Researchers have attributed the current JumpCloud breach to a department of North Korea’s Lazarus Group. Early indications recommend that the group was financially motivated, primarily focusing on cryptocurrency and blockchain firms.
JumpCloud is an enterprise directory-as-a-service supplier serving over 180,000 prospects, in accordance with its web site, together with Monday.com, GoFundMe, and others. 6sense tracks its platform because the thirty second hottest in id and entry administration (IAM), with a 0.2% market share.
On July 12, JumpCloud CISO Robert Phan revealed in a weblog put up “a complicated nation-state sponsored risk actor that gained unauthorized entry to our programs to focus on a small and particular set of our prospects.” Precisely which nation-state was unclear till right now, when Tom Hegel, senior risk researcher with SentinelOne, tied the hacker-controlled infrastructure to North Korea. Hegel additionally related the assault with a social engineering marketing campaign recognized by Github on July 18.
Crowdstrike, working straight with JumpCloud, supplied extra particular attribution to Reuters right now, naming a subsect of the Lazarus Group they monitor as “Labyrinth Chollima.”
Now, working with victims of the breach, researchers from Mandiant are filling out much more of the puzzle. In upcoming analysis, the cybersecurity agency plans to disclose that the hackers are primarily focusing on the Web3 trade, stealing credentials from crypto and blockchain firms for follow-on assaults.
JumpCloud Breach Chronology
JumpCloud first turned conscious of suspicious exercise on June 27, at 3:13 P.M. UTC. It occurred “on an inside orchestration system which we traced again to a complicated spear-phishing marketing campaign,” Pham wrote, which started the week prior, on June 22.
The attackers had managed to succeed in “a selected space of our infrastructure,” Pham admitted, efficiently performing a knowledge injection assault in opposition to the corporate’s instructions framework. To mitigate the harm, he wrote, “we rotated credentials, rebuilt infrastructure, and took a lot of different actions to additional safe our community and perimeter. Moreover, we activated our ready incident response plan and labored with our Incident Response (IR) associate to investigate all programs and logs for potential exercise. It was additionally presently, as a part of our IR plan, that we contacted and engaged legislation enforcement in our investigation.”
Preliminary proof of buyer compromise was noticed at 3:35 UTC on July 5. The corporate notified affected prospects and, later that day, initiated a force-rotation of all administrator API keys.
JumpCloud has not but disclosed what number of prospects have been affected by its breach, or how badly. Pham did observe that “the assault vector utilized by the risk actor has been mitigated.”
How IoCs Pointed To The DPRK
JumpCloud had recognized its hackers as a nation-state entity. However which one?
The proof was in the publicly disclosed indicators of compromise (IOCs). With them, Hegel says, “I will begin diving into the IPs themselves, attempting to grasp their profile, see what else is getting used on that server, what these domains are speaking to.” In a single case, Hegel related an IP with a website recognized in one other social engineering marketing campaign which GitHub attributed to North Korean hackers.
Hegel slowly mapped out the attackers’ command infrastructure — an IP that associated to a website, a website that associated to a beforehand recognized cluster or assault.
The attackers left behind sure digital fingerprints like how and when it was registered, in addition to “the timing of the way it resolves to different servers, and different random technical traits just like the SSL cert, or the software program operating on that server,” Hegel clarifies. “There are one million totally different attributes we will use to profile the fingerprint of a server, which, on this case, overlaps with different North Korean stuff.”
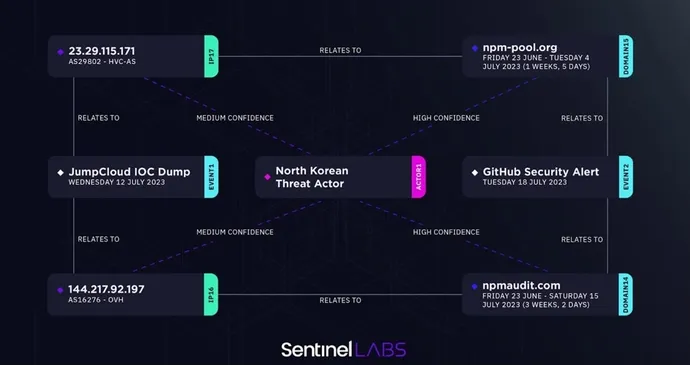
The picture above charts how the 2 campaigns, and the varied domains and IPs therein, are related. “Clustering all that collectively, you are getting an understanding that that is one large set of infrastructure. It is all associated,” Hegel explains. “And who do I see working out of this infrastructure? At that time, we’re seeing it overlap with a number of clusters of different Lazarus campaigns.”
Concentrating on the Crypto Business
As an IAM service supplier, JumpCloud supplies a direct path for hackers to steal credentials from firms that may show helpful for follow-on assaults. However what sort of assaults did Lazarus intend to pursue this time?
Right here too, on reflection, there have been clues. Like in JumpCloud’s weblog put up, the place Pham famous how the assault, removed from a basic spray-and-pray kind of marketing campaign, “was extraordinarily focused and restricted to particular prospects.”
And there was the GitHub assault to which Hegel drew a connection. In that case, “many of those focused accounts are related to the blockchain, cryptocurrency, or on-line playing sectors,” Github famous in its weblog put up.
In an announcement on the JumpCloud attackers shared with Darkish Studying, Mandiant revealed, “with excessive confidence that this can be a cryptocurrency-focused factor inside the DPRK’s Reconnaissance Basic Bureau (RGB), focusing on firms with cryptocurrency verticals to acquire credentials and reconnaissance knowledge,” the seller wrote. “It is a financially motivated risk actor that we have seen more and more goal the cryptocurrency trade and varied blockchain platforms.”
In response to Austin Larsen, Mandiant senior incident response advisor with Google Cloud, Mandiant has not recognized any monetary penalties for the JumpCloud victims it has labored with. Nevertheless, that solely appears to be as a result of “this marketing campaign was primarily centered on acquiring credentials from precedence targets and reconnaissance knowledge for future intrusions,” he says. In at the very least one case, actually, the crew “recognized proof that the actor efficiently accomplished their goal of gathering credentials from precedence targets.”
North Korean hackers focusing on the crypto trade to fund the Kim regime is nothing new. However the JumpCloud assault reiterates simply how refined and profitable their ongoing technique has change into. “They’re very inventive,” Hegel thinks. “It is actually showcasing their understanding, and their want to conduct multilevel provide chain assaults.”






:contrast(5):saturation(1.16)/https%3A%2F%2Fprod.static9.net.au%2Ffs%2Fa521a821-8701-47e1-a6c6-ab251c2e75ff)



