This confirms that subtle malign affect actions depend on developments in a goal nation to generate preliminary curiosity with out compromising the identification of the attacker. Maybe most apparently, our analysis additionally unexpectedly uncovered proof of malware being leveraged towards Fb customers.
Whereas it might appear counterintuitive that the IRA would hack customers that they’re attempting to affect with out being caught, the operational strategy right here was clear. They used click-fraud malware like FaceMusic to contaminate an initially gullible inhabitants, improve the visibility of troll farm content material utilized by IRA accounts, after which increase the attain of the affect operation to extra various social media populations. Given the main target in CEIO analysis on direct assaults on affect infrastructure like voting programs or social media platforms, this discovering is revelatory.
Seize, not kill: Operational utility feeds strategic worth of cyber-enabled affect operations
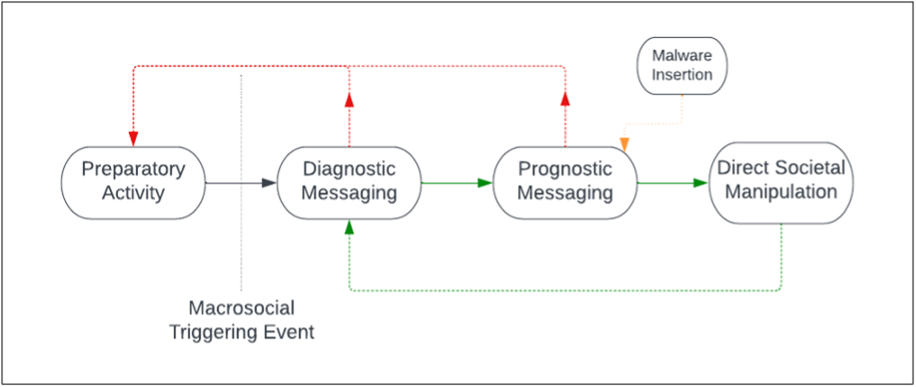
This analysis reveals a transparent lifecycle of CEIO actions that’s rooted in a sturdy understanding of the constraints going through affect operators. We’d consider this as a seize chain reasonably than the standard kill chain. Because the diagram beneath reveals, preparatory cyber exercise is essential within the growth of affect campaigns that may be the differentiator between tactical outcomes and strategic worth. After a belligerent just like the IRA establishes its preliminary social media footprint, it engages in a messaging marketing campaign that references home triggering occasions to interact and seize an preliminary inhabitants.
As with a lot social engineering, nevertheless, the first-mover precept with affect operations is to focus on gullible individuals to increase entry. Malware was the important thing to this aim, translating the prospects of the operation from one with restricted chance of great impression to one thing able to producing strategically significant manipulation of America’s info setting.
Christopher Whyte
This new tackle the usage of malware for affect operations not solely refocuses analysis and follow on CEIO, it additionally helps make sense of high-level empirical patterns within the marriage of cyber and affect efforts prior to now couple of years. As Microsoft and different know-how stakeholders have famous just lately, as an illustration, there’s a clear distinction in follow between Chinese language and Russian and Iranian menace actors on this house since 2020. Whereas Chinese language APTs have been linked to quite a few affect campaigns, the usage of malware or extra performative cyber actions alongside such efforts is minimal, notably towards Western targets. Against this, hackers backed by Moscow and Tehran constantly mix the strategies, to questionable outcomes.
A promising rationalization for this divergence lies within the character of Chinese language affect operations, which have typically centered on the West extra on issue-based manipulation of media and fewer on subverting sociopolitical programs. Such an strategy depends way more on distraction and on producing noise than it does on focused viewers results. As such, the utility of malware is much less.
Assessing cyber-enabled affect operations vulnerability
How ought to safety groups assess danger round cyber-enabled affect? The traditional reply to this query is just like assessing danger from geopolitical disaster. When contemplating the specter of manipulative or parallel cyber actions, vulnerability is most important for 2 varieties of actors. First, any group whose operation instantly ties into the perform of electoral processes is at heightened danger, whether or not that be social know-how firms or companies contracted to service voting infrastructure. Second, organizations that symbolize key social or political points are vulnerable to compromise as overseas menace actors search to leverage modern situations to provide performative ends.
This new analysis, nevertheless, means that danger lies way more problematically with workforces than with organizations themselves. Using malware towards susceptible populations on social media means that the CEIO menace is way more disaggregated than nationwide safety planners and trade safety groups would love.
Conventional hygiene controls like workforce coaching and constraints on the usage of private tools are clearly key to limiting organizational vulnerability to an infection. Extra usually, nevertheless, the notion of a seize chain emphasizes but once more the necessity for sociopolitical intelligence merchandise to be factored into safety analytics. Assessing CEIO danger means not solely understanding how geopolitical circumstance heightens firm vulnerability, it means understanding when personnel background and follow introduces new danger for organizational perform.










