As attackers concentrate on political ends, large payouts, risk hunters must concentrate on id intrusions, entry retailers and ways enabling quick lateral motion.

Adversary breakout time — the time it takes a risk actor to zipline from the preliminary level of entry right into a community — hit a mean all-time low of 79 minutes, down from 84 minutes final 12 months, with the quickest breakout of the 12 months coming in at a file of seven minutes.
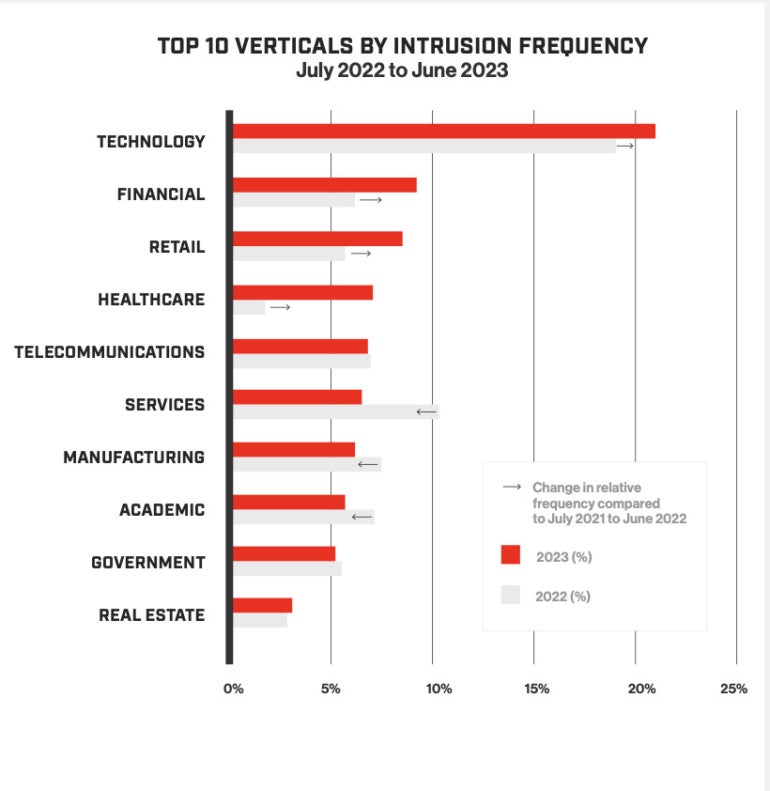
“That’s essential, as a result of your whole playbooks from the protection aspect must be decided by how rapidly the risk actor is working,” mentioned Param Singh, vp of CrowdStrike’s risk monitoring unit Falcon OverWatch. “All blue teamers, together with us, must do issues like take into consideration automation and determine cease the quickest risk actor, one transferring laterally inside seven minutes.” The risk report additionally confirmed a 40% year-over-year improve in interactive intrusions, wherein an adversary interacts with and executes towards a goal. Probably the most regularly focused vertical was expertise for the sixth consecutive 12 months, adopted by monetary, retail, well being care and telecommunications sectors (Determine A).
Determine A
“We have a look at among the similar stats 12 months over 12 months, and we’re seeing that for a few of these the needle is transferring and favoring the risk actors,” mentioned Singh.
CrowdStrike’s report, utilizing information from July 1, 2022, to June 30, 2023, garnered by Falcon OverWatch and revealed this week on the annual Black Hat conference in Las Vegas, additionally discovered that:
- Sixty-two p.c of interactive intrusions concerned the abuse of legitimate accounts, whereas there was a 160% improve in makes an attempt to assemble secret keys and different credentials through cloud occasion metadata APIs.
- There was a 40% year-over-year improve in interactive intrusions, with probably the most regularly focused vertical being expertise for the sixth consecutive 12 months, adopted by monetary, retail, well being care and telecommunications.
- The amount of interactive intrusion exercise towards the monetary companies trade elevated by over 80% this 12 months versus 2022, the biggest bounce CrowdStrike has noticed for the monetary companies trade.
CrowdStrike additionally reported that North Korea was the nation-state entrance of probably the most aggressive state-sponsored assaults.
Additionally on the rise are entry brokers. The agency reported a 147% improve in entry dealer ads on the darkish internet, up 35% from 6 months in the past.
CrowdStrike additionally discovered that, for the sixth consecutive 12 months, the expertise sector was probably the most regularly focused, with monetary second, displacing telecommunications, which is the third most focused vertical. North Korean risk teams, aiming to generate forex have been, in accordance with the report, probably the most aggressive state-sponsored adversaries versus the monetary sector.
The report discovered that, whereas adversaries reminiscent of North Korean aligned attackers concentrate on stealing cryptocurrency or nonfungible tokens (NFTs), the larger image is that opportunistic large recreation looking (BGH) ransomware and information theft campaigns stay the first eCrime risk to monetary establishments.
The report additionally factors to 2 attackers, the Iranian Kitten and Chinese language Panda as purveyors of two particular practices: Kitten customers exploit a sure form of asset whereas Panda adversaries are more and more aiming for breadth of assaults levied towards as many targets as potential (Determine B)
Determine B

The expertise sector’s reliance on and use of delicate information make it a BGH goal for ransomware and information theft. Different distinguished eCrime threats to the expertise sector embrace enabling companies, entry brokers and knowledge theft campaigns, in accordance with CrowdStrike’s report.
The agency additionally pointed to some hallmarks of 2023 ways by risk actors:
- Exploitation of weak software program to realize entry through entry brokers, which means organizations want visibility into their exterior assault floor.
- Rampant use of reliable distant monitoring and administration instruments to mix into enterprise noise and keep away from detection.
- Potential to navigate a number of working programs, such because the 3CX provide chain assault by Labyrinth Chollima, found by CloudStrike.
‘Kerberoasting’ is heating up in 2023
Over the previous 12 months, Falcon OverWatch noticed a 583% improve in a tactic referred to as Kerberoasting, which supplies attackers larger privileges and allows lateral motion inside a sufferer’s atmosphere.
Kerberos is an authentication protocol that grants tickets for entry to Lively Listing accounts, a protocol based mostly on a singular identifier. Kerberoasting entails the theft of tickets containing credentials, related to the identifiers. Though encrypted, these credentials will be cracked offline.
“It’s not a brand new method, however we’re seeing it turning into an even bigger a part of the risk actor playbook,” mentioned Singh. “When you assault an preliminary sufferer, the stolen credentials you used to get onto that machine is probably not sufficient to maneuver laterally and work in your mission. Kerboroasting permits privilege escalation; as a result of it’s an efficient option to transfer laterally, we’re seeing this big spike.”










