Relating to ransomware assaults, some knowledge is extra treasured to ransomware teams as others. A brand new analysis research by Rapid7, Ache Factors: Ransomware Knowledge Disclosure Tendencies, supplies perception on the information that ransomware teams worth and the way they use knowledge to use strain.
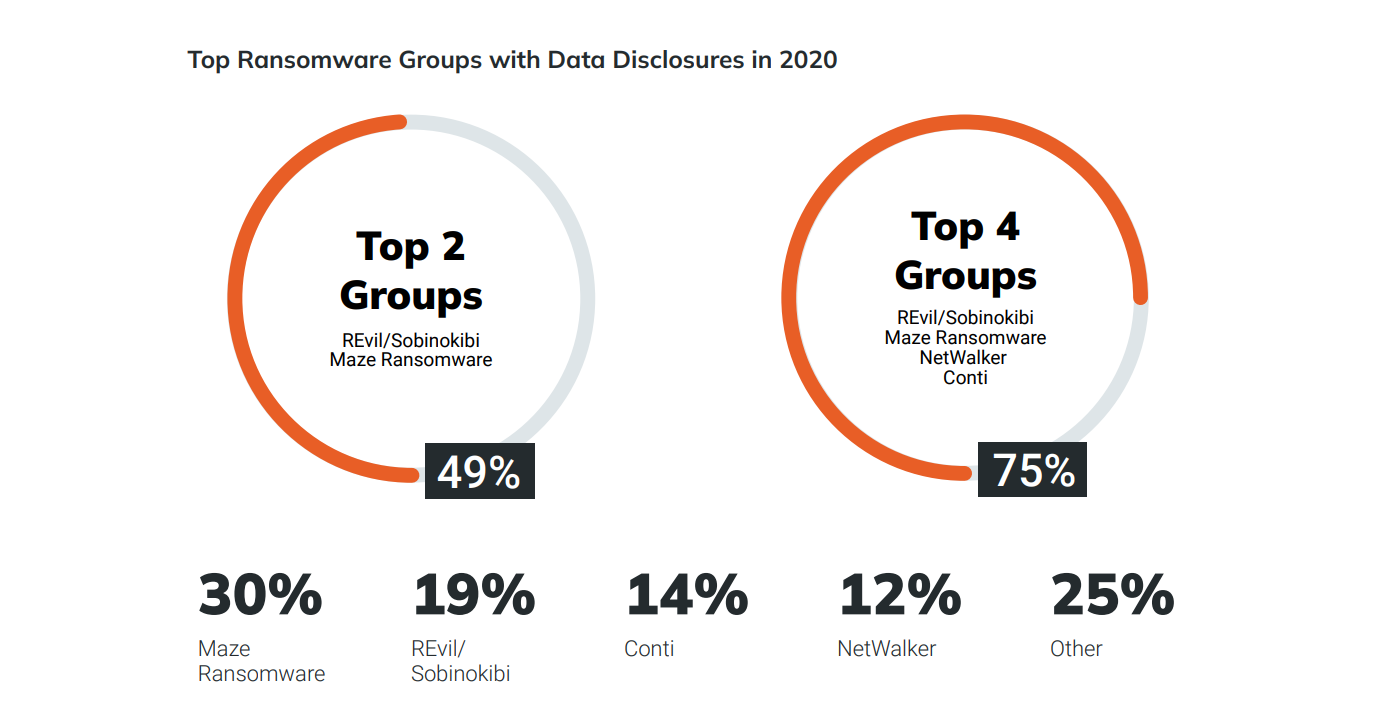
Double extortion assaults have elevated in recent times. Conventional ransomware assaults encrypt knowledge on attacked techniques to extort cash from firms and people. The rise of countermeasures, together with using backups, have lowered the effectiveness of conventional ransomware assaults.
If knowledge backups can be found, firms may use these to revive the information with out having to pay ransom. With out extra leverage, ransomware teams could be left empty handed after the assault.
Double extortion assaults mix the encryption stage with one other stage, which occurs earlier than knowledge is encrypted. Teams analyze information and paperwork on the attacked community to steal knowledge. Knowledge remains to be held hostage, as it’s encrypted within the second stage, however the stolen knowledge could also be used as leverage in ransomware negotiations. Ransomware teams might threaten to launch the information to the general public, or promote it to events. If negotiations fail, knowledge could also be bought on the darkish net.
Ransomware research are launched regularly. We now have lined two right here on Ghacks up to now two months alone. The primary, confirms that ransomware assaults and ransom funds are growing. The second, that the ransom cost is marginal when in comparison with the general prices of ransomware assaults.
Ransomware Knowledge Disclosure
Rapid7 analyzed 161 knowledge disclosures between April 2020 and February 2022. Many ransomware assaults occur over the course of days, weeks and even months. The time span provides attackers time to gather and exfiltrate knowledge from compromised networks earlier than working encryption duties.
Some knowledge is extra priceless to ransomware teams than others. Knowledge that could be used as leverage, as an example affected person information, monetary paperwork, or mental property information, are extra priceless on common than different forms of knowledge that attackers might uncover throughout assaults.
The extracted knowledge is utilized in numerous methods by ransomware teams. Moreover apparent makes use of to realize even deeper entry to the community of the group, exfiltrated knowledge might also be used as leverage, or bought on darkish net markets if ransomware negotiations fail.
The additional time that attackers spend on a community provides organizations a chance to detect the compromise earlier than knowledge is totally encrypted.
Ransomware knowledge disclosures occur in two phases:
- Stage 1: A pattern of the stolen knowledge is introduced to the group; that is achieved to enhance credibility and as leverage, as additional knowledge disclosures might show damaging to the group. The information is offered to the group solely normally, however it might even be printed publicly on the Web.
- Stage 2: Knowledge is bought or printed, if negotiations with the sufferer have been fruitless.
Rapid7 notes within the evaluation that knowledge disclosures are indicators of common ransomware tendencies. Firm researchers have been in a position to decide the next primarily based on the evaluation of the 161 knowledge disclosures:
- Most typical forms of knowledge attackers disclosed
- How knowledge disclosures differ between industries and risk actor teams.
- Present ransomware market share amongst risk actors.
Knowledge Units in Ransomware Knowledge Disclosures
Not all knowledge is of equal significance to organizations, and knowledge disclosures might differ extensively between sectors. Most thought after have been buyer & affected person knowledge in monetary companies assaults, finance and accounting data in healthcare and pharmaceutical assaults, and worker PII & HR in Monetary companies.
Notably, mental property knowledge was utilized in 43% of pharmaceutical disclosures. For all industries, finance & accounting data was used essentially the most, adopted by buyer & affected person knowledge, and worker PII & HR knowledge.
Buyer knowledge disclosures dominated the Monetary Companies sector, adopted by worker PII & HR knowledge, and inside finance and accounting paperwork. The give attention to buyer knowledge means that buyer knowledge is commonly extra priceless to ransomware teams than different forms of knowledge. Rapid7 suggests that the specter of releasing buyer knowledge is commonly highly effective, because it may have an effect on the group’s public notion.
Inner finance and accounting information have been disclosed in healthcare and pharmaceutical essentially the most, and never in monetary sector disclosures. Buyer and affected person knowledge was disclosed in additional than 50% of all instances, however not almost as a lot as in monetary companies.
The excessive frequency with which Buyer & Affected person Knowledge seems in these disclosures recommend attackers purpose to exert better strain on victims with: a) the extra extreme authorized and regulatory penalties of affected person knowledge breaches for hospitals and different healthcare suppliers and; b) the better utility of the extra detailed and granular affected person knowledge units to criminals for id theft and different types of fraud.
Disclosures from the pharmaceutical sector had a excessive frequency of mental property information. Pharmaceutical firms “rely closely on massive mental property investments”, which makes these knowledge discloses priceless to risk actors. Mental property disclosures have been included in simply 12% of disclosures of all samples.
Menace Actor Group Tendencies
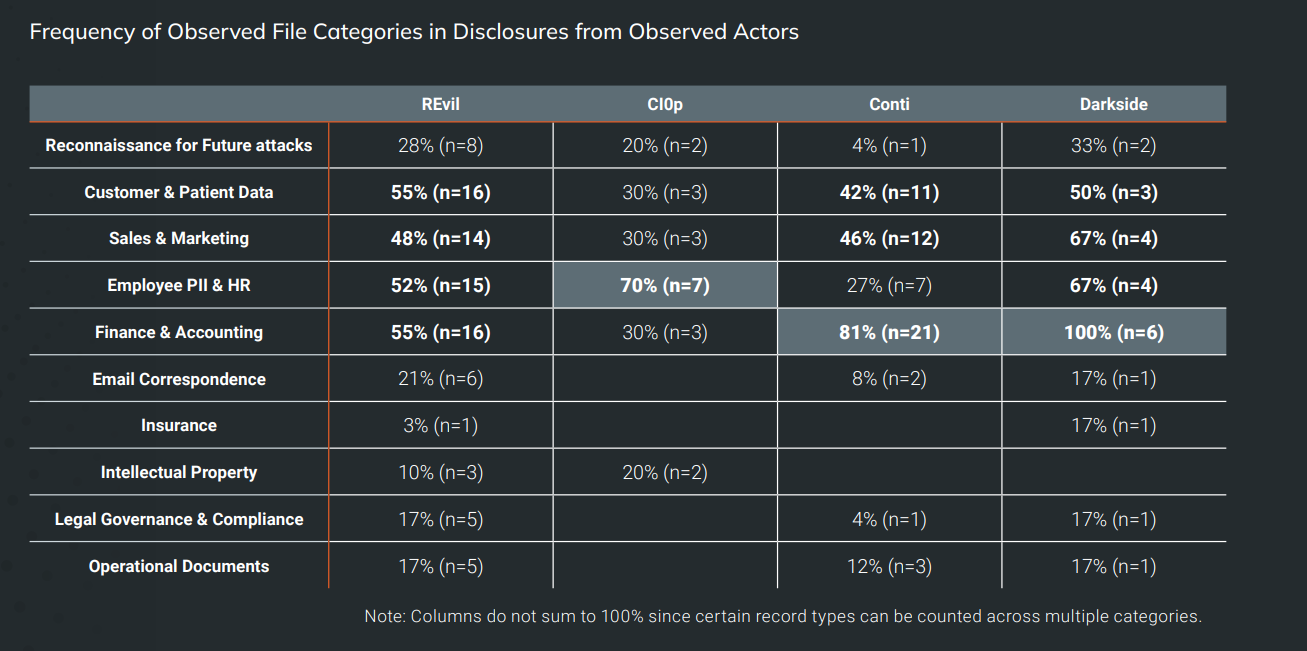
Menace Actor Teams use completely different methods on the subject of double extortion assaults. A number of the variations could also be defined by the information that the attackers found throughout assaults. If a sure kind of knowledge will not be discovered or cannot be exfiltrated, different knowledge might have been used as an alternative as leverage.
The 4 principal teams of the evaluation used completely different knowledge sorts in disclosures. Finance & account knowledge was disclosed 100% by the group Darkside, however solely 30% of the time by CI0p. Equally, Darkside disclosed gross sales & advertising, and worker Pii & HR knowledge 67% of the time, whereas different teams solely 27% or 30% of the time.
Suggestions and recommendations by Rapid7
Increasingly organizations use backups to counter conventional ransomware assaults. Backups assist, however they aren’t 100% efficient on their very own on the subject of double extortion assaults. To counter double distortion assaults, Rapdi7 means that organizations use file encryption, phase firm networks, and render “any information unreadable to unauthorized eyes”.
The report might help organizations in figuring out excessive precedence property to raised defend these towards potential ransomware assaults.
Organizations, lastly, might also use the findings of the report in preparations to “anticipate what forms of
information are most certainly to look”.
Now You: how do you defend your techniques towards ransomware assaults? (by way of Rapdi7)
Abstract

Article Identify
Rapid7 analysis reveals which knowledge ransomware teams search and use for leverage
Description
A brand new analysis research by Rapid7 supplies perception on the information that ransomware teams worth and the way they use knowledge to use strain.
Writer
Martin Brinkmann
Writer
Ghacks Expertise Information
Brand

Commercial








/cdn.vox-cdn.com/uploads/chorus_asset/file/25841912/Silo_Photo_021008.jpg)

