Telephones, tablets and workstations with unpatched CVEs are a transparent and current hazard. New Armis research lists essentially the most susceptible.

Asset visibility and safety firm Armis recognized linked belongings posing the best dangers to world enterprise. Armis’ new analysis, primarily based on evaluation from its Asset Intelligence Engine, targeted on linked belongings with essentially the most assault makes an attempt, weaponized frequent vulnerabilities and exposures and different high-risk elements.
Most susceptible belongings included IoT, IT, constructing administration
The highest 10 asset varieties with the very best variety of assault makes an attempt have been distributed throughout IT, operational expertise, the Web of Issues, the Web of Medical Issues, the Web of Private Issues and constructing administration programs.
SEE: Securing IoT with Microsoft Defender for IoT sensors (TechRepublic)
Armis reported that the gadgets with the very best variety of assault makes an attempt have been:
- Engineering workstations (OT).
- Imaging workstations (IoMT).
- Media gamers (IoT).
- Private computer systems (IT).
- Digital machines (IT).
- Uninterruptible energy provide (UPS) gadgets (BMS).
- Servers (IT).
- Media writers (IoMT).
- Tablets (IoPT).
- Cell phones (IoPT).
The analysis reiterates findings in June this yr about essentially the most at-risk gadgets by the agency’s Asset Intelligence and Safety Platform, which tracks over 3 billion belongings in line with Armis.
In that analysis, Armis discovered vital vulnerabilities in engineering workstations, supervisory management and knowledge acquisition servers, automation servers, management system historians and programmable logic controllers, that are additionally essentially the most susceptible OT and industrial management programs.
“Malicious actors are deliberately concentrating on these belongings as a result of they’re externally accessible, have an expansive and complex assault floor and recognized weaponized CVEs,” mentioned Tom Gol, CTO of analysis at Armis.
Gol mentioned in a press release that these belongings are enticing for attackers as a result of they’ll wreak havoc throughout a number of programs.
SEE: Armis and Honeywell uncover vulnerabilities in Honeywell Techniques (TechRepublic)
“Engineering workstations could be linked to all controllers in a manufacturing unit, imaging workstations will acquire non-public affected person knowledge from hospitals and UPSs can function an entry level to vital infrastructure entities, making all of those enticing targets for malicious actors with various agendas, like deploying ransomware or inflicting destruction to society within the case of nation-state assaults,” Gol mentioned, including that defenders ought to enhance visibility of those belongings and patch vulnerabilities (Determine A).
Determine A
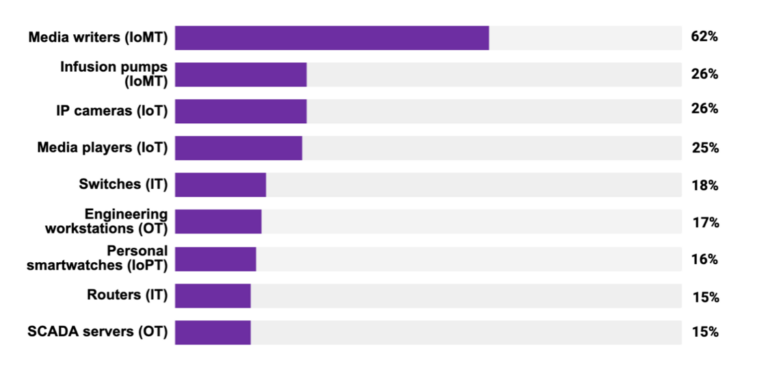
Excessive-risk elements for frequent {hardware} and programs
The Armis researchers discovered a variety of asset varieties with frequent high-risk elements:
- Servers and programmable logic controllers constituting end-of-life or end-of-support working programs.
- Private computer systems and the like utilizing SMBv1, a posh and unencrypted protocol. These vulnerabilities, together with EternalBlue, have been exploited by WannaCry and NotPetya assaults.
- Property with excessive vulnerability scores or which have had threats detected or have been flagged for unencrypted visitors or that also have the CDPwn vulnerabilities impacting community infrastructure and VoIPs.
- Half of pneumatic tube programs have an unsafe software program replace mechanism.
Armis mentioned it discovered that 74% of organizations immediately nonetheless have a minimum of one asset of their community susceptible to EternalBlue exploited by NotPetya to achieve preliminary entry earlier than utilizing credential theft for privilege escalation.
“Persevering with to coach world companies concerning the evolving and elevated danger being launched to their assault floor by managed and unmanaged belongings is a key mission of ours,” mentioned Nadir Izrael, CTO and cofounder of Armis. “This intelligence is essential to serving to organizations defend in opposition to malicious cyberattacks. With out it, enterprise, safety and IT leaders are at midnight, susceptible to blind spots that dangerous actors will search to use.”










