Qualys report appears to be like at how misconfiguration points on cloud service suppliers assist attackers acquire entry.

Cloud misconfiguration — incorrect management settings utilized to each {hardware} and software program components within the cloud — are risk vectors that amplify the chance of knowledge breaches. A brand new report from cloud safety vendor Qualys, authored by Travis Smith, vice chairman of the corporate’s Risk Analysis Unit lifts the lid on danger elements for 3 main cloud service suppliers.
In regards to the report
Smith wrote that Qualys researchers, analyzing misconfiguration points at Amazon Net Companies, Microsoft Azure and Google Cloud Platform, discovered that inside Azure, 99% of the disks are both not encrypted or aren’t utilizing customer-managed keys that give customers management of encryption keys that shield knowledge in software program as a service functions.
The research, which reviewed encryption, id and entry administration and failures to observe external-facing property examined dangers to unauthorized entry on account of:
- The complexity of cloud environments
- Lack of know-how in maintaining with evolving applied sciences
- Insecure settings and permissions attributable to human errors
- Speedy deployment compromising safety implementation measures
- Lack of management and visibility of cloud-resident unencrypted or delicate knowledge because of the dynamic nature of cloud environments
Smith wrote that the corporate’s reachers discovered that 85% of the keys aren’t rotated, that means automated key rotation isn’t enabled. Amazon gives automated key rotation — producing new cryptographic materials — on a 365 day cycle for keys.
Qualys additionally reported that in GCP environments, 97.5% of digital machine disks for vital digital machines lack encryption utilizing customer-supplied encryption keys.
Bounce to:
Id and Entry Administration
Qualys discovered poor implementation ranges of IAM in all three main suppliers:
- Multifactor authentication: AWS isn’t enabled for 44% of IAM customers with console passwords. IAM Entry Analyzer isn’t enabled in 96% of the accounts scanned by Qualys.
- In Azure, scans for enabling authentication and configuring consumer certificates inside Azure App Service fail 97% of the time.
Publicity of external-facing property from leaky S3 buckets
Qualys famous {that a} widespread mistake by customers throughout the three platforms is public publicity of knowledge:
- Qualys reported 31% of S3 buckets are publicly accessible.
- The misconfiguration of leaving public community entry enabled was seen in 75% of the Azure databases.
SEE: What’s cloud safety?
Middle for Web Safety work gives insights to remediation
Suggestions by the agency included reviewing analysis by the Middle for Web Safety together with work Qualys participated in: mapping of particular person controls to the MITRE ATT&CK techniques and strategies.
Qualys contributed to creating these CIS benchmarks for AWS, Azure and GCP. The benchmarks will assist provide some useful perception and context for defenders to higher prioritize the a whole bunch of hardening controls out there in cloud environments.
Qualys additionally checked out how companies are deploying controls to harden their cloud postures throughout the three main platforms, noting that privilege escalation (96.03%), preliminary entry (84.97%) and discovery (84.97%) are passing on the highest charges.
Efforts to manage assaults early are serving to to ameliorate extra dangerous penalties additional alongside the the kill chain:
- Affect handed at solely 13.67%
- Exfiltration at solely 3.70%.
- Exploitation of public dealing with apps handed at solely 28.54%.
- Exploitation of distant companies, at solely 17.92%, are failing at excessive charges.
- Useful resource hijacking is passing at simply 22.83%.
Smith wrote that since crypto mining malware is a risk to cloud environments, organizations ought to think about mitigating such controls to scale back their organizational danger within the cloud.
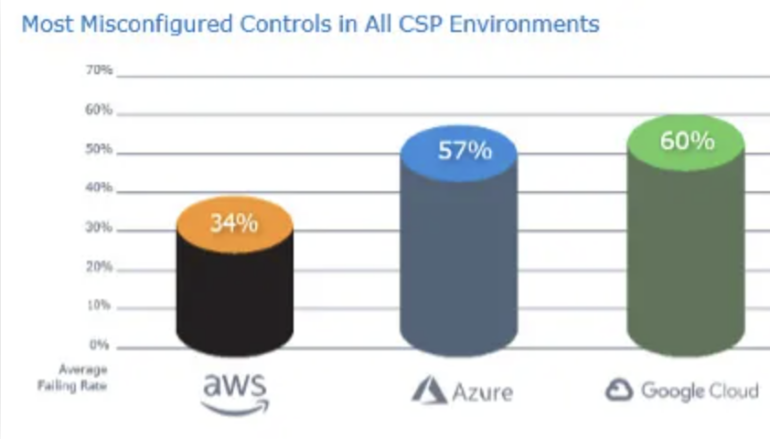
“The lesson from these knowledge factors is that nearly each group wants to higher monitor cloud configurations,” mentioned Smith, including that scans for CIS controls failed 34% of the time for AWS, 57% for Microsoft Azure and 60% for GCP (Determine A).
Determine A
“Even for those who imagine your cloud configurations are so as, the info tells us that not recurrently confirming standing is a dangerous wager. Scan the configurations typically and ensure the settings are appropriate. It takes only one slip-up to by chance open your group’s cloud to attackers,” wrote Smith.










