On December 7, 2021, Google introduced it was suing two Russian males allegedly chargeable for working the Glupteba botnet, a worldwide malware menace that has contaminated hundreds of thousands of computer systems over the previous decade. That very same day, AWM Proxy — a 14-year-old anonymity service that rents hacked PCs to cybercriminals — out of the blue went offline. Safety specialists had lengthy seen a hyperlink between Glupteba and AWM Proxy, however new analysis reveals AWM Proxy’s founder is among the males being sued by Google.
AWMproxy, the storefront for renting entry to contaminated PCs, circa 2011.
Launched in March 2008, AWM Proxy rapidly turned the biggest service for crooks looking for to route their malicious Internet site visitors by compromised gadgets. In 2011, researchers at Kaspersky Lab confirmed that just about the entire hacked methods for hire at AWM Proxy had been compromised by TDSS (a.ok.a TDL-4 and Alureon), a stealthy “rootkit” that installs deep inside contaminated PCs and masses even earlier than the underlying Home windows working system boots up.
In March 2011, safety researchers at ESET discovered TDSS was getting used to deploy Glupteba, one other rootkit that steals passwords and different entry credentials, disables safety software program, and tries to compromise different gadgets on the sufferer’s community — akin to Web routers and media storage servers — to be used in relaying spam or different malicious site visitors.
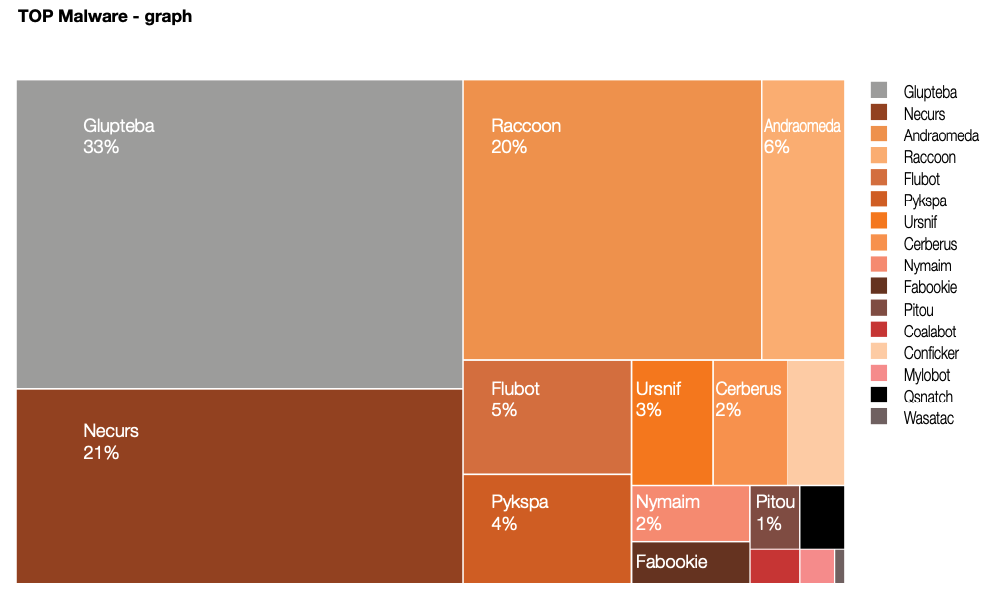
A report from the Polish pc emergency response staff (CERT Orange Polksa) discovered Glupteba was by far the most important malware risk in 2021.
Like its predecessor TDSS, Glupteba is primarily distributed by “pay-per-install” or PPI networks, and through site visitors bought from site visitors distribution methods (TDS). Pay-per-install networks attempt to match cybercriminals who have already got entry to massive numbers of hacked PCs with different crooks looking for broader distribution of their malware.
In a typical PPI community, purchasers will submit their malware—a spambot or password-stealing Trojan, for instance —to the service, which in flip expenses per thousand profitable installations, with the worth relying on the requested geographic location of the specified victims. One of the vital widespread methods PPI associates generate income is by secretly bundling the PPI community’s installer with pirated software program titles which might be broadly out there for obtain through the online or from file-sharing networks.
An instance of a cracked software program obtain web site distributing Glupteba. Picture: Google.com.
Over the previous decade, each Glupteba and AWM Proxy have grown considerably. When KrebsOnSecurity first lined AWM Proxy in 2011, the service was promoting entry to roughly 24,000 contaminated PCs scattered throughout dozens of nations. Ten years later, AWM Proxy was providing 10 instances that variety of hacked methods on any given day, and Glupteba had grown to a couple of million contaminated gadgets worldwide.
There may be additionally ample proof to counsel that Glupteba could have spawned Meris, an enormous botnet of hacked Web of Issues (IoT) gadgets that surfaced in September 2021 and was chargeable for among the largest and most disruptive distributed denial-of-service (DDoS) assaults the Web has ever seen.
However on Dec. 7, 2021, Google introduced it had taken technical measures to dismantle the Glupteba botnet, and filed a civil lawsuit (PDF) in opposition to two Russian males considered chargeable for working the huge crime machine. AWM Proxy’s on-line storefront disappeared that very same day.
AWM Proxy rapidly alerted its prospects that the service had moved to a brand new area, with all buyer balances, passwords and buy histories seamlessly ported over to the brand new house. Nevertheless, subsequent takedowns concentrating on AWM Proxy’s domains and different infrastructure have conspired to maintain the service on the ropes and ceaselessly switching domains ever since.
Earlier this month, the US, Germany, the Netherlands and the U.Ok. dismantled the “RSOCKS” botnet, a competing proxy service that had been in operation since 2014. KrebsOnSecurity has recognized the proprietor of RSOCKS as a 35-year-old from Omsk, Russia who runs the world’s largest discussion board catering to spammers.

The staff who stored issues operating for RSOCKS, circa 2016.
Shortly after final week’s story on the RSOCKS founder, I heard from Riley Kilmer, co-founder of Spur.us, a startup that tracks felony proxy companies. Kilmer mentioned RSOCKS was equally disabled after Google’s mixed authorized sneak assault and technical takedown concentrating on Glupteba.
“The RSOCKS web site gave you the estimated variety of proxies in every of their subscription packages, and that quantity went all the way down to zero on Dec. 7,” Kilmer mentioned. “It’s not clear if which means the companies had been operated by the identical individuals, or in the event that they had been simply utilizing the identical sources (i.e., PPI applications) to generate new installations of their malware.”
Kilmer mentioned every time his firm tried to find out what number of methods RSOCKS had on the market, they discovered every Web deal with being bought by RSOCKS was additionally current in AWM Proxy’s community. As well as, Kilmer mentioned, the appliance programming interfaces (APIs) utilized by each companies to maintain monitor of contaminated methods had been just about equivalent, as soon as once more suggesting sturdy collaboration.
“100% of the IPs we obtained again from RSOCKS we’d already recognized in AWM,” Kilmer mentioned. “And the IP port mixtures they provide you once you entry a person IP had been the identical as from AWM.”
In 2011, KrebsOnSecurity revealed an investigation that recognized one of many founders of AWM Proxy, however Kilmer’s revelation prompted me to take a recent have a look at the origins of this sprawling cybercriminal enterprise to find out if there have been further clues exhibiting extra concrete hyperlinks between RSOCKS, AWM Proxy and Glupteba.
IF YOUR PLAN IS TO RIP OFF GOOGLE…
Supporting Kilmer’s concept that AWM Proxy and RSOCKS could merely be utilizing the identical PPI networks to unfold, additional analysis reveals the RSOCKS proprietor additionally had an possession stake in AD1[.]ru, a particularly well-liked Russian-language pay-per-install community that has been in operation for no less than a decade.
Google took goal at Glupteba partly as a result of its house owners had been utilizing the botnet to divert and steal huge sums in internet advertising income. So it’s greater than somewhat ironic that the vital piece of proof linking all of those operations begins with a Google Analytics code included within the HTML code for the unique AWM Proxy again in 2008 (UA-3816536).
That analytics code additionally was current on a handful of different websites over time, together with the now-defunct Russian area identify registrar Domenadom[.]ru, and the web site web-site[.]ru, which curiously was a Russian firm working a worldwide actual property appraisal enterprise known as American Appraisal.
Two different domains linked to that Google Analytics code — Russian plastics producers techplast[.]ru and tekhplast.ru — additionally shared a special Google Analytics code (UA-1838317) with web-site[.]ru and with the area “starovikov[.]ru.”
The identify on the WHOIS registration data for the plastics domains is an “Alexander I. Ukraincki,” whose private data is also included within the domains tpos[.]ru and alphadisplay[.]ru, each apparently producers of point-of-sale cost terminals in Russia.
Constella Intelligence, a safety agency that indexes passwords and different private data uncovered in previous knowledge breaches, revealed dozens of variations on electronic mail addresses utilized by Alexander I. Ukraincki over time. Most of these electronic mail addresses begin with some variation of “uai@” adopted by a website from one of many many Russian electronic mail suppliers (e.g., yandex.ru, mail.ru). [Full disclosure: Constella is currently an advertiser on this website].
However Constella additionally reveals these completely different electronic mail addresses all relied on a handful of passwords — mostly “2222den” and “2222DEN.” Each of these passwords have been used virtually solely previously decade by the one who registered greater than a dozen electronic mail addresses with the username “dennstr.”
The dennstr id results in a number of variations on the identical identify — Denis Strelinikov, or Denis Stranatka, from Ukraine, however these clues in the end led nowhere promising. And possibly that was the purpose.
Issues started trying brighter after I ran a search in DomainTools for web-site[.]ru’s unique WHOIS data, which reveals it was assigned in 2005 to a “non-public particular person” who used the e-mail deal with lycefer@gmail.com. A search in Constella on that electronic mail deal with says it was used to register practically two dozen domains, together with starovikov.ru and starovikov[.]com.
A cached copy of the contact web page for Starovikov[.]com reveals that in 2008 it displayed the non-public data for a Dmitry Starovikov, who listed his Skype username as “lycefer.”
Lastly, Russian incorporation paperwork present the corporate LLC Web site (web-site[.]ru)was registered in 2005 to 2 males, one among whom was named Dmitry Sergeevich Starovikov.
Bringing this full circle, Google says Starovikov is among the two operators of the Glupteba botnet:
The duvet web page for Google’s lawsuit in opposition to the alleged Glupteba botnet operators.
Mr. Starovikov didn’t reply to requests for remark. However attorneys for Starovikov and his co-defendant final month filed a response to Google’s criticism within the Southern District of New York, denying (PDF) their purchasers had any information of the scheme.
Regardless of the entire disruption brought on by Google’s authorized and technical meddling, AWM continues to be round and practically as wholesome as ever, though the service has been branded with a brand new identify and there are doubtful claims of latest house owners. Promoting buyer plans starting from $50 a day to almost $700 for “VIP entry,” AWM Proxy says its malware has been operating on roughly 175,000 methods worldwide over the past 24 hours, and that roughly 65,000 of those methods are presently on-line.
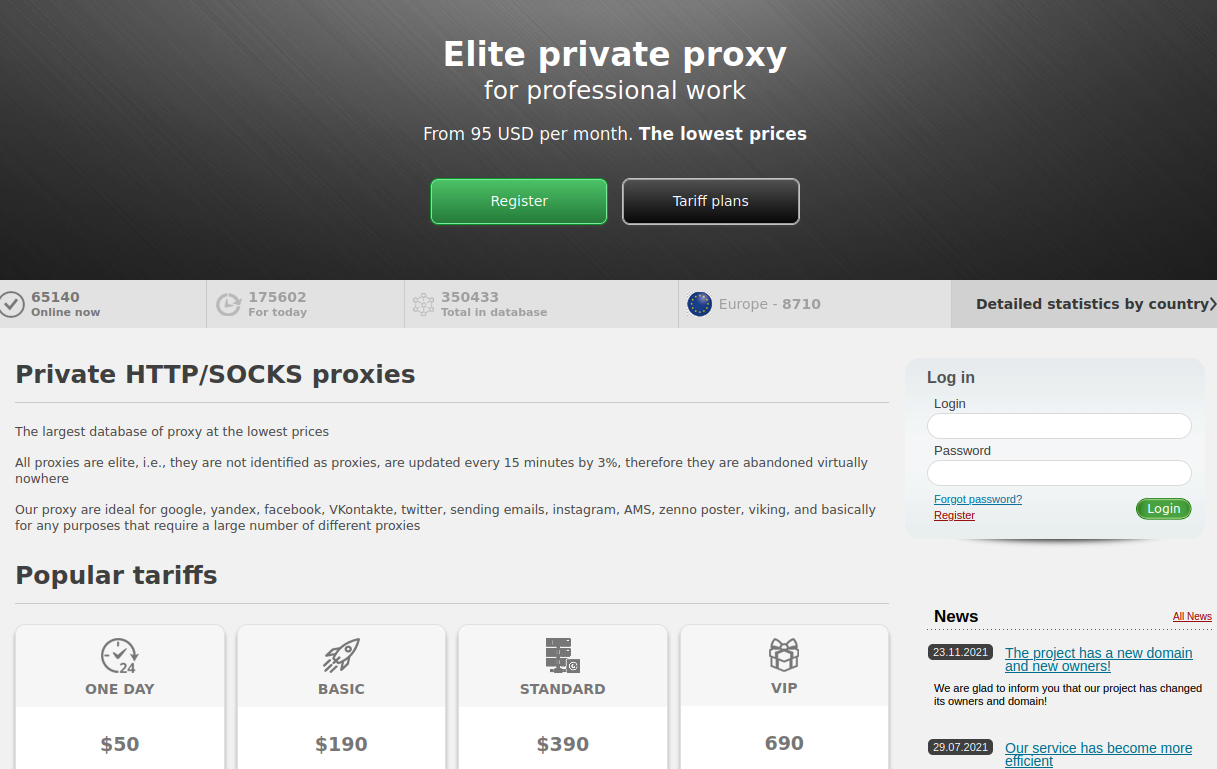
AWM Proxy, because it exists at this time.
In the meantime, the directors of RSOCKS lately alerted prospects that the service and any unspent balances will quickly be migrated over to a brand new location.
Many individuals appear to equate spending time, cash and energy to analyze and prosecute cybercriminals with the largely failed warfare on medicine, that means there may be an countless provide of up-and-coming crooks who will all the time fill in any gaps within the workforce each time cybercriminals face justice.
Whereas that could be true for a lot of low-level cyber thieves at this time, investigations like these present as soon as once more how small the cybercriminal underground actually is. It additionally reveals the way it makes a substantial amount of sense to focus efforts on concentrating on and disrupting the comparatively small variety of established hackers who stay the true pressure multipliers of cybercrime.










