Ransomware assaults skyrocketed final month in accordance with the brand new month-to-month cybersecurity report by NCC Group. New risk group Cl0p is behind the rise because it exploited vulnerabilities in GoAnywhere file switch supervisor.

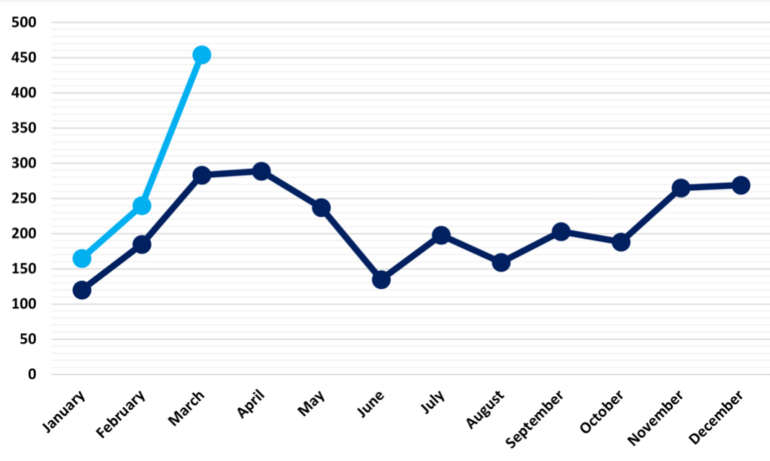
Ransomware assaults have spiked, in accordance with the NCC Group’s International Menace Intelligence Group. In its month-to-month risk report, NCC Group reported a 91% improve in ransomware assaults in March versus February and a 62% improve versus the month final 12 months — the best variety of month-to-month ransomware assaults the group has ever measured (Determine A).
Determine A
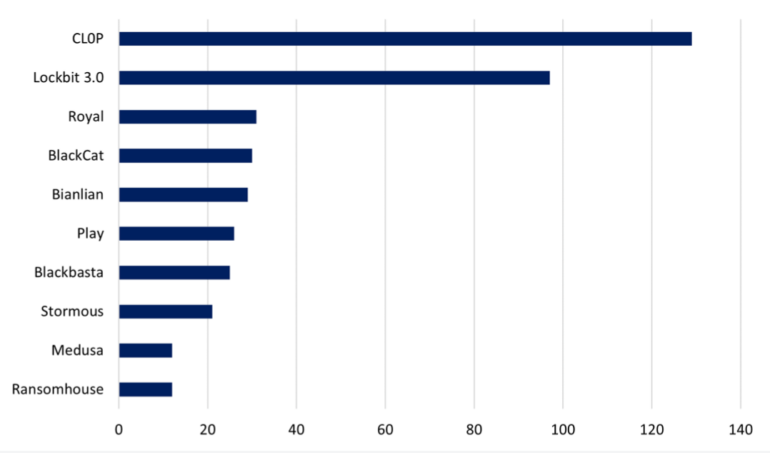
Ransomware-as-a-Service supplier Cl0p, essentially the most energetic risk actor, accounted for 28% of all March victims. NCC Group mentioned additionally it is the primary time Cl0p has been the highest RaaS for cybercriminal teams.
Cl0p, a Russian linked entity specializing in double extortion, exfiltrates knowledge then threatens to launch it if ransom isn’t forthcoming. The hacking group has been round since 2019, when it efficiently attacked main firms like Hitachi, Shell and several other different enterprises.
LockBit 3.0 got here in second, accounting for 21% of assaults. NCC Group mentioned March 2023 was the second month since September 2021 during which LockBit had not been the highest ransomware risk actor. The group’s victims declined 25% from February, per NCC.
SEE: The Royal rip-off — risk actors promise difficult 2023
The non-aligned assault group Royal, which appeared in September final 12 months focusing on the healthcare sector, was the third most energetic attacker with a 106% improve in assaults in March versus February (Determine B).
Determine B
Cl0p accessed GoAnywhere MFT vulnerability to assault organizations
NCC Group mentioned the rise in assaults by CL0p mirrored its exploitation of a vulnerability in Fortra’s GoAnywhere managed file switch utilized by 1000’s of organizations all over the world, inflicting large-scale disruption.
As reported, Fortra discovered the zero-day vulnerability in January and informed solely its authenticated customers, but it surely was not assigned a CVE ID on Mitre or patched till early February.
Shields up for organizations utilizing GoAnywhere MFT
Based on NCC Group, there are viable techniques for safeguarding towards assaults by Cl0p and different exploiters of third-party instruments and providers:
- Restrict publicity on ports 8000 and 8001, the place the GoAnywhere MFT admin panel is located.
- After logging into GoAnywhere, comply with the steps outlined within the GoAnywhere safety advisory.
- Set up patch 7.1.2.
- Overview admin person accounts for suspicious exercise, with a particular deal with accounts created by techniques, suspicious or atypical timing of account creation or disabled super-users creating a number of accounts.
- Contact GoAnywhere MFT help immediately by way of portal, e mail or telephone to obtain extra help.
SEE: Finish-to-end encrypted e mail platforms can thwart assaults.
North American, industrial sector are double bullseyes
Areas
Repeating tendencies from final month’s evaluation, North America was the goal of just about half of March’s exercise, with 221 victims (48%). Europe (28%) and Asia (13%) adopted with 126 and 59 assaults respectively.
Sectors
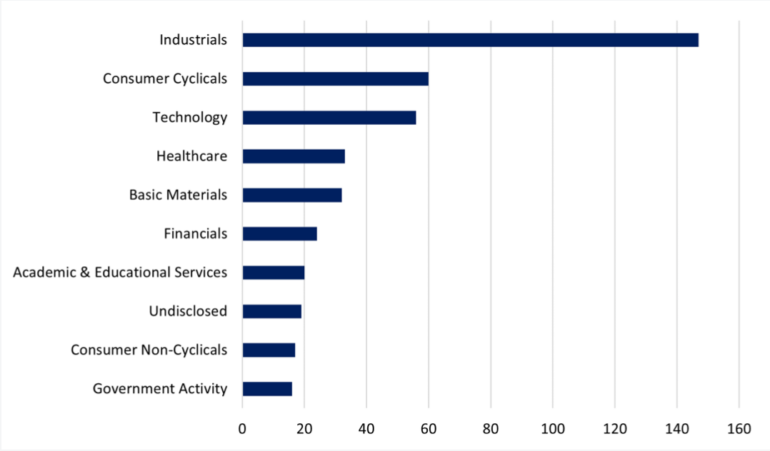
Industrials had been by far essentially the most focused sector final month with 147 strikes, accounting for 32% of assaults. Client Cyclicals was the second-most focused with 60 assaults (13%), adopted by Expertise, regaining third place with 56 assaults (12%).
Within the industrial sector:
- The variety of victims in skilled and industrial providers elevated 120%.
- Assaults on equipment, instruments, heavy automobiles, trains and ships elevated 127%.
- Assaults on onstruction and engineering sectors elevated 16% (Determine C).
Determine C
Tempo of ransomware assaults more likely to stay brisk
Matt Hull, international head of risk intelligence at NCC Group, mentioned the massive surge in ransomware assaults final month is more likely to be par for the course this 12 months. “If [Cl0p’s] operations stay constant, we will count on them to stay a prevalent risk all year long. We’re protecting an in depth eye on the actor because it evolves,” he mentioned.
The corporate beforehand reported the best variety of ransomware instances in January and February than prior to now 3 years.
Tips on how to defend towards accelerating ransomware threats
With this 12 months more likely to function elevated assaults, NCC Group suggests:
- Know if a newly introduced vulnerability will have an effect on your group, in addition to know your techniques and configurations.
- Patch usually. The truth that Log4j continues to be energetic reveals how un-patched CVEs supply an open door.
- Block frequent types of entry: Create a plan for learn how to rapidly disable at-risk techniques like VPNs or RDP.
- Look into endpoint safety packages to detect exploits and malware.
- Create backups offline and offsite, past the attain of attackers.
- Be cognizant: Attackers return to the identical sufferer after they know a gap has not been patched.
If attacked and the outbreak is remoted and stopped, each hint of their intrusion, malware, instruments and strategies of entry have to be eliminated, assessed and acted upon to keep away from being attacked once more.










