The sufferer shaming website operated by the Snatch ransomware group is leaking knowledge about its true on-line location and inner operations, in addition to the Web addresses of its guests, KrebsOnSecurity has discovered. The leaked knowledge counsel that Snatch is one in all a number of ransomware teams utilizing paid advertisements on Google.com to trick individuals into putting in malware disguised as in style free software program, akin to Microsoft Groups, Adobe Reader, Mozilla Thunderbird, and Discord.
First noticed in 2018, the Snatch ransomware group has revealed knowledge stolen from lots of of organizations that refused to pay a ransom demand. Snatch publishes its stolen knowledge at a web site on the open Web, and that content material is mirrored on the Snatch staff’s darknet website, which is simply reachable utilizing the worldwide anonymity community Tor.
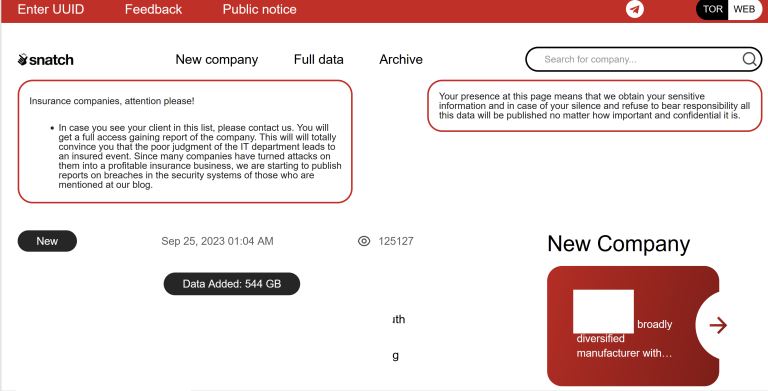
The sufferer shaming web site for the Snatch ransomware gang.
KrebsOnSecurity has discovered that Snatch’s darknet website exposes its “server standing” web page, which incorporates details about the true Web addresses of customers accessing the web site.
Refreshing this web page each few seconds exhibits that the Snatch darknet website generates an honest quantity of visitors, typically attracting 1000’s of tourists every day. However by far essentially the most frequent repeat guests are coming from Web addresses in Russia that both at present host Snatch’s clear internet domains or lately did.
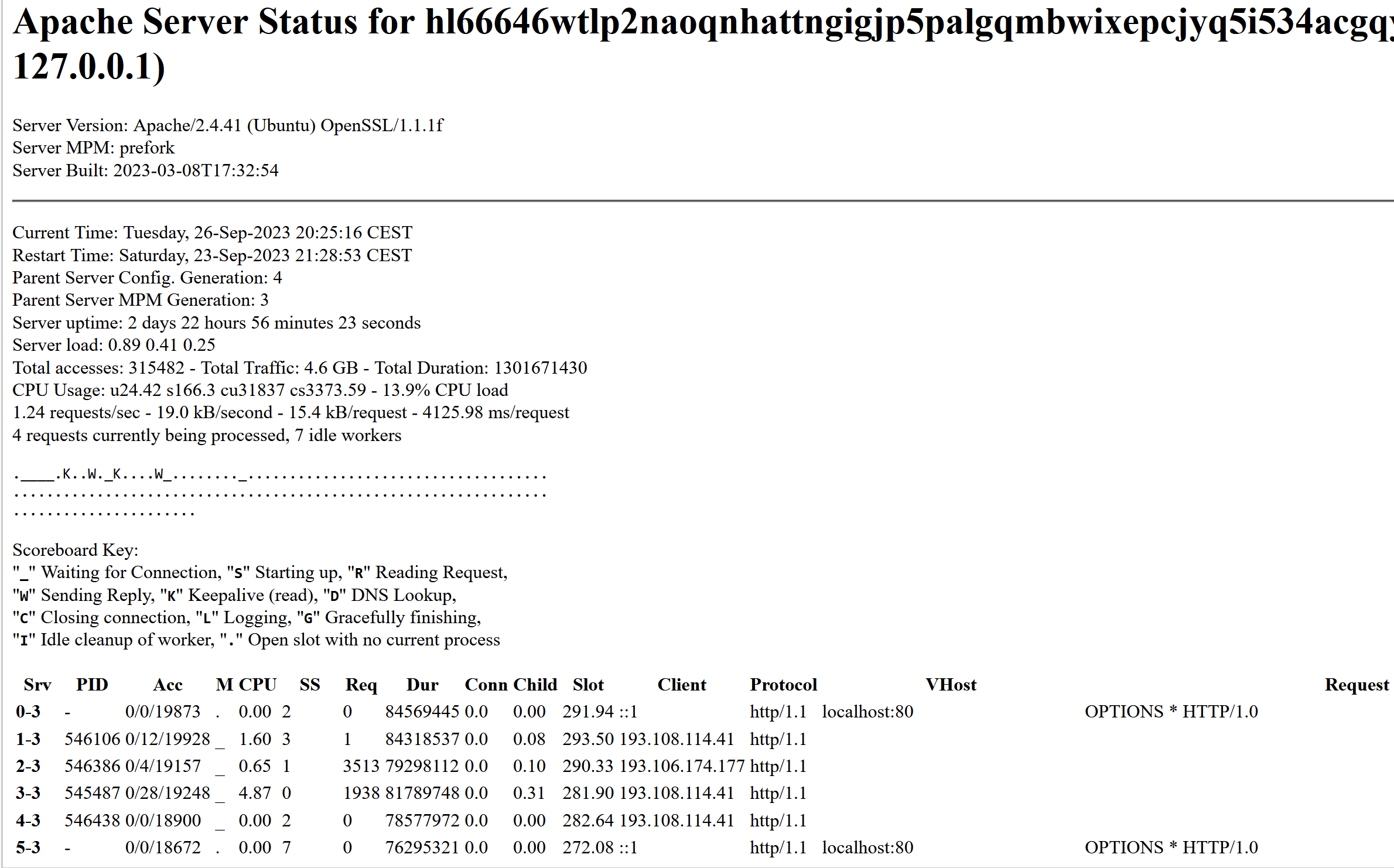
The Snatch ransomware gang’s sufferer shaming website on the darknet is leaking knowledge about its guests. This “server standing” web page says that Snatch’s web site is on Central European Summer time Time (CEST) and is powered by OpenSSL/1.1.1f, which is not supported by safety updates.
In all probability essentially the most energetic Web tackle accessing Snatch’s darknet website is 193.108.114[.]41, which is a server in Yekaterinburg, Russia that hosts a number of Snatch domains, together with snatchteam[.]prime, sntech2ch[.]prime, dwhyj2[.]prime and sn76930193ch[.]prime. It might nicely be that this Web tackle is exhibiting up incessantly as a result of Snatch’s clear-web website includes a toggle button on the prime that lets guests change over to accessing the location through Tor.
One other Web tackle that confirmed up incessantly within the Snatch server standing web page was 194.168.175[.]226, at present assigned to Matrix Telekom in Russia. In keeping with DomainTools.com, this tackle additionally hosts or else lately hosted the same old coterie of Snatch domains, in addition to fairly a couple of domains phishing recognized manufacturers akin to Amazon and Cashapp.
The Moscow Web tackle 80.66.64[.]15 accessed the Snatch darknet website all day lengthy, and that tackle additionally housed the suitable Snatch clear-web domains. Extra curiously, that tackle is residence to a number of latest domains that seem confusingly much like recognized software program firms, together with libreoff1ce[.]com and www-discord[.]com.
That is attention-grabbing as a result of the phishing domains related to the Snatch ransomware gang had been all registered to the identical Russian title — Mihail Kolesnikov, a reputation that’s considerably synonymous with latest phishing domains tied to malicious Google advertisements.
Kolesnikov could possibly be a nod to a Russian normal made well-known throughout Boris Yeltsin’s reign. Both means, it’s clearly a pseudonym, however there are another commonalities amongst these domains which will present perception into how Snatch and different ransomware teams are sourcing their victims.
DomainTools says there are greater than 1,300 present and former domains registered to Mihail Kolesnikov between 2013 and July 2023. About half of the domains look like older web sites promoting feminine escort companies in main cities round the USA (e.g. the now-defunct pittsburghcitygirls[.]com).
The opposite half of the Kolesnikov web sites are far more moderen phishing domains principally ending in “.prime” and “.app” that seem designed to imitate the domains of main software program firms, together with www-citrix[.]prime, www-microsofteams[.]prime, www-fortinet[.]prime, ibreoffice[.]prime, www-docker[.]prime, www-basecamp[.]prime, ccleaner-cdn[.]prime, adobeusa[.]prime, and www.real-vnc[.]prime.
In August 2023, researchers with Trustwave Spiderlabs stated they encountered domains registered to Mihail Kolesnikov getting used to disseminate the Rilide info stealer trojan.
Nevertheless it seems a number of crime teams could also be utilizing these domains to phish individuals and disseminate every kind of information-stealing malware. In February 2023, Spamhaus warned of an enormous surge in malicious advertisements that had been hijacking search ends in Google.com, and getting used to distribute a minimum of 5 completely different households of data stealing trojans, together with AuroraStealer, IcedID/Bokbot, Meta Stealer, RedLine Stealer and Vidar.
For instance, Spamhaus stated victims of those malicious advertisements would seek for Microsoft Groups in Google.com, and the search engine would typically return a paid advert spoofing Microsoft or Microsoft Groups as the primary end result — above all different outcomes. The malicious advert would come with a emblem for Microsoft and at first look look like a secure and trusted place to obtain the Microsoft Groups consumer.
Nevertheless, anybody who clicked on the end result was whisked away as a substitute to mlcrosofteams-us[.]top — yet one more malicious area registered to Mr. Kolesnikov. And whereas guests to this web site could consider they’re solely downloading the Microsoft Groups consumer, the installer file features a copy of the IcedID malware, which is admittedly good at stealing passwords and authentication tokens from the sufferer’s internet browser.
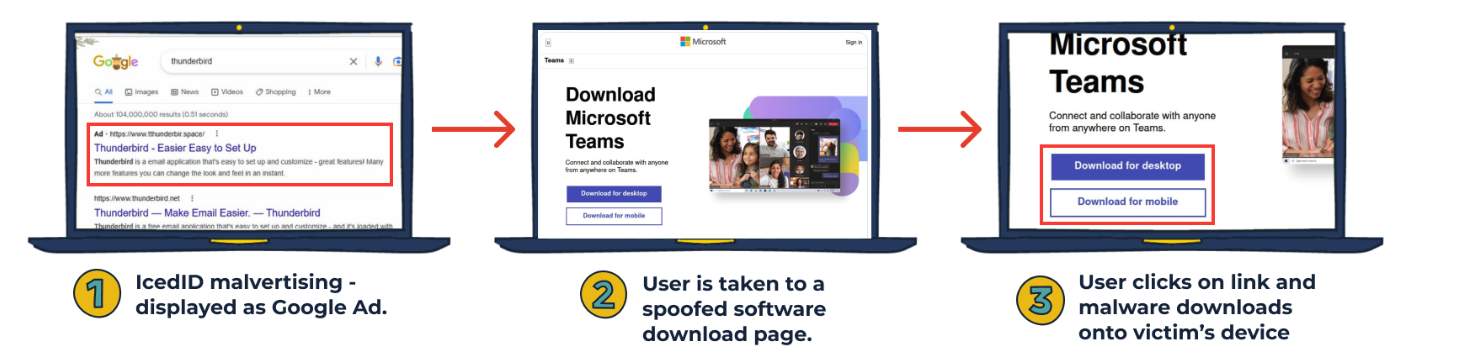
Picture: Spamhaus
The founding father of the Swiss anti-abuse web site abuse.ch instructed Spamhaus it’s seemingly that some cybercriminals have began to promote “malvertising as a service” on the darkish internet, and that there’s quite a lot of demand for this service.
In different phrases, somebody seems to have constructed a really worthwhile enterprise churning out and selling new software-themed phishing domains and promoting that as a service to different cybercriminals. Or maybe they’re merely promoting any stolen knowledge (and any company entry) to energetic and hungry ransomware group associates.
The tip concerning the uncovered “server standing” web page on the Snatch darkweb website got here from @htmalgae, the identical safety researcher who alerted KrebsOnSecurity earlier this month that the darknet sufferer shaming website run by the 8Base ransomware gang was inadvertently left in growth mode.
That oversight revealed not solely the true Web tackle of the hidden 8Base website (in Russia, naturally), but additionally the id of a programmer in Moldova who apparently helped to develop the 8Base code.
@htmalgae stated the concept of a ransomware group’s sufferer shaming website leaking knowledge that they didn’t intend to reveal is deliciously ironic.
“It is a prison group that shames others for not defending person knowledge,” @htmalgae stated. “And right here they’re leaking their person knowledge.”
The entire malware talked about on this story is designed to run on Microsoft Home windows units. However Malwarebytes lately lined the emergence of a Mac-based info stealer trojan referred to as AtomicStealer that was being marketed via malicious Google advertisements and domains that had been confusingly much like software program manufacturers.
Please be additional cautious if you find yourself looking out on-line for in style software program titles. Cracked, pirated copies of main software program titles are a frequent supply of infostealer infections, as are these rogue advertisements masquerading as search outcomes. Be sure that to double-check you might be truly on the area you consider you’re visiting *earlier than* you obtain and set up something.
Keep tuned for Half II of this submit, which features a nearer take a look at the Snatch ransomware group and their founder.
Additional studying:
@HTMalgae’s listing of the highest Web addresses seen accessing Snatch’s darknet website
Ars Technica: Till Additional Discover Assume Twice Earlier than Utilizing Google to Obtain Software program
Bleeping Pc: Hackers Abuse Google Advertisements to Unfold Malware in Legit Software program










