Any firm that’s strategic might be focused for a similar sort of actions as this cyberattack. Observe these tricks to mitigate your organization’s threat to this cybersecurity risk.
Mandiant, a cybersecurity firm owned by Google, has revealed the main points of a 2022 cyberattack run by Russian risk actor Sandworm. The risk actor compromised a Ukrainian vital infrastructure group to govern its operational expertise setting, leading to an influence outage that coincided with mass missile strikes. Then, Sandworm tried to trigger extra disruption and take away all proof of its operation two days later by deploying and operating a variant of the CADDYWIPER malware.
This cyberattack is a placing instance of evolution in OT focusing on throughout wartime. Any firm that’s strategic to an attacker might be focused for a similar sort of actions.
Bounce to:
Timeline of this cybersecurity assault
It began round June 2022, when Sandworm gained entry to the IT setting of a Ukrainian vital infrastructure group. The risk actor deployed a recognized webshell, Neo-reGeorg, on an internet-facing server of the sufferer. A couple of month later, the group deployed GOGETTER, a recognized customized tunneling software program beforehand utilized by the group. The malware proxied communications between the focused system and the attacker’s command & management server and was made persistent in case of a server reboot.
The risk group then accessed the OT setting “by way of a hypervisor that hosted a Supervisory Management And Information Acquisition (SCADA) administration occasion for the sufferer’s substation setting,” in response to Mandiant researchers, who said the attacker probably had entry to the SCADA system for as much as three months.
On Oct. 10, 2022, the risk actor immediately executed MicroSCADA instructions on the system. The motion was finished by leveraging an ISO file, a digital CD-ROM that contained two scripts and one textual content file. The system was configured to permit inserted CD-ROMs to be launched robotically when inserted. These recordsdata had been used to execute a local MicroSCADA binary throughout the system, scilc.exe (Determine A).
Determine A
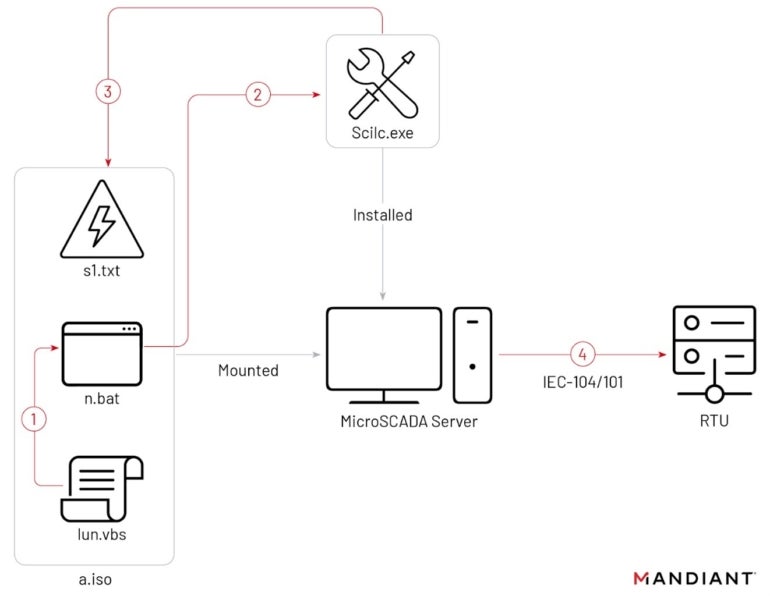
The reliable scilc.exe file from the MicroSCADA software program suite permits the execution of instructions written in Supervisory Management Implementation Language, that are typically text-based statements. Though Mandiant researchers had been unable to establish the SCIL instructions executed by Sandoworm, they imagine the instructions had been in all probability issued to open circuit breakers within the victims’ substation environments, subsequently switching off the sufferer’s substation.
In line with Mandiant, the assault resulted in an unscheduled energy outage.
Two days after this occasion, the risk actor put in a brand new variant of the CADDYWIPER malware within the goal’s setting to trigger additional disruption and probably take away forensic artifacts that would result in the invention of the operation. CADDYWIPER is wiping software program that has been beforehand used in opposition to Ukrainian targets by Sandworm and noticed in disruptive operations throughout a number of intrusions. Within the reported assault, the wiper didn’t attain the hypervisor of the SCADA digital machine that was compromised — which is uncommon, in response to Mandiant. The safety researchers conclude that this failure to take away proof “may outcome from an absence of coordination throughout totally different people or operational subteams concerned within the assault.”
SEE: Google Cloud’s Cybersecurity Traits to Watch in 2024 (TechRepublic)
Who’s Sandworm?
Sandworm is a harmful risk actor that has been attributed to Russia’s Foremost Intelligence Directorate of the Common Employees of the Armed Forces, Navy Unit 74455. The group has been lively since at the least 2009.
Six Unit 74455 officers related to Sandworm had been indicted in 2020 for a number of operations: Assaults in opposition to Ukrainian electrical corporations and authorities organizations; the focusing on of the 2017 French presidential marketing campaign, the 2018 Olympic Destroyer assault in opposition to the Olympic Video games, the 2018 operation in opposition to the Organisation for the Prohibition of Chemical Weapons and assaults in opposition to Georgia in 2018 and 2019.
Sandworm exposes Russia’s OT-oriented offensive cyber capabilities
Sandworm’s newest assault, along with earlier assaults originating from Russia such because the Industroyer incidents, which additionally focused OT, present efforts from Russia to streamline OT assault capabilities by way of simplified deployment options, in response to Mandiant. The researchers talked about “a continued funding in OT-oriented offensive cyber capabilities and total strategy to attacking IT techniques” (Determine B).
Determine B
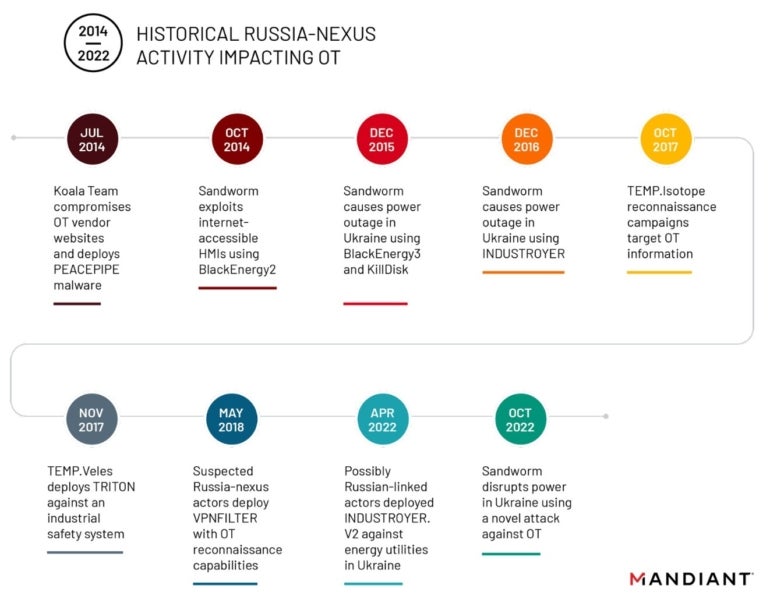
One important change within the strategies utilized by Sandworm is using native Dwelling Off The Land binary, aka LotLBin, which they now use for OT environments as a lot as for ordinary IT environments. This variation in all probability decreased the sources wanted for Sandworms assaults whereas making it more durable for defenders to detect the fraudulent exercise.
The timing of this Sandworm assault can be intriguing. As revealed by Mandiant, the attackers probably developed the disruptive functionality three weeks previous to the OT incident however might have been ready for a selected second to deploy the aptitude. “The eventual execution of the assault coincided with the beginning of a multi-day set of coordinated missile strikes on vital infrastructure throughout a number of Ukrainian cities, together with town wherein the sufferer was situated,” writes Mandiant.
Learn how to shield from this cybersecurity risk
Safety admins or IT execs ought to comply with these tricks to mitigate the chance of this cybersecurity risk.
- Harden MicroSCADA and different SCADA administration hosts. These techniques have to be updated and patched, and configured to require authentication and limit entry to solely obligatory customers for the techniques.
- Put community segmentation in place between the SCADA techniques and the remainder of the group’s community.
- Mixture log recordsdata to a central server and thoroughly analyze them continuously to detect attainable fraudulent use or alteration of the SCADA techniques.
- Monitor and analyze any file switch associated to the SCADA techniques. Any suspicious change in SCADA configuration or information must be investigated.
- Conduct common safety audits on SCADA techniques to establish attainable vulnerabilities or misconfigurations that would have an effect on the safety of the techniques.
- Do common backups to facilitate restoration in case of a safety incident or cyberattack on SCADA techniques.
Disclosure: I work for Pattern Micro, however the views expressed on this article are mine.










