypass Vulnerability
April showers could also be over, however the regular pitter-pat of Mark of the Net points continues. This one’s Reasonable in impression and restricted in scope – a profitable assault would result in restricted losses of integrity and availability of safety features that depend on MotW, together with Protected Mode in Workplace. Nonetheless, Microsoft assesses this one to be extra prone to be exploited throughout the subsequent 30 days, and the makes use of of a vulnerability like this in a chained assault must be stored in thoughts. Sophos has developed Intercept X/Endpoint IPS and XGS Firewall protections in opposition to this difficulty, as lined within the desk under.
CVE-2024-30044 – Microsoft SharePoint Server Distant Code Execution Vulnerability
The month’s sole Crucial-severity vulnerability impacts SharePoint and is believed by Microsoft to be extra prone to see exploitation within the subsequent 30 days. As soon as once more, Sophos has developed Intercept X/Endpoint IPS and XGS Firewall protections in opposition to this difficulty, as lined within the desk under.
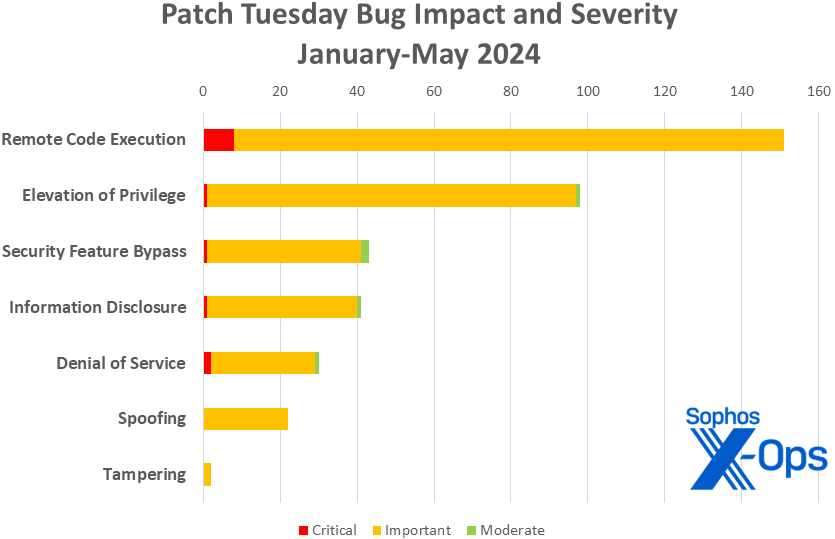
Determine 3: RCE points proceed to outpace all different kinds of vulnerability in 2024
Sophos protections
| CVE | Sophos Intercept X/Endpoint IPS | Sophos XGS Firewall |
| CVE-2024-29996 | Exp/2429996-A | Exp/2429996-A |
| CVE-2024-30025 | Exp/2430025-A | Exp/2430025-A |
| CVE-2024-30032 | Exp/2430032-A | Exp/2430032-A |
| CVE-2024-30034 | Exp/2430034-A | Exp/2430034-A |
| CVE-2024-30035 | Exp/2430035-A | Exp/2430035-A |
| CVE-2024-30037 | Exp/2430037-A | Exp/2430037-A |
| CVE-2024-30044 | Exp/2430044-A, sid:2309589 | sid:2309589 |
| CVE-2024-30050 | sid:2309595 | sid:2309595 |
As you may each month, should you don’t need to wait in your system to drag down Microsoft’s updates itself, you may obtain them manually from the Home windows Replace Catalog web site. Run the winver.exe device to find out which construct of Home windows 10 or 11 you’re working, then obtain the Cumulative Replace package deal in your particular system’s structure and construct quantity.
Appendix A: Vulnerability Influence and Severity
It is a checklist of Might patches sorted by impression, then sub-sorted by severity. Every checklist is additional organized by CVE.
Distant Code Execution (25 CVEs)
| Crucial severity | |
| CVE-2024-30044 | Microsoft SharePoint Server Distant Code Execution Vulnerability |
| Essential severity | |
| CVE-2024-29997 | Home windows Cell Broadband Driver Distant Code Execution Vulnerability |
| CVE-2024-29998 | Home windows Cell Broadband Driver Distant Code Execution Vulnerability |
| CVE-2024-29999 | Home windows Cell Broadband Driver Distant Code Execution Vulnerability |
| CVE-2024-30000 | Home windows Cell Broadband Driver Distant Code Execution Vulnerability |
| CVE-2024-30001 | Home windows Cell Broadband Driver Distant Code Execution Vulnerability |
| CVE-2024-30002 | Home windows Cell Broadband Driver Distant Code Execution Vulnerability |
| CVE-2024-30003 | Home windows Cell Broadband Driver Distant Code Execution Vulnerability |
| CVE-2024-30004 | Home windows Cell Broadband Driver Distant Code Execution Vulnerability |
| CVE-2024-30005 | Home windows Cell Broadband Driver Distant Code Execution Vulnerability |
| CVE-2024-30006 | Microsoft WDAC OLE DB supplier for SQL Server Distant Code Execution Vulnerability |
| CVE-2024-30009 | Home windows Routing and Distant Entry Service (RRAS) Distant Code Execution Vulnerability |
| CVE-2024-30010 | Home windows Hyper-V Distant Code Execution Vulnerability |
| CVE-2024-30012 | Home windows Cell Broadband Driver Distant Code Execution Vulnerability |
| CVE-2024-30014 | Home windows Routing and Distant Entry Service (RRAS) Distant Code Execution Vulnerability |
| CVE-2024-30015 | Home windows Routing and Distant Entry Service (RRAS) Distant Code Execution Vulnerability |
| CVE-2024-30017 | Home windows Hyper-V Distant Code Execution Vulnerability |
| CVE-2024-30020 | Home windows Cryptographic Companies Distant Code Execution Vulnerability |
| CVE-2024-30021 | Home windows Cell Broadband Driver Distant Code Execution Vulnerability |
| CVE-2024-30022 | Home windows Routing and Distant Entry Service (RRAS) Distant Code Execution Vulnerability |
| CVE-2024-30023 | Home windows Routing and Distant Entry Service (RRAS) Distant Code Execution Vulnerability |
| CVE-2024-30024 | Home windows Routing and Distant Entry Service (RRAS) Distant Code Execution Vulnerability |
| CVE-2024-30029 | Home windows Routing and Distant Entry Service (RRAS) Distant Code Execution Vulnerability |
| CVE-2024-30042 | Microsoft Excel Distant Code Execution Vulnerability |
| CVE-2024-30045 | .NET and Visible Studio Distant Code Execution Vulnerability |
Elevation of Privilege (17 CVEs)
| Essential severity | |
| CVE-2024-26238 | Microsoft PLUGScheduler Scheduled Process Elevation of Privilege Vulnerability |
| CVE-2024-29994 | Microsoft Home windows SCSI Class System File Elevation of Privilege Vulnerability |
| CVE-2024-29996 | Home windows Widespread Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2024-30007 | Microsoft Brokering File System Elevation of Privilege Vulnerability |
| CVE-2024-30018 | Home windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-30025 | Home windows Widespread Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2024-30027 | NTFS Elevation of Privilege Vulnerability |
| CVE-2024-30028 | Win32k Elevation of Privilege Vulnerability |
| CVE-2024-30030 | Win32k Elevation of Privilege Vulnerability |
| CVE-2024-30031 | Home windows CNG Key Isolation Service Elevation of Privilege Vulnerability |
| CVE-2024-30032 | Home windows DWM Core Library Elevation of Privilege Vulnerability |
| CVE-2024-30033 | Home windows Search Service Elevation of Privilege Vulnerability |
| CVE-2024-30035 | Home windows DWM Core Library Elevation of Privilege Vulnerability |
| CVE-2024-30037 | Home windows Widespread Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2024-30038 | Win32k Elevation of Privilege Vulnerability |
| CVE-2024-30049 | Home windows Win32 Kernel Subsystem Elevation of Privilege Vulnerability |
| CVE-2024-30051 | Home windows DWM Core Library Elevation of Privilege Vulnerability |
Data Disclosure (7 CVEs)
| Essential severity | |
| CVE-2024-30008 | Home windows DWM Core Library Data Disclosure Vulnerability |
| CVE-2024-30016 | Home windows Cryptographic Companies Data Disclosure Vulnerability |
| CVE-2024-30034 | Home windows Cloud Information Mini Filter Driver Data Disclosure Vulnerability |
| CVE-2024-30036 | Home windows Deployment Companies Data Disclosure Vulnerability |
| CVE-2024-30039 | Home windows Distant Entry Connection Supervisor Data Disclosure Vulnerability |
| CVE-2024-30043 | Microsoft SharePoint Server Data Disclosure Vulnerability |
| CVE-2024-30054 | Microsoft Energy BI Shopper Javascript SDK Data Disclosure Vulnerability |
Spoofing (4 CVEs)
| Essential severity | |
| CVE-2024-30041 | Microsoft Bing Search Spoofing Vulnerability |
| CVE-2024-30047 | Dynamics 365 Buyer Insights Spoofing Vulnerability |
| CVE-2024-30048 | Dynamics 365 Buyer Insights Spoofing Vulnerability |
| CVE-2024-30053 | Azure Migrate Cross-Website Scripting Vulnerability |
Denial of Service (3 CVEs)
| Essential severity | |
| CVE-2024-30011 | Home windows Hyper-V Denial of Service Vulnerability |
| CVE-2024-30019 | DHCP Server Service Denial of Service Vulnerability |
| CVE-2024-30046 | Visible Studio Denial of Service Vulnerability |
Safety Function Bypass (2 CVEs)
| Essential severity | |
| CVE-2024-30040 | Home windows MSHTML Platform Safety Function Bypass Vulnerability |
| Reasonable severity | |
| CVE-2024-30050 | Home windows Mark of the Net Safety Function Bypass Vulnerability |
Tampering (1 CVE)
| Essential severity | |
| CVE-2024-30059 | Microsoft Intune for Android Cell Software Administration Tampering Vulnerability |
Appendix B: Exploitability
It is a checklist of the Might CVEs already beneath exploit within the wild, and people judged by Microsoft to be extra prone to be exploited within the wild throughout the first 30 days post-release. The checklist is organized by CVE.
| Exploitation detected | |
| CVE-2024-30040 | Home windows MSHTML Platform Safety Function Bypass Vulnerability |
| CVE-2024-30051 | Home windows DWM Core Library Elevation of Privilege Vulnerability |
| Exploitation extra doubtless throughout the subsequent 30 days | |
| CVE-2024-29996 | Home windows Widespread Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2024-30025 | Home windows Widespread Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2024-30032 | Home windows DWM Core Library Elevation of Privilege Vulnerability |
| CVE-2024-30034 | Home windows Cloud Information Mini Filter Driver Data Disclosure Vulnerability |
| CVE-2024-30035 | Home windows DWM Core Library Elevation of Privilege Vulnerability |
| CVE-2024-30037 | Home windows Widespread Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2024-30038 | Win32k Elevation of Privilege Vulnerability |
| CVE-2024-30044 | Microsoft SharePoint Server Distant Code Execution Vulnerability |
| CVE-2024-30049 | Home windows Win32 Kernel Subsystem Elevation of Privilege Vulnerability |
| CVE-2024-30050 | Home windows Mark of the Net Safety Function Bypass Vulnerability |
Appendix C: Merchandise Affected
It is a checklist of Might’s patches sorted by product household, then sub-sorted by severity. Every checklist is additional organized by CVE. Patches which can be shared amongst a number of product households are listed a number of occasions, as soon as for every product household.
Home windows (48 CVEs)
| Essential severity | |
| CVE-2024-26238 | Microsoft PLUGScheduler Scheduled Process Elevation of Privilege Vulnerability |
| CVE-2024-29994 | Microsoft Home windows SCSI Class System File Elevation of Privilege Vulnerability |
| CVE-2024-29996 | Home windows Widespread Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2024-29997 | Home windows Cell Broadband Driver Distant Code Execution Vulnerability |
| CVE-2024-29998 | Home windows Cell Broadband Driver Distant Code Execution Vulnerability |
| CVE-2024-29999 | Home windows Cell Broadband Driver Distant Code Execution Vulnerability |
| CVE-2024-30000 | Home windows Cell Broadband Driver Distant Code Execution Vulnerability |
| CVE-2024-30001 | Home windows Cell Broadband Driver Distant Code Execution Vulnerability |
| CVE-2024-30002 | Home windows Cell Broadband Driver Distant Code Execution Vulnerability |
| CVE-2024-30003 | Home windows Cell Broadband Driver Distant Code Execution Vulnerability |
| CVE-2024-30004 | Home windows Cell Broadband Driver Distant Code Execution Vulnerability |
| CVE-2024-30005 | Home windows Cell Broadband Driver Distant Code Execution Vulnerability |
| CVE-2024-30006 | Microsoft WDAC OLE DB supplier for SQL Server Distant Code Execution Vulnerability |
| CVE-2024-30007 | Microsoft Brokering File System Elevation of Privilege Vulnerability |
| CVE-2024-30008 | Home windows DWM Core Library Data Disclosure Vulnerability |
| CVE-2024-30009 | Home windows Routing and Distant Entry Service (RRAS) Distant Code Execution Vulnerability |
| CVE-2024-30010 | Home windows Hyper-V Distant Code Execution Vulnerability |
| CVE-2024-30011 | Home windows Hyper-V Denial of Service Vulnerability |
| CVE-2024-30012 | Home windows Cell Broadband Driver Distant Code Execution Vulnerability |
| CVE-2024-30014 | Home windows Routing and Distant Entry Service (RRAS) Distant Code Execution Vulnerability |
| CVE-2024-30015 | Home windows Routing and Distant Entry Service (RRAS) Distant Code Execution Vulnerability |
| CVE-2024-30016 | Home windows Cryptographic Companies Data Disclosure Vulnerability |
| CVE-2024-30017 | Home windows Hyper-V Distant Code Execution Vulnerability |
| CVE-2024-30018 | Home windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-30019 | DHCP Server Service Denial of Service Vulnerability |
| CVE-2024-30020 | Home windows Cryptographic Companies Distant Code Execution Vulnerability |
| CVE-2024-30021 | Home windows Cell Broadband Driver Distant Code Execution Vulnerability |
| CVE-2024-30022 | Home windows Routing and Distant Entry Service (RRAS) Distant Code Execution Vulnerability |
| CVE-2024-30023 | Home windows Routing and Distant Entry Service (RRAS) Distant Code Execution Vulnerability |
| CVE-2024-30024 | Home windows Routing and Distant Entry Service (RRAS) Distant Code Execution Vulnerability |
| CVE-2024-30025 | Home windows Widespread Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2024-30027 | NTFS Elevation of Privilege Vulnerability |
| CVE-2024-30028 | Win32k Elevation of Privilege Vulnerability |
| CVE-2024-30029 | Home windows Routing and Distant Entry Service (RRAS) Distant Code Execution Vulnerability |
| CVE-2024-30030 | Win32k Elevation of Privilege Vulnerability |
| CVE-2024-30031 | Home windows CNG Key Isolation Service Elevation of Privilege Vulnerability |
| CVE-2024-30032 | Home windows DWM Core Library Elevation of Privilege Vulnerability |
| CVE-2024-30033 | Home windows Search Service Elevation of Privilege Vulnerability |
| CVE-2024-30034 | Home windows Cloud Information Mini Filter Driver Data Disclosure Vulnerability |
| CVE-2024-30035 | Home windows DWM Core Library Elevation of Privilege Vulnerability |
| CVE-2024-30036 | Home windows Deployment Companies Data Disclosure Vulnerability |
| CVE-2024-30037 | Home windows Widespread Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2024-30038 | Win32k Elevation of Privilege Vulnerability |
| CVE-2024-30039 | Home windows Distant Entry Connection Supervisor Data Disclosure Vulnerability |
| CVE-2024-30040 | Home windows MSHTML Platform Safety Function Bypass Vulnerability |
| CVE-2024-30049 | Home windows Win32 Kernel Subsystem Elevation of Privilege Vulnerability |
| CVE-2024-30051 | Home windows DWM Core Library Elevation of Privilege Vulnerability |
| Reasonable severity | |
| CVE-2024-30050 | Home windows Mark of the Net Safety Function Bypass Vulnerability |
Dynamics 365 (2 CVEs)
| Essential severity | |
| CVE-2024-30047 | Dynamics 365 Buyer Insights Spoofing Vulnerability |
| CVE-2024-30048 | Dynamics 365 Buyer Insights Spoofing Vulnerability |
SharePoint (2 CVEs)
| Crucial severity | |
| CVE-2024-30044 | Microsoft SharePoint Server Distant Code Execution Vulnerability |
| Essential severity | |
| CVE-2024-30043 | Microsoft SharePoint Server Data Disclosure Vulnerability |
Visible Studio (2* CVEs)
| Essential severity | |
| CVE-2024-30045 | .NET and Visible Studio Distant Code Execution Vulnerability |
| CVE-2024-30046 | Visible Studio Denial of Service Vulnerability |
* As well as, this launch consists of data on two GitHub-issued advisories affecting Visible Studio; please see Appendix D for particulars.
.NET (1 CVE)
| Essential severity | |
| CVE-2024-30045 | .NET and Visible Studio Distant Code Execution Vulnerability |
365 Apps for Enterprise (1 CVE)
| Essential severity | |
| CVE-2024-30042 | Microsoft Excel Distant Code Execution Vulnerability |
Azure (1 CVE)
| Essential severity | |
| CVE-2024-30053 | Azure Migrate Cross-Website Scripting Vulnerability |
Bing Seek for iOS (1 CVE)
| Essential severity | |
| CVE-2024-30041 | Microsoft Bing Search Spoofing Vulnerability |
Intune (1 CVE)
| Essential severity | |
| CVE-2024-30059 | Microsoft Intune for Android Cell Software Administration Tampering Vulnerability |
Workplace (1 CVE)
| Essential severity | |
| CVE-2024-30042 | Microsoft Excel Distant Code Execution Vulnerability |
Energy BI (1 CVE)
| Essential severity | |
| CVE-2024-30054 | Microsoft Energy BI Shopper Javascript SDK Data Disclosure Vulnerability |
Appendix D: Advisories and Different Merchandise
It is a checklist of advisories and knowledge on different related CVEs within the Might Microsoft launch, sorted by product.
Related to Edge / Chromium (6 CVEs)
| CVE-2024-4331 | Chromium: CVE-2024-4331 Use after free in Image In Image |
| CVE-2024-4368 | Chromium: CVE-2024-4368 Use after free in Daybreak |
| CVE-2024-4558 | Chromium: CVE-2024-4558 Use after free in ANGLE |
| CVE-2024-4559 | Chromium: CVE-2024-4559 Heap buffer overflow in WebAudio |
| CVE-2024-4671 | Chromium: CVE-2024-4671 Use after free in Visuals |
| CVE-2024-30055 | Microsoft Edge (Chromium-based) Spoofing Vulnerability |
Related to Visible Studio (non-Microsoft CVE issuer) (2 CVEs)
| CVE-2024-32002 | Recursive clones on case-insensitive filesystems that help symlinks are inclined to Distant Code Execution |
| CVE-2024-32004 | GitHub: CVE-2023-32004 Distant Code Execution whereas cloning special-crafted native repositories |
Related to Adobe (non-Microsoft launch) (4 CVEs)
| CVE-2024-30284 | Use After Free (CWE-416) |
| CVE-2024-30310 | Out-of-bounds Write (CWE-787) |
| CVE-2024-30311 | Out-of-bounds Learn (CWE-125) |
| CVE-2024-30312 | Out-of-bounds Learn (CWE-125) |










