Invicti’s Chief Expertise Officer and Head of Safety Analysis, Frank Catucci, co-authored this text.
Two ideas regularly drive our work serving to you defend software program: Assume as attackers do, and intention for zero noise. Not all the things’s a disaster; in case you can’t prioritize, you’ll be extra susceptible, not much less. The October 25 announcement of two new OpenSSL vulnerabilities gives an ideal instance of what we imply. Is that this the subsequent Heartbleed?
No.
We’ll present you why, by approaching these vulnerabilities as an attacker would. The technical element is vital, however the takeaway is useless easy. Patch this with OpenSSL 3.0.7. You’ll be a bit safer. The world might be, too. However don’t spend one minute panicking. This one’s not price a freakout – both by you or by your safety methods.
Stepping again: What occurred in OpenSSL
A fast refresher in case you’ve been away: On October 25, OpenSSL notified customers that it had discovered two new vulnerabilities in OpenSSL 3.0.0 by way of 3.0.6. One in all these was apparently “crucial” – the identical stage because the infamous 2014 Heartbleed flaw. That captured everybody’s consideration as a result of Heartbleed affected many high-profile organizations, might compromise encrypted data of all types, and truly confirmed up within the wild. It was dangerous.
However by November 1, when OpenSSL launched its model 3.0.7 repair, it extra clearly understood the 2 new vulnerabilities and downgraded them to “excessive” severity (see advisory and weblog submit). Since we’re within the enterprise of scanning servers, purposes and APIs for vulnerabilities, we are able to add worth by illuminating why this was accomplished, with a concentrate on how attackers may attempt to exploit these flaws – and why they most likely can’t.
What to know first concerning the OpenSSL vulnerabilities
The primary new vulnerability, CVE-2022-3602, is an X.509 E-mail Handle 4-byte Buffer Overflow that may be triggered as identify constraints are checked throughout X.509 certificates verification. It solely happens after certificates chain signature verification. Furthermore, it requires both a trusted certificates authority (CA) to have signed the malicious certificates or for the appliance to proceed certificates verification even after it’s didn’t assemble a path to a trusted issuer.
These circumstances are unusual. A CA would have needed to signal a malicious certificates or the request would must be accepted with out verification. If that had occurred, you’d be in danger even with out these vulnerabilities.
As OpenSSL notes, an attacker might craft a malicious e-mail deal with to overflow 4 attacker-controlled bytes on the stack. This buffer overflow might trigger a crash (therefore, denial of service) or, doubtlessly, distant code execution (RCE). However no present exploit can leverage such an RCE.
The second new vulnerability, CVE-2022-3786, can also be an X.509 E-mail Handle Variable Size Buffer Overflow with related traits. However this one can’t trigger an RCE situation.
What an exploit would require
To see why we’re not too apprehensive, it helps to grasp how OpenSSL implements the SSL/TLS handshake and what it might take to make a profitable exploit.
Determine 1 reveals a typical certificates request and verification sequence. Earlier than a safe connection is established, an SSL/TLS handshake takes place to authenticate and negotiate among the many protocol variations and ciphers that the connection will use. After the consumer supplies its certificates, the server verifies that:
- The digital signature is reliable.
- The timestamp is legitimate.
- The certificates is legitimate and never revoked.
- Certificates Transparency is accurately logged.
That is the place the OpenSSL vulnerabilities may trigger bother, using a hostile payload in an e-mail deal with that’s embedded inside the consumer certificates and crafted in worldwide characters encoded in Punycode. However this circulation is simply used when the SSL/TLS server is configured to request consumer certificates, which is uncommon in public web websites. (The uncommon elective sequence the place these vulnerabilities apply is proven surrounded by dashed crimson strains.) For an exhaustive evaluation of how such a 4-byte stack overflow might work, see right here. Extra importantly for our functions, listed below are three causes most attackers will discover this vector problematic:
- Getting a CA to signal a malicious certificates isn’t straightforward or risk-free. A number of validation steps are required. That is sufficiently non-trivial that hackers could be extra more likely to assault the CA on to signal the certificates on their behalf.
- It may be laborious to discover a goal web site for an exploit that requests certificates solely from the CA that’s prepared to signal your malicious certificates. Many organizations use a number of CAs: you may encounter one you haven’t compromised.
- Fairly merely, it’s laborious to formulate a profitable assault that exploits these vulnerabilities. And, even when the above two circumstances can by some means be met…
4-byte stack overflows aren’t what they was
Even when an attacker overcomes all the opposite challenges, they’ll solely write a single 4-byte worth to the stack. Again within the day (we’re speaking the Nineties) 4 bytes was usually sufficient to overwrite a return pointer on a stack and execute arbitrary code. However not now. Let’s take into account why.
The Wikipedia picture beneath reveals how a buffer overflow can affect the code a compromised program executes. The assault depends on a buffer allotted on the stack adjoining to the return pointer. It specifies what’ll be executed when a program returns from calling a perform. When a programmer doesn’t verify the size of untrusted inputs, or makes an “off-by-one” error, an attacker can theoretically divert that subsequent step.
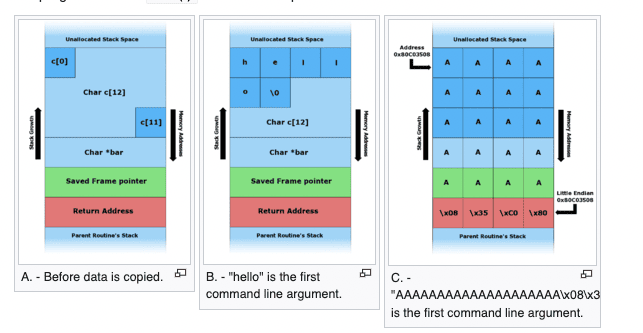
Nonetheless, that is a lot tougher with fashionable software program stacks. Take, as an illustration, Ubuntu 22.04, which ships OpenSSL 3.0.6. Ubuntu’s current Safety Advisory discusses the way it makes use of stack safety to assist mitigate buffer overflows.
With stack safety, a “canary,” or guard worth, is written in reminiscence proper earlier than the return pointer. It’s initialized to a random worth earlier than the perform is invoked, and verified when the perform returns. If it’s compromised, that’s an early warning of tampering with the return deal with – just like the traditional canary in a coal mine. Seeing that, this system terminates moderately than giving the attacker management.
One other method, Handle Area Format Randomization (ASLR), adjustments the reminiscence structure of the stack at program launch. Assaults that try to leap right into a compromised area of reminiscence grow to be far tougher as a result of attackers can’t depend on fastened positions in shell code.
Lastly, as OpenSSL reported in its weblog submit, there’s yet one more large impediment to weaponizing these two OpenSSL vulnerabilities. Linux distributors who’ve analyzed them discovered that the 4 bytes an attacker might affect are in a “useless area” of the stack that isn’t in use, and might’t affect this system counter.
When attackers take into account all these obstacles, most will most likely flip elsewhere. That’s why we expect it made sense for OpenSSL to downgrade these vulnerabilities from “crucial” to “excessive.”
The underside line (and what to do)
These are legit bugs, discovered by gifted researchers who deserve our appreciation. Remarkably, OpenSSL needed to change just one character to repair CVE-2022-3602 – and by tweaking that “equals signal” in OpenSSL 3.0.7, they’ve made the world a bit of safer. So: Scan with SCA to establish cases of OpenSSL 3.0.0–3.0.6 in your code base, and improve to three.0.7 as quickly as you’ll be able to. In case you receive OpenSSL out of your OS vendor or one other third social gathering, search updates from them as effectively. No panic. No flurry of pointless crimson alerts. Simply, as embroiderers and safety professionals are identified to say, preserve calm and patch on.
—
- Essich, CC BY 3.0 https://creativecommons.org/licenses/by/3.0, through Wikimedia Commons










