Learn extra about LockBit Ransomware:
LockBit Takedown: What You Must Find out about Operation Cronos
LockBit Infrastructure Disrupted by International Legislation Enforcers
LockBit and Royal Mail Ransomware Negotiation Leaked
LockBit Stays Prime International Ransomware Menace
“We all know who he’s. We all know the place he lives. We all know how a lot he’s value. LockbitSupp has engaged with legislation enforcement.”
This message was launched on LockBit ransomware group’s former knowledge leak website at 12pm GMT on February 23.
Nonetheless, for the 30,000 curious individuals who visited the web page this was not the information that they had anticipated.
They had been anticipating legislation enforcement businesses behind Operation Cronos, which took down LockBit’s infrastructure on February 19, to disclose the id of the group’s kingpin, recognized on the darkish net by the moniker LockbitSupp.
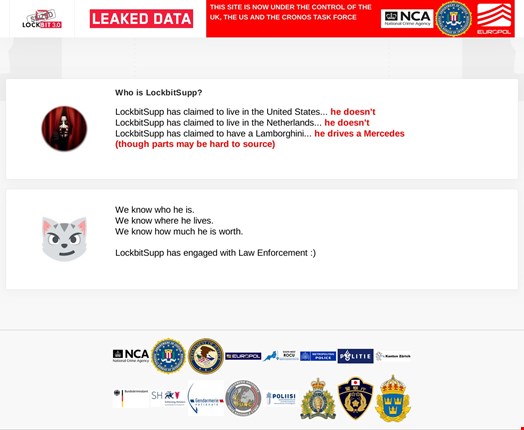
Nonetheless, the message taught us that legislation enforcement brokers do know who the person behind the LockbitSupp persona is and are speaking with him.
Moreover, the legislation enforcement message unveiled some revelations concerning the particular person, particularly that lots of his earlier claims referring to location and the automobile he drives are false (see above).
These LockbitSupp claims had been cited by Jon DiMaggio, chief safety strategist at Analyst1, in his Ransomware Diaries collection, for which he maintained frequent contacts with LockbitSupp and a few of LockBit’s associates.
DiMaggio discovered inconsistencies throughout totally different interactions with LockbitSupp and assessed that three different people, together with the group’s present chief, had run the persona.
LockBit’s Origins
LockBit is a infamous ransomware variant and, at instances, has been probably the most deployed worldwide, indiscriminately concentrating on organizations from all business verticals.
Right here’s a graphic from our upcoming Lively Adversary Report , displaying exactly how, as seen by the Sophos X-Ops Incident Response group, Conti in 2021 and LockBit in 2023 represented actually double the amount of infections of the closest “opponents .” 2/11 pic.twitter.com/LDFv5qJ0i3
— Sophos X-Ops (@SophosXOps) February 21, 2024
The group emerged in 2019 and the LockBit named ransomware was first seen on a Russian-language based mostly cybercrime boards in January 2020 and it listed its first sufferer to its leak website in September 2020.
Due to its hyperlinks with Russian-language boards, many safety analysts imagine the gang was based mostly in, or at the least closely linked with, Russia.
As a part of Operation Cronos, the US imposed sanctions on the group’s associates chargeable for ransomware assaults, together with two Russian nationals. One, Ivan Gennadievich Kondratiev, was generally recognized within the cybercriminal world as “Bassterlord” and “Fisheye.”
The group operates a ransomware-as-a-service (RaaS) mannequin, with a community of associates that leverage LockBit’s malware to conduct cyber-attacks.
Following Operation Cronos, the UK’s Nationwide Crime Company (NCA) stated it gained a wealth of knowledge on the group’s associates, revealing 187 distinct entities.
This quantity might be larger or decrease as some associates would possibly use a number of accounts and others may need been inactive or solely lively for a brief time frame.
The US authorities provides a $15m bounty for anybody offering crucial data on the group and its directors.
LockBit’s Techniques and Operations
LockBit ransomware has advanced since its inception in 2019. Safety consultants imagine the group has been operating the next ransomware variations:
- LockBit 1.0 was launched in January 2020 as “ABCD” ransomware
- LockBit 2.0 (LockBit Crimson) was launched in June 2021 along with StealBit, the group’s knowledge exfiltration instrument
- LockBit Linux was launched in October 2021 to contaminate Linux and VMWare ESXi techniques
- LockBit 3.0 (LockBit Black) was launched in March 2022 and leaked six months later by the group’s disgruntled developer, resulting in disruptions inside the RaaS construction
- LockBit Inexperienced was launched in January 2023 and promoted by LockbitSupp as being a serious new model – a incontrovertible fact that was later denied by many safety professionals, who discovered it was a rebranded model of a Conti encryptor
The most recent ‘actual’ model of the ransomware, LockBit 3.0, aimed to be a extra modular and evasive than earlier variations.
LockBit 3.0 proved difficult for safety analysts and automatic protection techniques as a consequence of its encrypted executables, random passwords and undocumented Home windows capabilities.
General, LockBit saved its providing easy with a point-and-click interface, which might enchantment to a variety of associates with various levels of technical information.
Typical techniques included double extortion, the place knowledge from a sufferer group could be encrypted and stolen.
Nonetheless, due to LockBit’s affiliate working mannequin the techniques, methods and procedures (TTPs) of the ransomware gang have assorted extensively.
A cybersecurity advisory by the US Cybersecurity and Infrastructure Safety Company printed in June 2023 particulars the technical data behind LockBits operations.
Curiously, the RaaS gang additionally engaged in publicity-generating actions and stunts, corresponding to paying folks to get LockBit tattoos, which, since Operation Cronos, has turn into a viral meme within the cybersecurity world.
How LockBit Leveraged Cryptocurrency
Legislation enforcement businesses behind Operation Cronos partnered with cryptocurrency transaction evaluation agency Chainalysis to grasp the teams funds.
They discovered 30,000 Bitcoin addresses linked to LockBit, with over 500 Bitcoin addresses lively, which have obtained over $120m. The evaluation additionally reveals over $114m stays unspent.

It’s possible that the LockBit ransomware group is chargeable for multi-billion {dollars}’ value of theft internationally.
LockBit has Hacked A whole bunch of Sufferer Organizations
LockBit used its leak website to publish the small print of its victims and the ransom calls for related to the hack. The huge variety of organizations the group hacked made it probably the most infamous ransomware gang of 2023. LockBit listed 275 victims on knowledge leak websites between October and December 2023.
In a webinar broadcast on February 21, Recorded Future estimated the entire variety of LockBit victims was 2300, with round 57% based mostly within the US.
“This estimate relies on our knowledge; the fact is probably going a lot larger,” stated Alexander Leslie, a risk intelligence analyst at Recorded Future.
Excessive-profile victims embrace the UK’s Royal Mail, from which LockBit demanded a £66m ransom.
The LockBit hacking group additionally claimed duty for a cyber-attack in opposition to the multinational automotive group Continental in November 2022.
Associates of the group additionally focused Toronto’s Hospital for Sick Youngsters (SickKids) on the night of December 18, 2022. This assault supposedly contravened the group’s coverage on targets and a decryption key was handed over freed from cost.
The Housing Authority of the Metropolis of Los Angeles (HACLA) issued a public discover outlining the impression of a ransomware breach that passed off in early 2023. The suspected culprits had been LockBit.
Is There a Decryptor for LockBit?
Sure. As a part of the February 19 Operation Cronos, legislation enforcement confirmed they’ve entry to round 1000 of LockBit’s decryption keys.
This has allowed the legislation enforcement organizations concerned in Operation Cronos to develop new decryption instruments designed to recuperate recordsdata encrypted by the LockBit ransomware.
“Legislation enforcement could possibly help you to decrypt your LockBit encrypted recordsdata,” reads a message displayed on LockBit’s knowledge leak website.
In a public assertion, the US Division of Justice (DoJ) commented: “Starting immediately, victims focused by this malware are inspired to contact the FBI at https://lockbitvictims.ic3.gov/ to allow legislation enforcement to find out whether or not affected techniques will be efficiently decrypted.”
These options have additionally been made accessible without cost on the ‘No Extra Ransom’ portal, accessible in 37 languages.
It’s In all probability the Finish of LockBit…As We Know It
Many cybersecurity consultants imagine that, regardless of Operation Cronos’ success, people behind LockBit will come again in a single kind or one other if they aren’t all arrested.
Some suppose they’ll develop one other toolset, whereas others imagine they’ll reorganize below a brand new identify, similar to Conti members have finished earlier than them.
Nonetheless, Yelisey Bohuslavskiy, co-founder of risk intelligence agency RedSense, believes that is the tip of LockBit as we all know it.
In a three-year investigation carried out by RedSense, researchers noticed that LockBit was functioning in a three-layered construction:
- Floor Degree: LockBit is a big and established RaaS comprised of dozens of associates, which chaotically assault random networks in a “spray and pray” trend and fail round 99% of the time
- LockbitSupp Degree: LockBit is counting on a low-capability core group, with pretend claims, fixed affiliate scams and LockbitSupp serving as a mere distraction for precise operations
- Large Recreation Degree: “Ghost teams” – i.e., teams of expert associates with excessive capabilities however who switch them to a different model
“The ‘Ghost Group’ mannequin is one thing between a company ransomware construction like Conti and a traditional RaaS like Maze,” stated the RedSense report.
One among LockBit’s most dependable ‘Ghost teams’ was named Zeon and it was comprised of former Conti hackers. The identical members had been additionally beforehand concerned with the Ryuk ransomware group, Zeon has additionally outsourced its abilities to the Akira ransomware group.
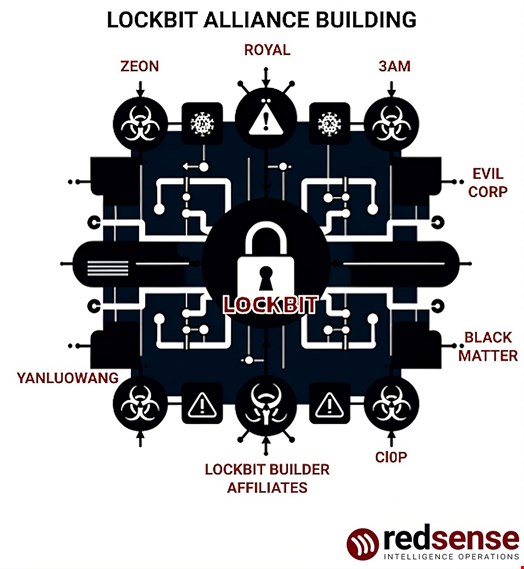
In keeping with RedSense, LockBit was closely reliant on the high-tier professionals like Zeon. It’s assumed that they’ll develop bored with the amateurism of the LockBit admins and can transfer on. They might maybe have extra substantial involvement with Akira or BlackSuit, a rebrand of the Royal ransomware group.
A number of the RedSense findings, particularly that an ex-Conti member was concerned in LockBit’s high-end operations, correlate with a report printed by one other risk intelligence agency, Prodaft, on February 22.
Prodaft took half in Operation Cronos.
Throughout its LockBit takedown webinar, Recorded Future estimated three potential situations for the way forward for LockBit:
- The ‘Retire’ situation, through which the LockBit core operational group would stop to become involved in unlawful cyber actions
- The ‘Return’ situation, through which LockBit admins would construct new infrastructure and attempt to develop a brand new model of their toolset, just like what the REvil ransomware group has finished up to now
- The ‘Little LockBits’ situation, through which LockBit members would be part of different current ransomware teams or kind new ones, similar to Conti members did
Recorded Future’s Leslie and his colleagues Allan Liska and Dmitry Smilyanets stated they imagine the final situation to be the almost definitely.
Nonetheless, Japanese cybersecurity agency Development Micro, which additionally took half in Operation Cronos, launched a report on February 22 displaying that the LockBit group was already attempting to develop a brand new ransomware model.
Conclusion
Operation Cronos and the legislation enforcement takedown of the LockBit ransomware gang has been hailed as a hit for the cybersecurity world.
LockBit ransomware has certainly been one of the vital prolific and damaging technique of cyber-attack globally.
Whereas the long run stays unsure for members of the gang, and lots of within the cybersecurity neighborhood are hoping for extra arrests, it’s clear that this refined community of cybercriminals has been stopped of their tracks. For now.










