Every week in the past, I wrote an article a couple of information breach that occurred at Twilio. It seems that Sign was impacted by this safety incident.
1900 Sign customers’ telephone numbers uncovered by Twilio information breach
The favored encrypted immediate messaging service depends on a telephone quantity to login, one thing which has drawn blended reactions from customers. A username and password system can be safer, in my view, as it might defend your privateness by not exposing your quantity to different customers. However that is a distinct matter, let’s concentrate on the problem at hand.
Because it makes use of a telephone quantity login system, Sign depends on the SMS protocol to obtain verification codes, and makes use of Twilio’s servers for offering the codes. 2-factor authentication through SMS has lengthy been criticized by safety specialists. It is not a really protected possibility, anybody who has entry to your telephone (and the SIM card with the registered quantity), can bypass the safety layer. There are further dangers too, since SMS messages usually are not encrypted (plain textual content), the verification code could be intercepted by malware or hackers.
Utilizing a neighborhood 2FA app like Aegis Authenticator for Android, or Raivo OTP for iOS, is a safer possibility, and in some ways the extra handy one too. Even Twilio’s personal 2FA app, Authy, is protected to make use of regardless of the father or mother firm struggling a knowledge breach, because the tokens are end-to-end encrypted earlier than being uploaded to the cloud.
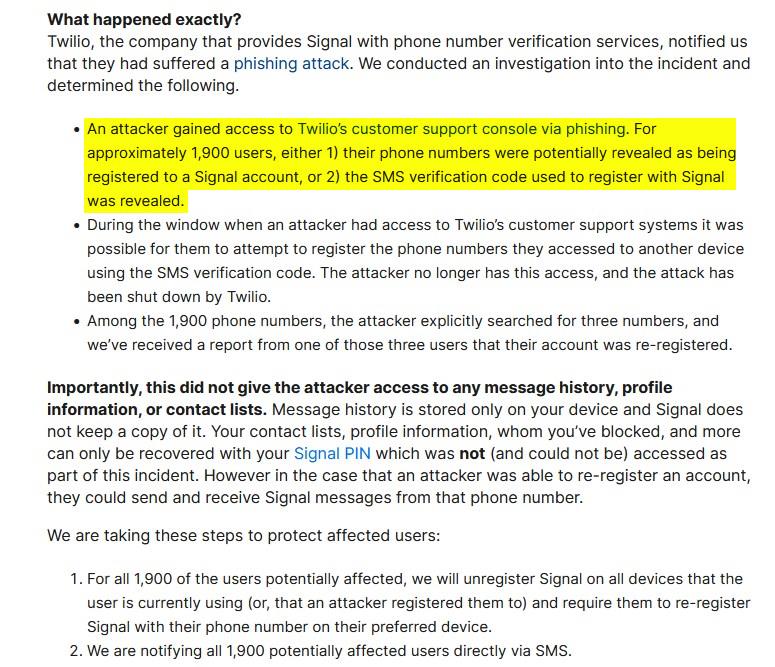
Sign says that the Twilio phishing assault uncovered the telephone numbers of round 1900 of the messaging service’s customers. Whereas that will look like lots, the corporate says that it represents a really low share of its complete customers. Sign has reassured customers that the info breach didn’t expose their private information similar to their message historical past, contact lists, profile data, blocked customers, and many others. So, how precisely are customers affected?
Hackers might have gained entry to the SMS verification code that was used to register Sign accounts. The attackers could have tried to re-register a person’s quantity on one other gadget, or found {that a} quantity was tied to a Sign account. Twilio labored with service suppliers to close down the assault vectors as quickly because it found the assault and notified Sign about it, so whereas the menace has ended, there’s a risk that the uncovered numbers had been in danger earlier than the problem had been resolved.
Sign says that the attacker searched for 3 numbers, and a type of customers had reported that their account had been re-registered by another person. That is why the corporate is reaching out to the opposite affected customers, to be able to immediate them to re-register Sign on their gadgets. You may discuss with this help article for extra particulars relating to the incident.
In the meantime, Twilio has confirmed that roughly 125 of its customers’ information had been accessed by malicious actors for a restricted time, and that it alerted them about it. The corporate states that there is no such thing as a proof that buyer passwords, authentication tokens, or API keys had been accessed by the attackers.
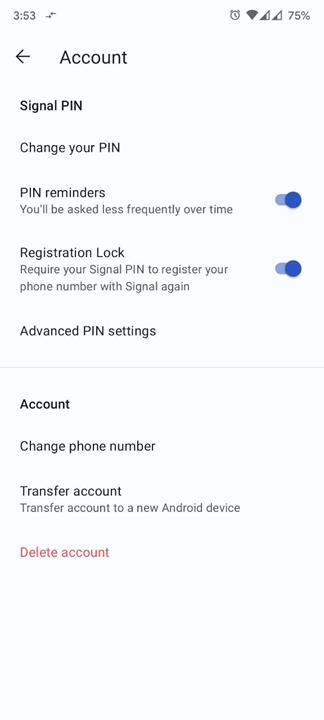
Sign can also be encouraging customers to allow registration lock on their Sign accounts to safe their accounts. You are able to do so from the Sign Settings (profile) > Account > Registration Lock. This can add an additional layer of safety, i.e., the app will ask you to enter your Sign PIN to register the account once more.
Abstract

Article Identify
Sign says Twilio information breach resulted in 1900 customers’ telephone numbers being uncovered
Description
Prompt messaging service Sign says that 1900 customers’ telephone numbers had been uncovered due to the Twilio information breach.
Writer
Ashwin
Writer
Ghacks Know-how Information
Brand

Commercial










