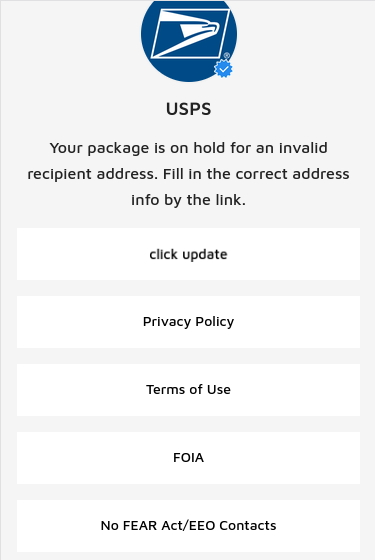
The pretend USPS phishing web page.
Latest weeks have seen a large uptick within the variety of phishing scams focusing on U.S. Postal Service (USPS) prospects. Right here’s a take a look at an intensive SMS phishing operation that tries to steal private and monetary knowledge by spoofing the USPS, in addition to postal companies in at the least a dozen different nations worldwide.
KrebsOnSecurity just lately heard from a reader who obtained an SMS purporting to have been despatched by the USPS, saying there was an issue with a bundle destined for the reader’s tackle. Clicking the hyperlink within the textual content message brings one to the area usps.informedtrck[.]com.
The touchdown web page generated by the phishing hyperlink contains the USPS emblem, and says “Your bundle is on maintain for an invalid recipient tackle. Fill within the appropriate tackle information by the hyperlink.” Under that message is a “Click on replace” button that takes the customer to a web page that asks for extra data.
The remaining buttons on the phishing web page all hyperlink to the true USPS.com web site. After gathering your tackle data, the pretend USPS web site goes on to request extra private and monetary knowledge.
This phishing area was just lately registered and its WHOIS possession information are principally nonexistent. Nevertheless, we are able to discover some compelling clues in regards to the extent of this operation by loading the phishing web page in Developer Instruments, a set of debugging options constructed into Firefox, Chrome and Safari that enable one to intently examine a webpage’s code and operations.
Try the underside portion of the screenshot beneath, and also you’ll discover that this phishing web site fails to load some exterior sources, together with a picture from a hyperlink referred to as fly.linkcdn[.]to.
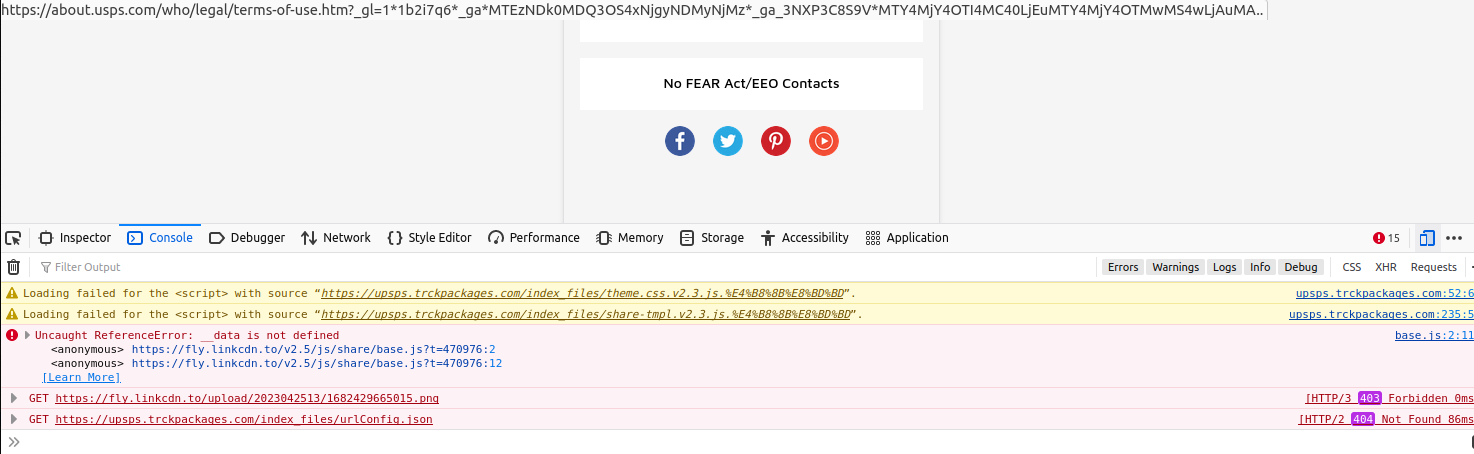
Click on the picture to enlarge.
A search on this area on the always-useful URLscan.io exhibits that fly.linkcdn[.]to is tied to a slew of USPS-themed phishing domains. Listed here are just some of these domains (hyperlinks defanged to stop unintentional clicking):
usps.receivepost[.]com
usps.informedtrck[.]com
usps.trckspost[.]com
postreceive[.]com
usps.trckpackages[.]com
usps.infortrck[.]com
usps.quicktpos[.]com
usps.postreceive].]com
usps.revepost[.]com
trackingusps.infortrck[.]com
usps.receivepost[.]com
usps.trckmybusi[.]com
postreceive[.]com
tackingpos[.]com
usps.trckstamp[.]com
usa-usps[.]store
usps.infortrck[.]com
unlistedstampreceive[.]com
usps.stampreceive[.]com
usps.stamppos[.]com
usps.stampspos[.]com
usps.trckmypost[.]com
usps.trckintern[.]com
usps.tackingpos[.]com
usps.posinformed[.]com
As we are able to see within the screenshot beneath, the developer instruments console for informedtrck[.]com complains that the location is unable to load a Google Analytics code — UA-80133954-3 — which apparently was rejected for pointing to an invalid area.
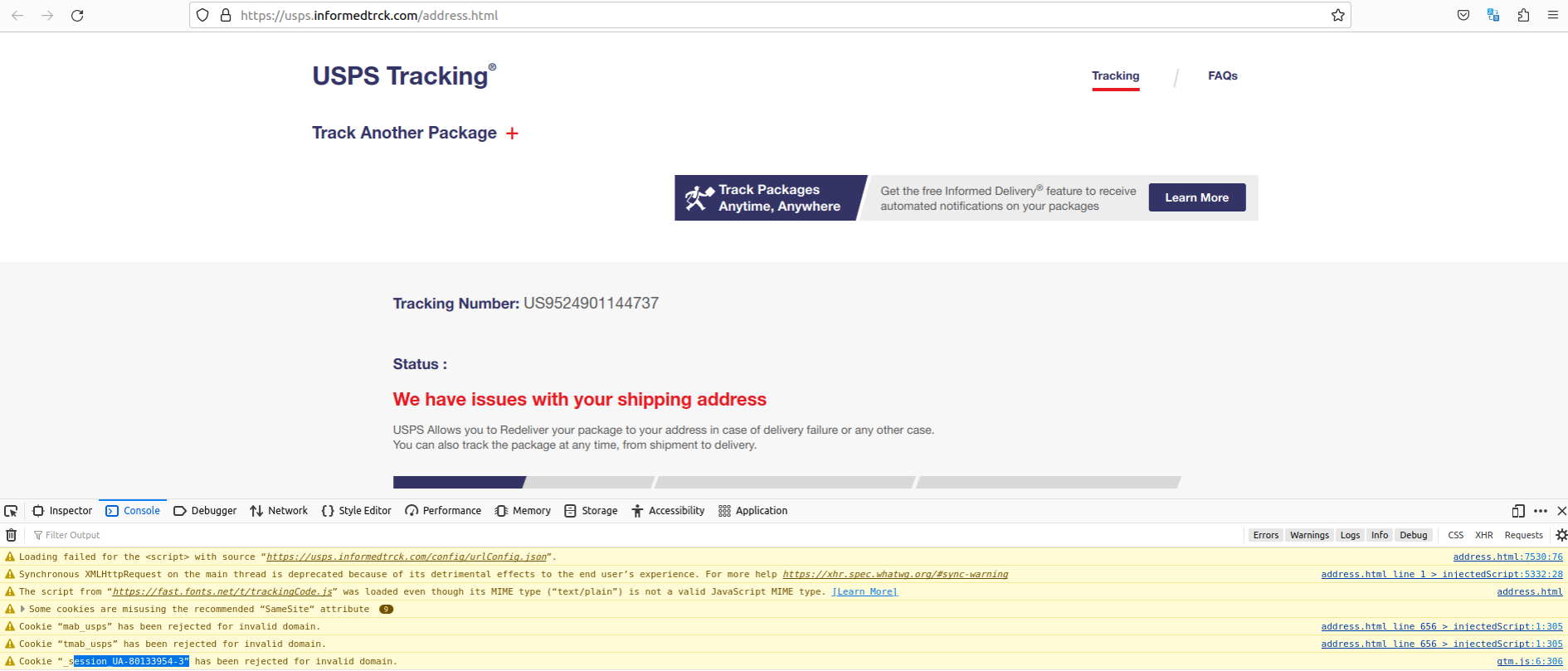
Discover the highlighted Google Analytics code uncovered by a defective Javascript component on the phishing web site. Click on to enlarge. That code really belongs to the USPS.
The legitimate area for that Google Analytics code is the official usps.com web site. In line with dnslytics.com, that very same analytics code has proven up on at the least six different practically equivalent USPS phishing pages relationship again practically as a few years, together with onlineuspsexpress[.]com, which DomainTools.com says was registered approach again in September 2018 to a person in Nigeria.
A unique area with that very same Google Analytics code that was registered in 2021 is peraltansepeda[.]com, which archive.org exhibits was working an analogous set of phishing pages focusing on USPS customers. DomainTools.com signifies this web site title was registered by phishers primarily based in Indonesia.
DomainTools says the above-mentioned USPS phishing area stamppos[.]com was registered in 2022 through Singapore-based Alibaba.com, however the registrant metropolis and state listed for that area says “Georgia, AL,” which isn’t an actual location.
Alas, working a seek for domains registered by way of Alibaba to anybody claiming to reside in Georgia, AL reveals practically 300 latest postal phishing domains ending in “.high.” These domains are both administrative domains obscured by a password-protected login web page, or are .high domains phishing prospects of the USPS in addition to postal companies serving different nations.
These different nations embody the Australia Publish, An Publish (Eire), Correos.es (Spain), the Costa Rican submit, the Chilean Publish, the Mexican Postal Service, Poste Italiane (Italy), PostNL (Netherlands), PostNord (Denmark, Norway and Sweden), and Posti (Finland). A whole listing of those domains is accessible right here (PDF).
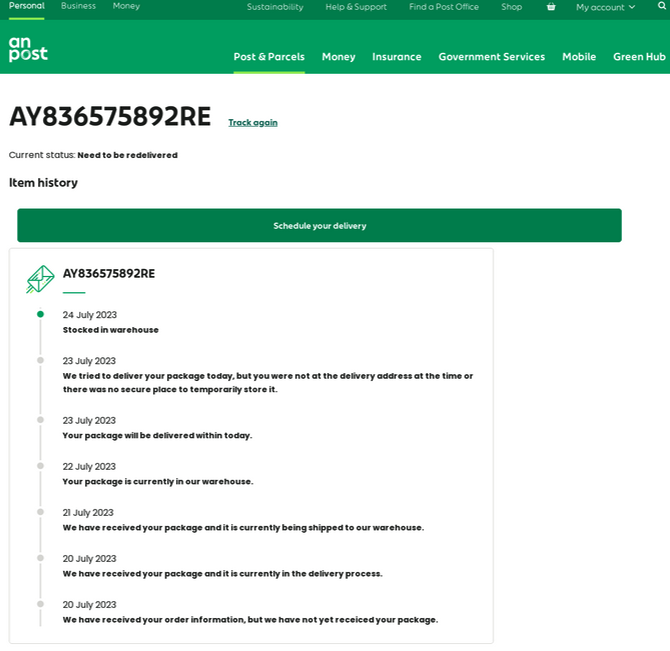
A phishing web page focusing on An Publish, the state-owned supplier of postal companies in Eire.
The Georgia, AL domains at Alibaba additionally embody a number of that spoof websites claiming to gather excellent highway toll charges and fines from the governments of Australia, New Zealand and Singapore.
In the meantime, researchers at DomainTools just lately revealed a report on an apparently unrelated however equally sprawling SMS-based phishing marketing campaign focusing on USPS prospects that seems to be the work of cybercriminals primarily based in Iran.
SMS-based phishing scams are likely to forged a large internet and sometimes spoof entities which might be broadly utilized by the native inhabitants, and few manufacturers are going to have extra family attain than home mail companies. In June, the United Parcel Service (UPS) disclosed that fraudsters had been abusing a web based cargo monitoring device in Canada to ship extremely focused SMS phishing messages that spoofed the UPS and different manufacturers.
With the vacation procuring season practically upon us, now is a superb time to remind household and mates about the most effective recommendation to sidestep phishing scams: Keep away from clicking on hyperlinks or attachments that arrive unbidden in emails, textual content messages and different mediums. Most phishing scams invoke a temporal component that warns of adverse penalties must you fail to reply or act shortly.
For those who’re not sure whether or not the message is professional, take a deep breath and go to the location or service in query manually — ideally, utilizing a browser bookmark in order to keep away from potential typosquatting websites.