 We’re happy to announce the provision of Sophos ZTNA 2.1, which brings help for on-premise Microsoft Lively Listing for identification, zero downtime, seamless failover between cloud points-of-presence, and essential safety enhancements.
We’re happy to announce the provision of Sophos ZTNA 2.1, which brings help for on-premise Microsoft Lively Listing for identification, zero downtime, seamless failover between cloud points-of-presence, and essential safety enhancements.
This launch provides a brand new identification supplier answer along with the present cloud-based Microsoft Entra ID and Okta options already supported by Sophos ZTNA. It allows organizations with out cloud infrastructure or a cloud-based identification platform to simply undertake Sophos ZTNA by leveraging their in-house Microsoft AD system for authentication with help for MFA via captchas or e-mail OTPs.
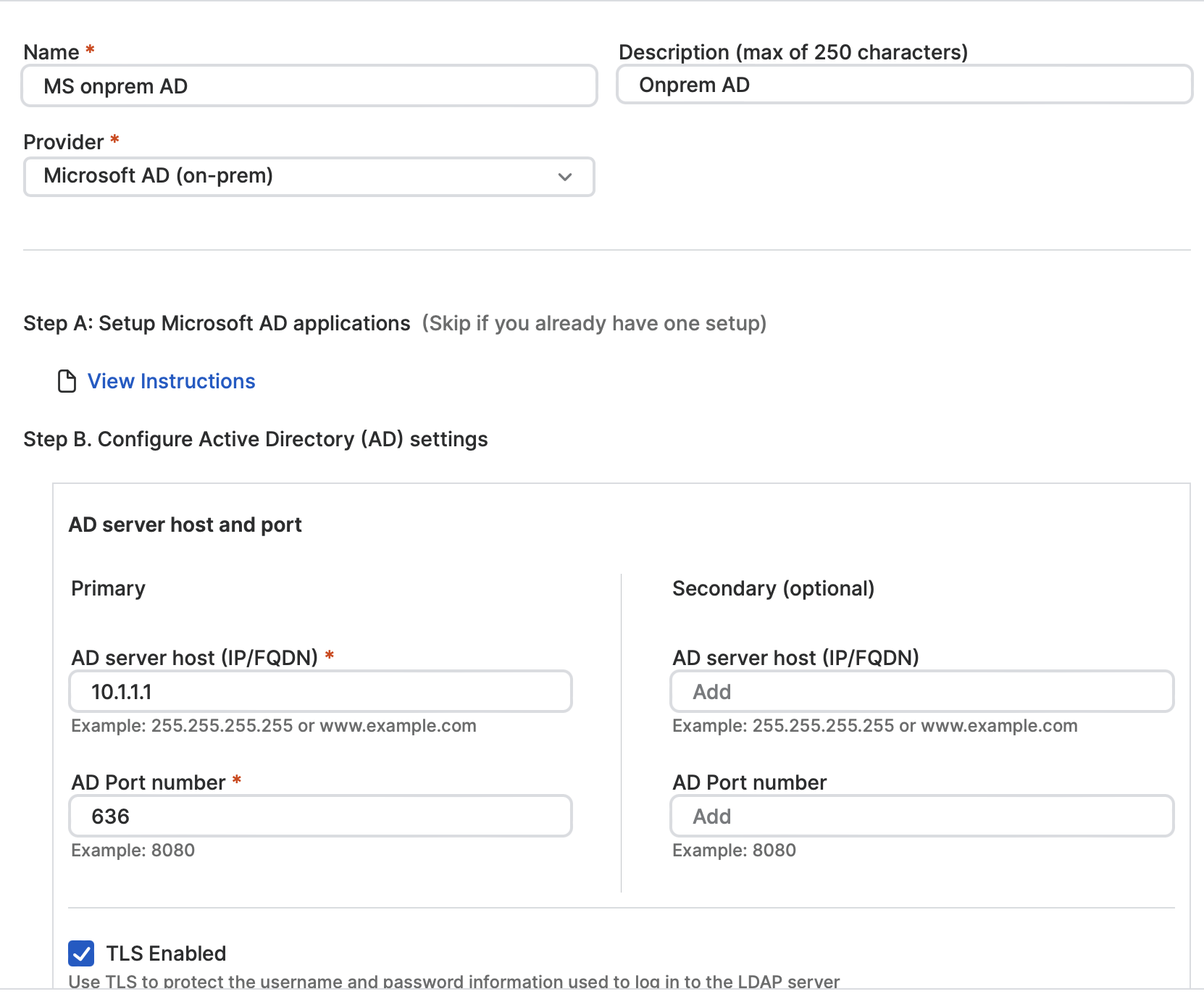
As well as, cloud gateways working on digital platforms (ESXi or Hyper-V) now help zero downtime and seamless failover between cloud factors of presence. This functionality will even be out there for Sophos Firewall-integrated ZTNA Gateways with the discharge of v20 MR2, which is scheduled for later this month. This new functionality permits for seamless transitions to the following closest regional gateway within the occasion of an outage in your most well-liked gateway area, making certain uninterrupted ZTNA entry throughout the outage.
An extra replace with safety enhancements can also be out there as ZTNA 2.1.1. You will want to first replace your gateways to 2.1 after which apply the two.1.1 replace after that.
Methods to get the updates
The gateway picture updates can be found from Sophos Central. There is no such thing as a have to replace your ZTNA brokers.
1. In Sophos Central, navigate to the Gateways web page and spot a sign that a picture replace is obtainable. This notification is barely seen on gateways hosted on ESXi and Hyper-V platforms. For gateways hosted on Sophos Firewall, they are going to be up to date when making use of firmware replace v20 MR2 (out there later this month).
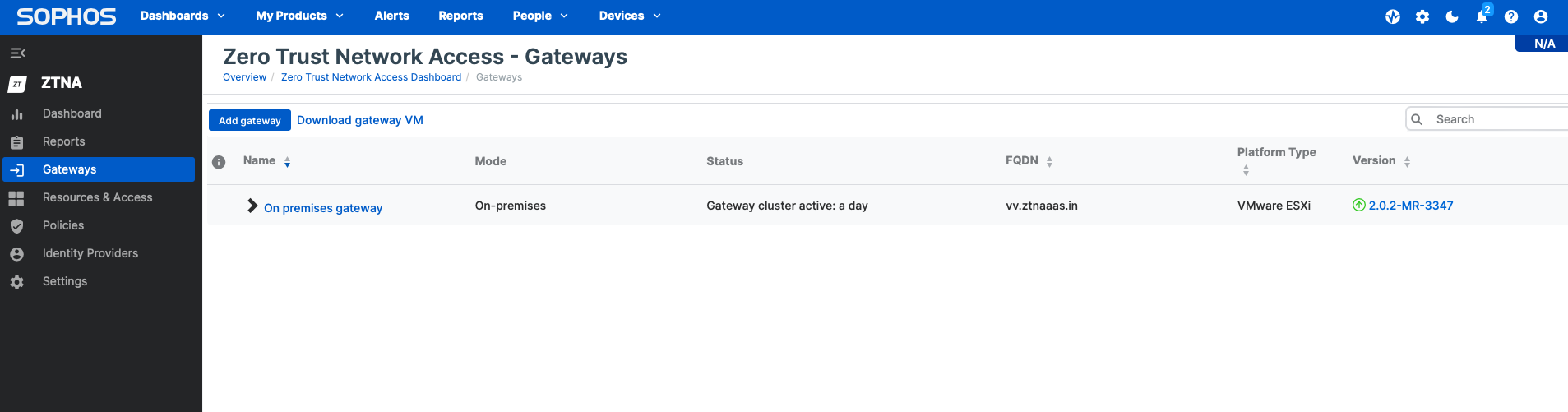
2. You may both provoke the improve instantly or schedule the improve for later. The replace could take as much as half-hour.
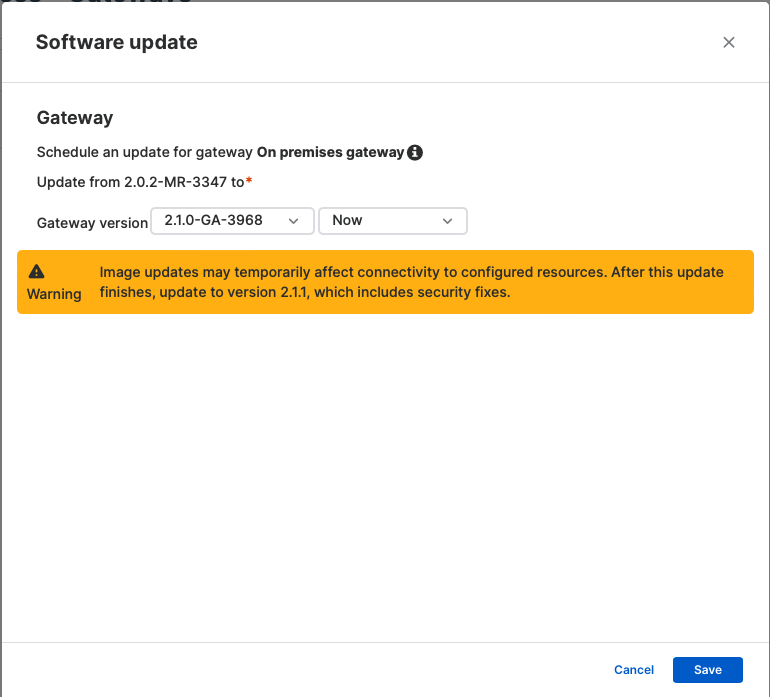
3. After the improve is accomplished and the gateway is again to “Lively,” confirm on the gateway’s diagnostics console that every one the checks cross earlier than initiating the following replace to ZTNA 2.1.1.
Model 2.1.1 contains essential safety and vulnerability fixes, and we extremely advocate that clients start the improve course of instantly. Upgrading to model 2.1.1 must also take roughly half-hour for a single node. The time required will probably be proportional if the deployment includes a multi-node cluster.
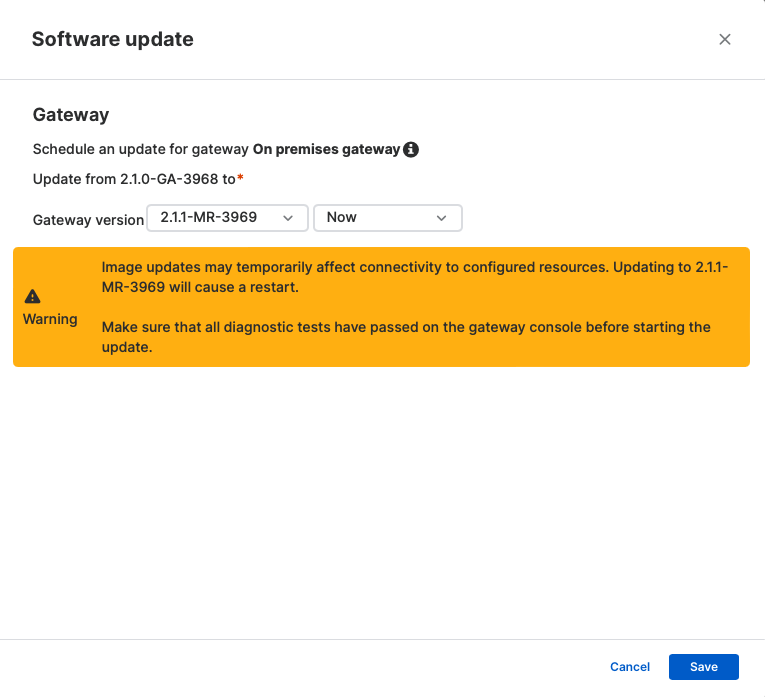
4. Test the gateway console diagnostics as soon as the replace is full and the gateway returns to the “Lively” state. If all diagnostics checks cross, useful resource entry will be resumed.
Documentation
The most recent on-line documentation is right here.
The troubleshooting information has additionally been up to date in case you encounter any points throughout configuration.










