It will be onerous to discover a net utility these days that doesn’t use third-party companies and APIs. Most of those require some sort of entry key, and which means a lot of secret (or at the very least delicate) credentials being saved and exchanged. What if somebody made a mistake and saved delicate information instantly within the supply of an online web page? Armed with a passive customized safety test in Invicti, we determined to see if may discover any circumstances of delicate information publicity in well-liked web sites.
What’s delicate information?
The definition of delicate information is dependent upon the kind and proprietor of this information. Generally, delicate information means any data that an individual, firm, or establishment doesn’t wish to expose publicly to keep away from the chance of misuse by malicious actors. For individuals, this could normally be personally identifiable data (PII), whereas for firms, it may very well be proprietary company data. Within the realm of net safety, delicate information contains secrets and techniques reminiscent of login credentials, entry tokens, and API keys.
For the aim of our analysis, we determined to outline delicate information as any sufficiently distinctive string that’s used to entry net sources. Examples of such delicate strings embody:
- Entry tokens
- API keys
- Connection strings
On this case, we are able to use the time period delicate information as a result of such keys should be secret and personal to stop safety points. For instance, exposing an API token might permit attackers to bypass entry controls or at the very least make entry simpler.
How one can scan for delicate information in public net belongings
We already know that builders sometimes hard-code passwords and different credentials into net pages and even go away them in feedback, so I had the concept of utilizing Invicti to jot down a customized safety test that may discover the commonest API keys and comparable tokens on well-liked web sites. We determined to test the Alexa high 10,000 websites and likewise study some information scraped from Pastebin as the preferred public paste website.
Invicti’s customized safety checks function permits you to lengthen the built-in vulnerability detection capabilities with customized scripts. You possibly can write energetic or passive scripts that specify assault patterns, analyze HTTP responses, and report potential vulnerabilities when the suitable standards are met. As a result of we’re analyzing third-party websites, we used solely passive checks that don’t situation any further HTTP requests throughout scans (not like energetic checks). For every HTTP request despatched by the crawler, you may write a passive safety test script to research the response. In case your script determines that the response comprises delicate data, you may increase a vulnerability within the scanner.
We are going to undergo the method of making a customized script in a while, however you may go to the Invicti Safety GitHub repository to get the complete script for figuring out delicate information publicity used for this analysis, full with recognized patterns for delicate information. The customized script was used to crawl the Alexa high 10,000 websites and roughly 1 million Pastebin URLs and search the responses for delicate information. Pastebin imposes a fee restrict that may forestall us from scanning shortly, so we used historic information scraped from Pastebin by way of archive.org and hosted it in our personal check environments for evaluation.
Defining signatures and common expressions for delicate information
To seek out delicate information with our safety test, we first must determine and outline what constitutes delicate information. This requires two issues: the suitable common expression (regex) to match a selected sort of information and a option to measure the randomness (entropy) of recognized strings. The entropy test is essential as an indicator of distinctive identifiers. If a string matches a recognized entry key format and appears prefer it was generated randomly (has sufficient entropy), we might be virtually sure that it’s delicate information, and we are able to increase a vulnerability.
For instance, the next guidelines might be utilized to detect a leaked Amazon AWS entry key ID:
- Begin with a four-character block:
AKIA,AGPA,AROA,AIPA,ANPA,ANVA,ASIA, orA3Tplus one different character (A–Z, 0–9) - Proceed with 16 random characters
With this data, we are able to create an everyday expression as follows:
(A3T[A-Z0-9]|AKIA|AGPA|AROA|AIPA|ANPA|ANVA|ASIA)[A-Z0-9]{16}Subsequent, we have to test the randomness of every worth matched with this regex. On this analysis, we used Shannon entropy as a measure of randomness (see the code itemizing beneath for the precise algorithm). To find out a dependable threshold worth for entropy, we ran some exams on completely different random and non-random strings. The entropy testing included actual samples of delicate information in addition to some strings that we created ourselves. The outcomes had been as follows:
| Delicate information string | Entropy worth |
|---|---|
AKIA6GF5VPDHNC7Q**** |
~4.08 |
a414d04b125cfbcc22b9c97b0428**** |
~3.57 |
glpat-se2-ZwN_AdAd4rF4**** |
~4.39 |
AIzaSyD8kljjH-39qYr6KMuMs_gt7aQStuG**** |
~4.92 |
TEST123 |
~2.52 |
ABCEXAMPLE |
~2.92 |
ABAEXABPLW |
~2.64 |
As you may see from the info, actual secrets and techniques all had an entropy larger than 3, whereas non-random strings had been beneath 3. Contemplating each the extent of randomness and the size of probably delicate strings, we determined that 3 could be a superb entropy threshold to get rid of false optimistic matches.
With this regex and entropy threshold, we now have a easy and dependable option to detect strings which are positively delicate information, reminiscent of the true AWS keys (masked for privateness) of AKIAISCW7NXHB4RL****, AKIA352CUBQERWTX****, AROAU6G0VVT0VXTV****, and AIPAMQNLYYXLUQQU****.
Delicate information uncovered by high web sites
Our analysis discovered a number of forms of delicate information publicly uncovered on a whole lot of internet sites from the Alexa high 10,000 listing. In whole, 630 websites revealed at the very least one sort of secret, that means that 6.3% of the world’s most-visited websites are exposing delicate information. Earlier than we get into the detailed numbers, let’s take a look at the commonest forms of uncovered information.
Amazon Net Companies (AWS) API keys
Relying on the way you entry AWS and what sort of AWS person you might be, AWS requires several types of safety credentials. For instance, you want a username and password to log into the AWS Administration Console, whereas making programmatic calls to AWS requires entry keys. AWS entry keys are additionally wanted to make use of the AWS Command Line Interface or AWS Instruments for PowerShell.
If you generate a long-term entry key, you get a pair of strings: the entry key ID (for instance, AKIAIOSFODNN7EXAMPLE) and the key entry key (for instance, wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY). The key entry key can solely be downloaded on the time you create it, so for those who neglect to obtain it otherwise you lose it later, you’ll must generate a brand new one. Entry key IDs beginning with AKIA are long-term entry keys for an IAM person or an AWS account root person. Entry key IDs that start with ASIA are non permanent credential entry keys that you simply generate utilizing AWS STS transactions. See the AWS docs for extra details about AWS credentials.
Our check recognized 108 websites exposing a complete of 212 AWS entry keys, which implies that 1.08% of the world’s largest web sites expose their AWS keys in net responses. Whereas a lot of the delicate information was encountered in HTML responses, some was additionally uncovered by way of JavaScript and JSON recordsdata. Listed below are a couple of AWS keys from our outcomes:

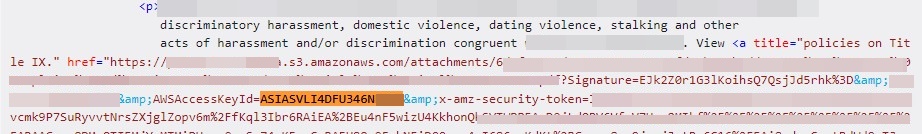

Google Cloud API keys
A Google Cloud API key’s a string that identifies a Google Cloud venture for quotas, billing, and monitoring. After producing a venture API key within the Google Cloud console, builders embed the important thing in each name to the API by way of a question parameter or request header. The API is primarily used for a paid service to embed the Google Maps database, search it, and use it in third-party apps. With some safety restrictions to restrict unauthorized use (which may doubtlessly rack up another person’s invoice), you might say that it’s regular for these keys to be uncovered if they’re solely legitimate for Google Maps. The issue is that the identical key can also be used for different paid companies.
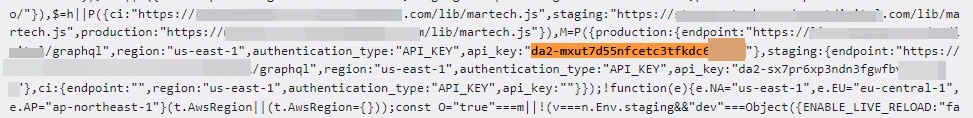
Google Cloud API keys begin with AIza adopted by 35 characters. For JavaScript and HTML responses, they will normally be detected utilizing the apiKey="AIza..." signature. In whole, we detected 171 Google Cloud information keys on 158 completely different web sites, with 95 responses being HTML, 75 JavaScript, and 1 JSON. Listed below are some examples of Google Cloud API keys:




Different generally uncovered keys and tokens
Whereas we counted a complete of 20 several types of delicate information, AWS and Google Cloud keys had been by far essentially the most quite a few provider-specific tokens. Listed below are a couple of examples of assorted tokens we discovered for different companies:


Analyzing the info and response sorts
Taking a look at information from the Alexa high 10,000 websites, we recognized 949 circumstances of doable delicate information disclosure throughout 595 completely different web sites. Practically half of those weren’t provider-specific however what we name generic API keys – mainly any tokens with the identify apiKey (with variations). Uncovered tokens that had secret within the identify had been labeled as generic secrets and techniques.
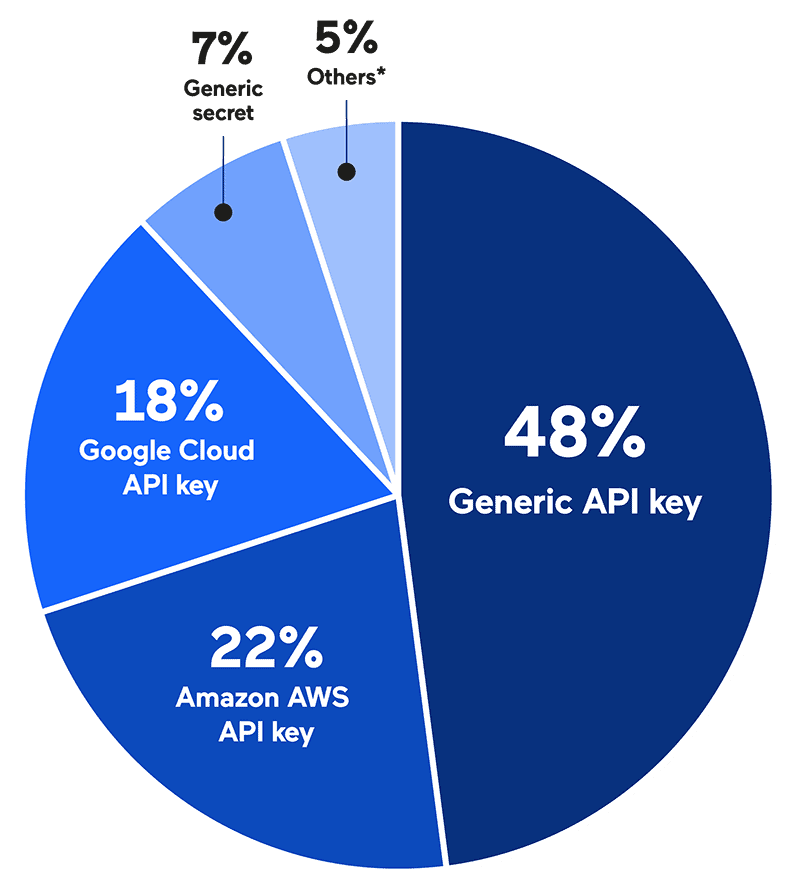
*Others: MailChimp API key, AWS AppSync GraphQL key, Fb app secret, Slack Webhook, Amazon AWS secret key, Twitter entry token secret, Github Personal, Fb App ID, Fb OAuth, Nexmo Secret, Google OAuth entry token, Symfony utility secret, Sentry auth token
Develop full information for forms of secrets and techniques
| Secret sort | Secret depend | Web site depend |
|---|---|---|
| Generic API key | 454 | 265 |
| Amazon AWS API key | 212 | 108 |
| Google Cloud API key | 171 | 158 |
| Generic secret | 65 | 54 |
| Slack webhook | 12 | 12 |
| AWS AppSync GraphQL key | 8 | 7 |
| Fb App secret | 8 | 8 |
| Amazon AWS secret key | 4 | 4 |
| Fb OAuth | 3 | 3 |
| Symfony Utility secret | 3 | 3 |
| Twitter Entry Token secret | 2 | 1 |
| Github personal | 2 | 2 |
| MailChimp API Key | 1 | 1 |
| Facebbook App ID | 1 | 1 |
| Nexmo secret | 1 | 1 |
| Google OAuth entry token | 1 | 1 |
| Sentry auth token | 1 | 1 |
| Whole | 949 | 630 |
By way of response sorts, over three-quarters of delicate information strings (753) had been uncovered in HTML responses. Practically all of the others had been revealed in JavaScript code, although a handful had been additionally returned in JSON responses.

Alexa high 10,000 web sites
Develop full information for forms of responses
| Response sort | HTML | JavaScript | JSON |
|---|---|---|---|
| Generic API key | 386 | 63 | 5 |
| Amazon AWS API key | 198 | 13 | 1 |
| Google Cloud API key | 95 | 75 | 1 |
| Generic secret | 49 | 16 | 0 |
| Fb App secret | 8 | 0 | 0 |
| AWS AppSync GraphQL key | 6 | 2 | 0 |
| Slack webhook | 2 | 10 | 0 |
| Twitter Entry Token secret | 2 | 0 | 0 |
| Fb OAuth | 2 | 1 | 0 |
| MailChimp API key | 1 | 0 | 0 |
| GitHub personal | 1 | 1 | 0 |
| Nexmo secret | 1 | 0 | 0 |
| Google OAuth entry token | 1 | 0 | 0 |
| Symfony Utility secret | 1 | 2 | 0 |
| Amazon AWS secret key | 0 | 4 | 0 |
| Fb App ID | 0 | 1 | 0 |
| Sentry auth token | 0 | 1 | 0 |
| Whole | 753 | 189 | 7 |
Examples of delicate information uncovered on Pastebin
It may appear that information despatched to websites reminiscent of Pastebin is restricted to one-time use and solely accessible via a random URL. Actually, it’s publicly accessible and might be scraped robotically for evaluation, so it’s essential to keep away from getting into any delicate information into such platforms. As talked about earlier, we retrieved archived Pastebin pastes and analyzed them in an area check atmosphere. Similar to the stay website information, the pastes additionally included some delicate information, together with AWS entry key IDs and database data:



So I uncovered an entry token – what’s the worst that would occur?
When a secret is uncovered, the most important risk issue is what might be finished with that particular secret. For a real-world instance exhibiting what may occur, I selected myself because the sufferer. Think about I created a private entry token (PAT) on GitHub after which by accident uncovered this token by forgetting to masks it after I took a screenshot for a weblog publish:
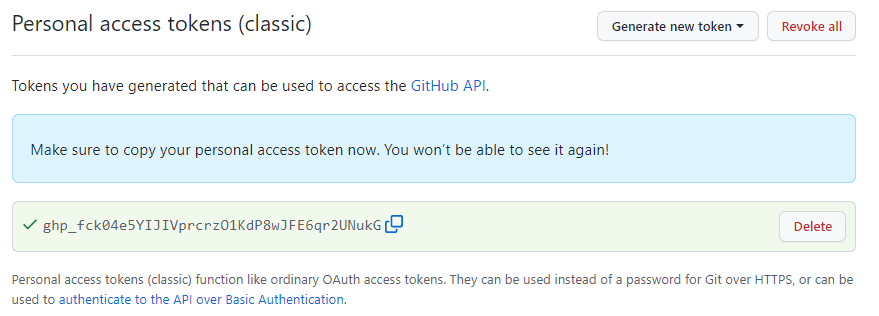
I may additionally expose my PAT by together with it in a decide to a public GitHub repo or in any variety of different methods. After you have my token, you may uncover my personal repository with just some traces of Python code (for those who’re undecided how to do this, GitHub Copilot can provide you a hand – simply watch out to not belief it an excessive amount of):
import requests
token = "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"
headers = {'Authorization': 'token ' + token}
repos = requests.get('https://api.github.com/person/repos', headers=headers)
A fast have a look at the response from the GitHub API reveals particulars of my personal repo:
"id": 575484076,
"node_id": "R_kgDOIk0wrA",
"identify": "private-repo-secrets",
"full_name": "kadirarslan-sensitive/private-repo-secrets",
"personal": true,
"proprietor": {
"login": "kadirarslan-sensitive",
And now you’re just a few traces away from cloning my personal repo and all of the top-secret proprietary code it comprises:
from git import Repo
HTTPS_REMOTE_URL = 'https://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:x-oauth-basic@github.com/kadirarslan-sensitive/private-repo-secrets'
DEST_NAME = 'cloned-private-project'
cloned_repo = Repo.clone_from(HTTPS_REMOTE_URL, DEST_NAME)
See if you will discover another secrets and techniques in there…
Writing a customized test to scan your functions for delicate information publicity
Thankfully, the strategies we utilized in our analysis to uncover delicate information in public sources may also be used to guard your individual information and functions. If you already know you will have functions that use a selected sort of confidential token, you may write a customized safety test to seek for delicate information publicity in manufacturing and even earlier than every launch (when built-in into your CI/CD pipeline). Let’s see how you should utilize Invicti’s Customized Safety Checks by way of Scripting function to create a script that finds your secret tokens.
Defining the info sample and common expression
For this situation, let’s assume your utility makes use of a product key that you simply wish to hold secret. Every product key’s a singular string that begins with prodKey adopted by a single digit surrounded by underscores and ends with 24 random alphanumeric characters, for instance:
prodKey_1_SUP3RS3CR3TTH1NKT0D3T3CTEach time the key follows a selected sample, we are able to simply detect it with Invicti. Initially, we want an everyday expression that matches the sample, which on this case could be:
/(prodKey_[0-9]{1}_[a-zA-Z0-9]{24})/gmBreaking this down, the regex matches:
- the string literal
prodKey(case delicate), - the character
_at place 8, - a single digit from 0 to 9 (inclusive),
- the character
_at place 10, - a string of 24 characters (a–z, A–Z, or 0–9).
Making a passive safety test in Invicti
Now that we now have the common expression, we’re prepared to jot down a customized safety test script in JavaScript. Since we’re solely analyzing responses, a passive safety test will probably be ample:
operate analyze(context, response) {
// Calculate the entropy for a matched worth
operate entropy(str) {
const len = str.size
// Construct a frequency map from the string
const frequencies = Array.from(str)
.cut back((freq, c) => (freq[c] = (freq[c] || 0) + 1) && freq, {})
return Object.keys(frequencies).map(e => frequencies[e])
.cut back((sum, f) => sum - f / len * Math.log2(f / len), 0)
}
// Regex for the key token sample
var secretRegex = /(prodKey_[0-9]{1}_[a-zA-Z0-9]{24})/gm;
isMatch = response.physique.match(secretRegex);
// Report a vulnerability if the regex matches and the entropy worth is above the edge
if (isMatch && entropy(isMatch[0]) >= 3) {
// Construct and return an Invicti vulnerability object utilizing a singular GUID
var vuln = new Vulnerability("<YOUR_GUID_HERE>");
vuln.CustomFields.Add("Delicate Knowledge Sort", String("Secret Key to your utility"));
vuln.CustomFields.Add("Delicate Knowledge", String(isMatch[0]));
vuln.CustomFields.Add("Entropy", String(entropy(isMatch[0])));
return vuln;
}
}
If you embody this tradition script in your safety checks and run a scan, Invicti will passively analyze responses to crawler requests and report any occurrences of strings that match your product key. Once more, as a result of this can be a passive test, discovering delicate information like this doesn’t contain sending any particular requests or payloads. To be taught extra about creating customized safety checks like this, see our help web page on customized safety checks by way of scripting.
Conclusion
On account of this analysis, we now have demonstrated that delicate information publicity occurs on every kind of internet sites massive and small, together with 6.3% of the world’s most visited websites. If such information is discovered and utilized by malicious actors, they might entry your inside environments, repositories, or billable companies, relying on the kind of secret. Aside from the chance of additional information exposures and assault escalations, you would possibly even endure financially if paid companies or sources are abused.
Most often, delicate data is uncovered on account of carelessness and inadequate safeguards within the SDLC course of. As a safety greatest apply, your safety testing carried out earlier than any replace to a manufacturing atmosphere (particularly for public-facing web sites) ought to embody checks for delicate information disclosure. You possibly can simply run devoted checks out of your dynamic utility safety testing (DAST) resolution, as proven above with the customized script for Invicti, and open-source instruments reminiscent of Trufflehog are additionally out there to smell out any delicate information you is likely to be exposing.










