It’s not information that 2024 has been a tumultuous yr on many fronts. For our second Energetic Adversary Report of 2024, we’re trying particularly at patterns and developments we famous throughout the first half of the yr (1H24). Although the yr itself was in some ways unremarkable on the floor for these charged with the safety of small- and medium-scale enterprises – the conflict between attackers and defenders raged on, as ever – we see some exceptional exercise just under that floor.
Key takeaways
- Abuse of built-in Microsoft companies (LOLbins) is up — approach up
- RDP abuse continues rampant, with a twist
- The ransomware scene: Banyans vs poplars
The place the information comes from
The info for this report is drawn from instances dealt with within the first half of 2024 by a) our external-facing IR group and b) the response group that handles important instances occurring amongst our Managed Detection and Response (MDR) prospects. The place acceptable, we examine findings from the 190 instances chosen for this report with knowledge amassed from earlier Sophos X-Ops casework, stretching again to the launch of our Incident Response (IR) service in 2020.
For this report, 80 p.c of the dataset was derived from organizations with fewer than 1000 staff. That is decrease than the 88 p.c in our final report; the distinction is primarily (however not totally) as a result of addition of MDR’s instances to the combo. Just below half (48%) of organizations requiring our help have 250 staff or fewer.
And what do these organizations do? As has been the case in our Energetic Adversary Studies since we started issuing them in 2021, the manufacturing sector was the almost definitely to request Sophos X-Ops response companies, although the proportion of consumers hailing from Manufacturing is down sharply, from 25 p.c in 2023 to 14 p.c within the first half of 2024. Building (10%), Training (8%), Data Expertise (8%), and Healthcare (7%) spherical out the highest 5. In whole, 29 totally different trade sectors are represented on this dataset. Additional notes on the information and methodology used to pick out instances for this report might be discovered within the Appendix.
The stability of the report analyzes our findings, as listed in the important thing takeaways above, and gives updates on a collection of points raised by earlier editions of the report. Evaluation of the total dataset for 2024 might be undertaken within the subsequent version of the report, slated for early 2025.
Born to run (natively): LOLbin use on a fast rise
LOLbins – abused-but-legitimate binaries already current on the machine or generally downloaded from professional sources related to the OS – have at all times been a part of the Energetic Adversary panorama. We distinction these to the findings we name “artifacts,” that are third-party packages introduced onto the system illegitimately by attackers (e.g., mimikatz, Cobalt Strike, AnyDesk). LOLbins are professional information, they’re signed, and when utilized in seemingly benign methods they’re much less probably to attract a system administrator’s consideration.
We noticed a modest improve this yr within the use and number of artifacts, and we’ll have a look at these adjustments later on this report. The rise in LOLbins, nonetheless, is arresting. (For the needs of this version of the report, we’re primarily specializing in binaries within the Microsoft Home windows working system, although we additionally see these abused in different OSes.) Within the first half of 2024, we discovered 187 distinctive Microsoft LOLbins used amongst our 190 instances – over a 3rd of them (64) showing simply as soon as in our dataset. This represents an increase of 51 p.c over 2023’s LOLbin numbers. The general rise in LOLbin counts since 2021 is proven in Determine 1.
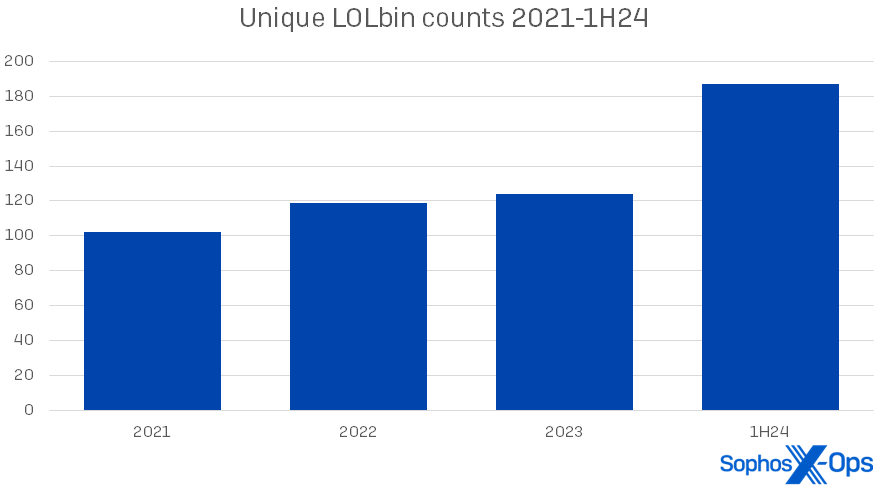
Determine 1: The abrupt rise in LOLbin use in 1H24 comes after years of gradual improve in utilization
Simply three years in the past, our 2021 statistics confirmed that artifacts had been greater than twice as widespread as LOLbins in our instances. Now the ratio is nearer to five:4, as proven in Determine 2.
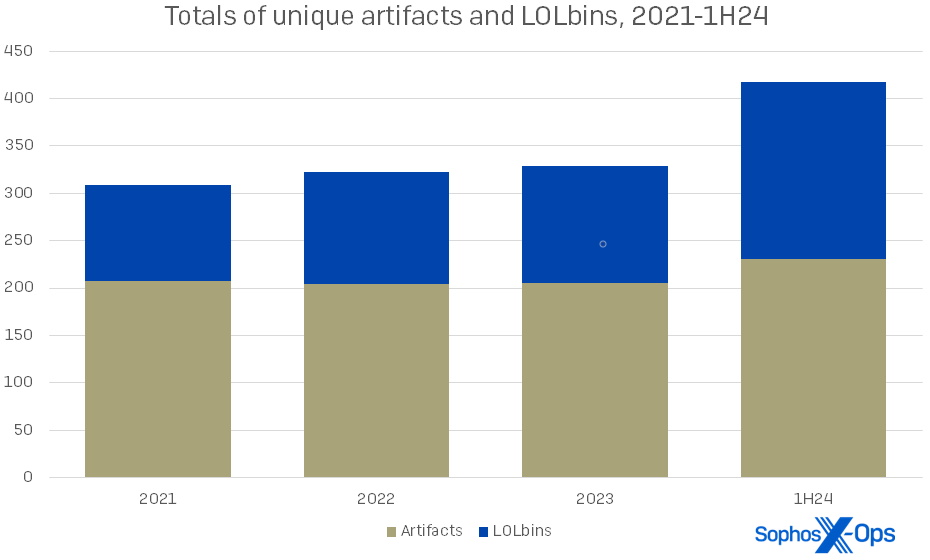
Determine 2: The usage of each artifacts and LOLbins is growing general, and attackers are throwing extra of each on the wall to see what sticks. In a specific incident this yr, the responding group famous 14 artifacts and 39 LOLbins in play
Which LOLbins are attackers utilizing? Main the pack as at all times is RDP, about which we’ll have extra to say within the subsequent part. We discovered 29 particular LOLbins in use in at the very least 10 p.c of instances; their names and prevalence are proven in Determine 3. This represents a considerable improve over final yr’s distribution, the place solely 15 of the 124 distinctive LOLbins noticed appeared in over 10 p.c of instances.
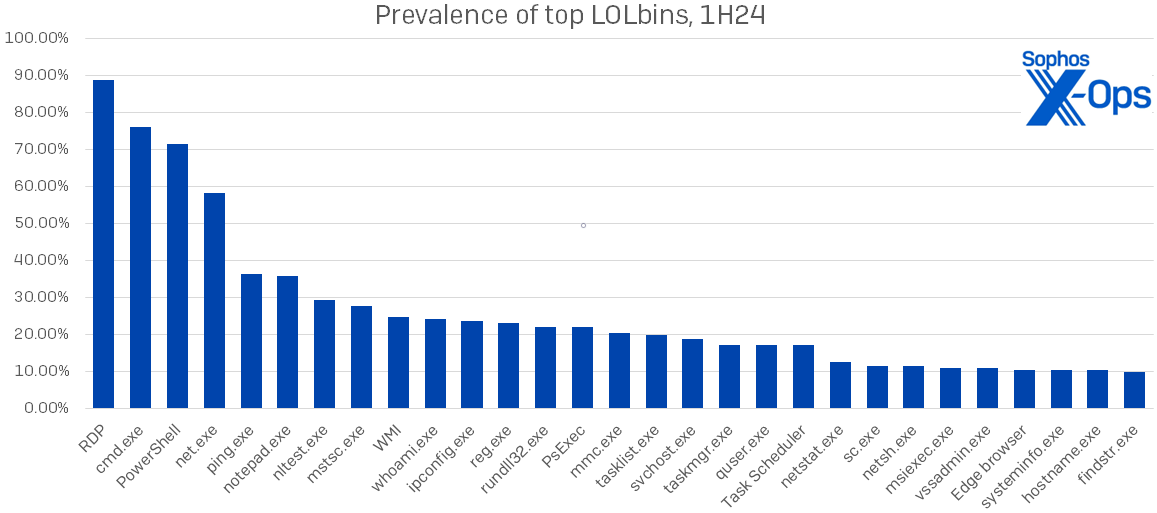
Determine 3: Essentially the most generally logged LOLbins of 1H24; all of those appeared in at the very least 10 p.c of instances
For probably the most half the names within the determine above aren’t any shock to common readers of the Energetic Adversary Report – RDP guidelines the panorama, with cmd.exe, PowerShell, and web.exe making their regular robust displaying. Nonetheless, we are able to see elevated use of even a few of these acquainted LOLbins in Determine 4, which additionally reveals the proportion improve in utilization for each LOLbin seen in over 10 p.c of 1H24 instances. Notice the prevalence of binaries used for discovery or enumeration – 16, by our depend.
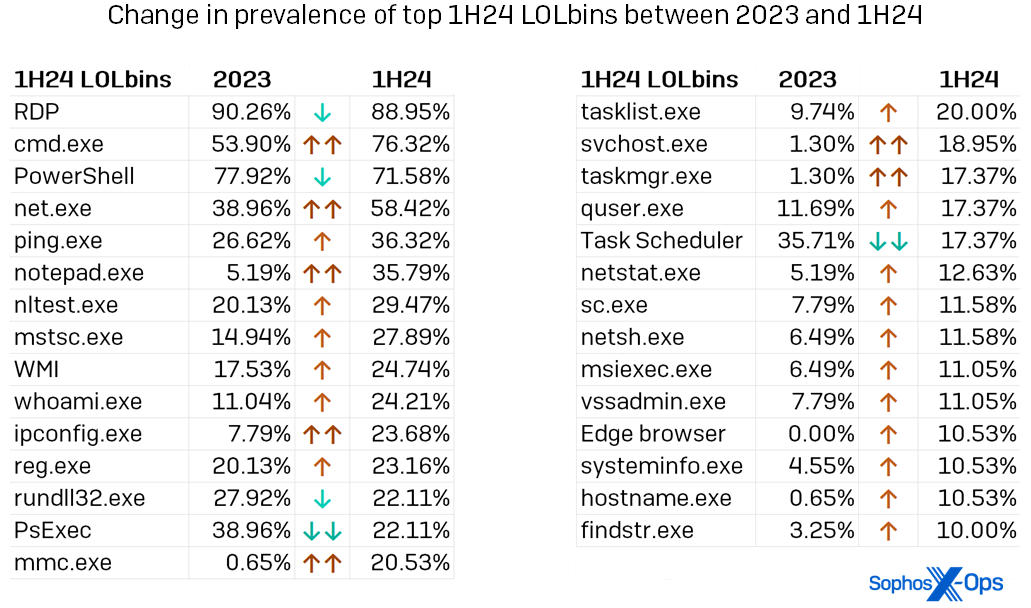
Determine 4: Of the highest 29 LOLbins we noticed in use throughout 1H24, solely 5 had been noticed much less often than they had been in 2023. (LOLbins for which utilization modified considerably – both 15 p.c greater or decrease than within the earlier yr’s knowledge – are indicated above with double arrows). Please be aware that within the context of this checklist, “Job Scheduler” contains each Job Scheduler and schtasks.exe, whereas WMI contains the now-deprecated WMIC
What’s a defender to do? First, this variation in tooling signifies that it isn’t sufficient to simply control your community for gadgets that don’t belong. Each LOLbin is not directly a part of the working system, from RDP right down to fondue.exe, tracert.exe, and time.exe (three of the one-use-only LOLbins we noticed within the knowledge). Greater than ever, it’s essential to know who’s in your community and what they need to be doing. If Alice and Bob from IT are doing issues with PowerShell, most likely okay. If Mallory from PR is doing issues with PowerShell, ask questions.
As well as, logging and well-informed community monitoring are key. At one level in our evaluation we requested ourselves whether or not the will increase we had been seeing had been maybe merely the results of incorporating the information from our MDR group. After normalizing the information we had been capable of conclude that they’re not, however we had been as soon as once more startled by the distinction having MDR-type eyes on the system makes on the subject of each preliminary entry and impression. (Extra on these in a minute.)
To study extra about LOLbins, together with capabilities of particular person binaries and the place they (normally) match into the MITRE ATT&CK framework, we suggest visiting the LOLBAS collaborative challenge on Github.
RDP (stands for Repeating the Rattling Drawback)
For a report that enjoys throwing in pop-music references, Energetic Adversary appears like a damaged document: RDP, RDP, RDP. As proven within the figures above, RDP is undefeated as a supply of infosecurity woe, with slightly below 89 p.c of the instances we noticed in 1H24 displaying some indication of RDP abuse.
Trying extra intently on the instances involving RDP, there’s not a lot change in whether or not assaults used RDP internally or externally. These statistics have been secure through the years, as proven in Determine 5.

Determine 5: In 2022 and 2023, there have been a number of instances through which attackers kicked over the traces of their RDP exercise so totally that the responding group couldn’t confidently discern precisely which actions had been profitable; 1H24 was higher in that facet at the very least
Trying simply exterior this report’s timeframe, the monotony of RDP abuse statistics was solely barely damaged in September by Microsoft’s announcement that the corporate is rolling out a multiplatform “Home windows App” (that is its title) designed to supply distant entry to Home windows 10 and 11 machines from “work or college accounts,” with RDP entry promised later. Nonetheless, regardless of the corporate’s claims of enhanced safety together with multifactor authentication functionality, most observers had been fast to explain Home windows App as primarily a rebrand of the Distant Desktop shopper. Whether or not our subsequent Energetic Adversary Report has comfortable information of a drop in RDP abuse or not, solely time will inform.
Shaking the tree: The poplars and banyans of ransomware
Turning our consideration now to ransomware, a stroll by the information on ransomware infections led to an attention-grabbing statement: In the case of attribution, the corollary between high-profile ransomware takedowns and diminished presence on our charts isn’t at all times as robust as one would hope.
In our expertise, some years have one dominant ransomware model that overshadows the others like the cover of a banyan tree, and different years distribute the ransomware instances comparatively evenly amongst a number of manufacturers, like a row of poplars. The distinction typically corresponds with authorized disruptions (“takedowns”) of high-profile ransomware teams. Nonetheless, the primary half of 2024 didn’t replicate this sample in our knowledge. LockBit was the dominant ransomware of 2023, however was the topic of a law-enforcement disruption in late February 2024. Regardless of that, LockBit remained the dominant ransomware seen by the IR group within the first half of the yr.
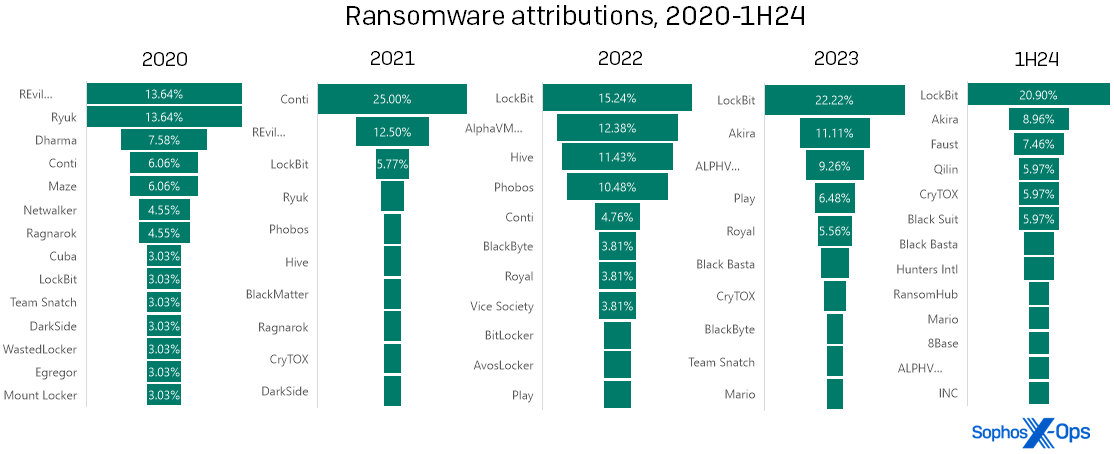
Determine 6: Poplar, banyan, poplar, banyan… banyan?! The sample we’ve noticed in ransomware attributions over the previous a number of years appears to have damaged down in 1H24 with LockBit… perhaps. (Two of the labels above are truncated for area; “REvil….” is extra absolutely “REvil / Sodinokibi,” whereas “ALPHV….” is “ALPHV/BlackCat”)
To be honest, authorized motion finally doesn’t make an enormous dent within the general ransomware scene – it disrupts the focused risk actor, however doesn’t completely cease a lot of the entities concerned. With each main authorized motion, the sheer variety of different manufacturers jockeying for place signifies that the hole is stuffed, after which some. Discover that Conti represented a mere 6 p.c of infections seen in 2020… after which first Ryuk (2020) and Revil (2021) had been hit by takedowns of the gang or, in Ryuk’s case, the Trickbot distribution system on which it relied. After that Conti (probably descended from Ryuk) flourished for a yr (2021), however dropped to single-digit prevalence ranges by the tip of 2022. In LockBit’s case, the proprietor of the model tried a mid-2024 “comeback,” rebuilding its infrastructure and even restarting its weblog. (A model of LockBit’s ransomware builder was additionally famously leaked by a disgruntled affiliate in September 2022, which can have an effect on its prevalence.)
What’s subsequent? First, it’s attainable that the sample will resolve itself within the knowledge from the second half of the yr – that’s, the “banyan” will morph right into a “poplar” as predicted. Within the month or so after the LockBit takedown, Sophos’ MDR and IR groups, respondents to our 2024 State of Ransomware survey, and different trade observers all reported a lower in LockBit infections. These bounced up once more for some time in Could; it’s commonplace to see that type of echo impact after a disruption by legislation enforcement, however finally the echo does fade.
Second, the title of the subsequent ubiquitous ransomware might be someplace within the determine above, which signifies that even when system directors won’t wish to place bets on any specific model, the offender is probably going already on defenders’ radar. These seeking to parry the following assault on their methods can begin by maintaining a tally of information regarding each recognized names and up-and-comers. It’s completely cheap to rejoice that creatures like Mikhail Matveev and Ekaterina Zhdanova are going through jail time, however the music isn’t over.
Total, ransomware infections had been down barely within the first half of the yr. For IR, 61.54 p.c of instances dealt with concerned ransomware, in comparison with 70.13 p.c in 2023. (The slack was greater than taken up by community breaches, which almost doubled their incidence in IR instances – 34.62 p.c in 1H24, in comparison with 18.83 p.c in 2023. Shut examination of all knowledge obtainable to us causes us to suspect that the drop, although actual, gained’t be as pronounced when the total yr’s numbers are analyzed.)
In the meantime, MDR dealt with primarily community breaches in 1H24, with simply 25.36 p.c of their instances chalked as much as ransomware. It ought to be famous that MDR, as a result of nature of the service, tends to come across and include ransomware far earlier in its an infection cycle than the IR group does – normally, previous to encryption or deployment, which signifies that they by no means rise to the extent of requiring response of the kind the Energetic Adversary Report covers. (Sadly, “assault detected” for the IR group usually means “the shopper realized that they may be below assault after they acquired a ransom be aware and all their computer systems had been bricked.”) For the MDR group, LockBit was already flattening out in prevalence by the tip of June, with 17.14 p.c of their ransomware attributions chalked as much as that model and each Akira and BlackSuit shut on its heels at 11.43 p.c apiece. (And finishing the circle, each Akira and BlackSuit are descendants of… Conti. Identical music, subsequent verse.)
Comin’ out and in of your life: Preliminary entry and impression
The third and fourteenth steps of the MITRE ATT&CK Matrix invariably appeal to reader curiosity; we now have even written in a earlier report in regards to the variations we noticed between two very related instances dealt with by our IR and MDR processes. For this report, we’ll focus our MITRE-related evaluation on the classes themselves, Preliminary Entry and Affect.
Preliminary Entry within the first half of 2024 appeared a lot because it did in earlier years. As one would count on from the RDP statistics, Exterior Distant Companies assault methods dominated the class, representing 63.16 p.c of instances in comparison with 2023’s 64.94 p.c. Legitimate Accounts (59.47%, down from 61.04%) and Exploit [of] Public-facing Software (30%, up from 16.88%) spherical out the highest three. (Since instances might exhibit many mixtures of initial-access methods, the chances won’t ever add as much as 100.)
The scenario is extra attention-grabbing with Affect, the ultimate class within the MITRE matrix. After years of dominating the Affect class by factoring right into a minimal of two-thirds of all instances, Knowledge Encrypted for Affect (a typical step in ransomware assaults) tumbles to second place with 31.58 p.c, simply above up-and-comer Knowledge Manipulation (30%) and trailing No Affect at 38.95 p.c.
Now we have written up to now about “No Affect” which means one thing a bit totally different on the subject of ATT&CK. The most recent version of ATT&CK lists fourteen methods that it acknowledges as “Affect.” These methods are evolving to maintain tempo with present realities of ransomware payouts and misplaced productiveness, and we now have refined our evaluation of earlier case knowledge to replicate these enhancements (thus retroactively trimming down the variety of instances for which the impression discovering is No). However it could be an excessive amount of to ask that the ATT&CK class embody intangibles reminiscent of reputational loss or workers burnout. Incident responders are all too conscious that no person needs to want their companies; although “no” impression sounds refreshing and nice, and although most of the MDR-handled instances had been certainly triggered in time to dam would-be attackers from succeeding of their goals, “No Affect” doesn’t imply there was no impression – it signifies that no matter occurred is past ATT&CK’s vocabulary to explain.
The place are they now: Checking on earlier AAR findings
In an try to preserve this version of the report comparatively quick, there are a number of subjects of earlier curiosity on which we’ll contact briefly, upfront of our full-year 2024 report.
Dwell time: Dwell-time numbers have been dropping, as we confirmed in our first 2023 report. The 1H24 numbers point out that this decline has leveled off and even barely reversed for instances dealt with by our Incident Response group. For ransomware, median dwell instances hover at 5.5 days; factoring in all different sorts of incidents, the median lingers at 8 days. Although we don’t but have earlier years’ MDR instances obtainable to the report group for evaluation, a have a look at their 1H24 knowledge reveals what a distinction monitoring makes – medians of three days for ransomware and in the future for every type of incidents. For the reason that MDR instances requiring incident response are a really small sliver of all of the exercise MDR sees day-to-day, the impact of getting watchful eyes in place is left as an train for the reader.
Time-to-AD: In our second 2023 report we appeared on the time it takes for attackers to achieve management of the goal’s Energetic Listing — a degree at which one can fairly say that the goal is compromised — and the interval from when the attacker positive aspects management of AD to when the assault is detected. That is one other statistic for which MDR’s knowledge varies radically from that compiled by IR. The IR numbers fluctuated in 1H24 from these of years previous, with attackers taking about two hours longer to achieve Energetic Listing (15.35 hours in 2023, 17.21 hours in 1H24). An obvious lower in dwell time between AD acquisition and assault detection (29.12 hours in 1H24, down from 48.43 hours in 2023) is attention-grabbing and will advantage scrutiny within the subsequent report, if a bigger accumulation of information reveals it to be an actual growth.
We are going to be aware that the three variations of Energetic Listing we most often noticed compromised had been Server 2019 (43%), Server 2016 (26%), and Server 2012 (18%), collectively accounting for 87 p.c of compromised AD servers. All three of those variations at the moment are out of mainstream Microsoft help, although Patch Tuesday launch info nonetheless states which updates would apply to every model. In case your methods are working on drained variations of Server, contemplate these numbers your wake-up name to replace. (For many who comply with our Patch Tuesday protection, we now have began this month to relay extra info on exactly which variations of Server are affected by every month’s patches.)
Compromised credentials: We additionally spotlighted the rise in compromised credentials as a root explanation for assaults in our second 2023 report. In 2023, 56 p.c of all incidents had compromised credentials as their root trigger. Within the first half of 2024, that dominance was dialed again considerably. Although compromised credentials had been nonetheless the main root trigger general for 2024, that quantity was led primarily by the IR instances, as proven in Determine 7. For MDR prospects, exploited vulnerabilities led the root-cause leaderboard, although by lower than one p.c.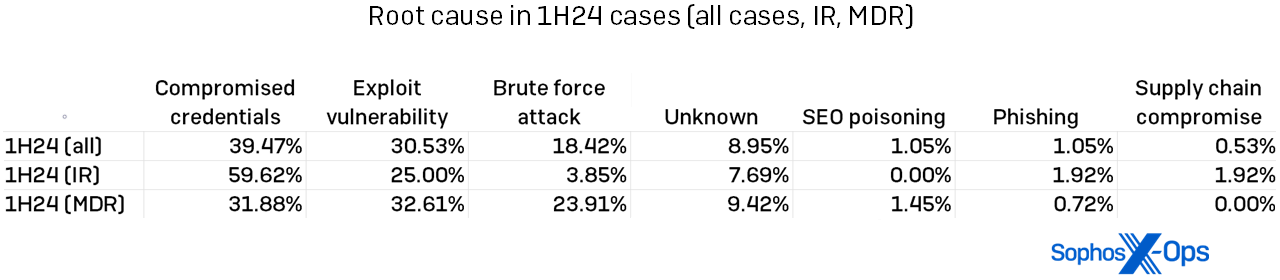
Determine 7: The basis causes of IR-handled and MDR-handled incidents assorted, with instances extra equally distributed amongst MDR and compromised credentials “successful” in a stroll for IR
Only a music about artifacts earlier than I am going
As talked about above, our knowledge discovered not solely LOLbins however third-party artifacts on the rise within the instances we noticed within the first half of 2024. The rise in artifact utilization is just not as hanging as that of the LOLbins, however a number of features bear additional dialogue.
First, the numbers are up, although barely. We noticed 230 distinctive artifacts on focused methods within the first half of 2024, in comparison with 205 in all of 2023 – a 12 p.c improve. (By the use of comparability, 2022 had 204 artifacts; 2021 had 207.)
Second, the names of probably the most generally discovered artifacts don’t a lot fluctuate from yr to yr, as proven in Determine 8. We did be aware that Cobalt Strike utilization continues the retreat it started in 2023, current in simply 13.68 p.c of infections within the first half. (In earlier years, Cobalt Strike was at one level current in almost half the instances, and it nonetheless sits atop the leaderboard of all-time artifact findings. Higher defender detections for Cobalt Strike are probably resulting in this drop.) 127 artifacts seem solely as soon as within the 1H24 knowledge, which is lower than 2023’s 102 single-use findings.
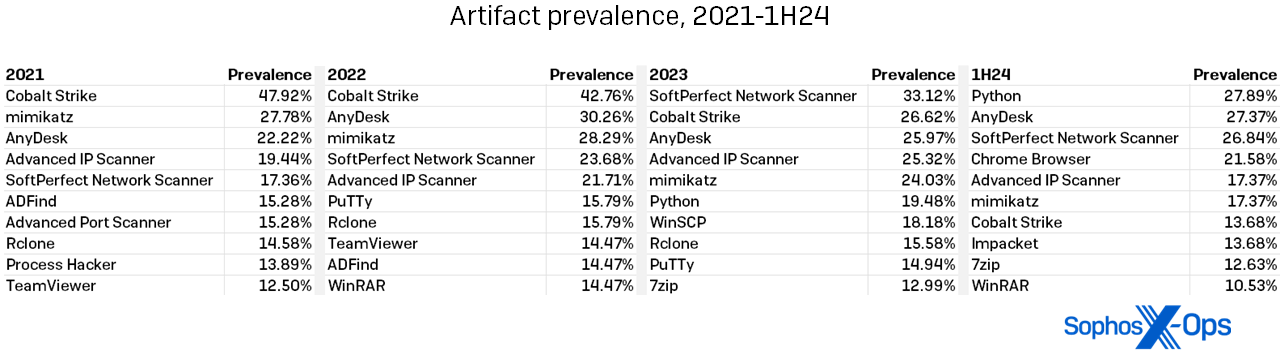
Determine 8: The years-long development towards extra various artifact use continues, with no single artifact occurring in additional than 30 p.c of instances within the first half of 2024
A defender studying that over half of all artifacts are single-use instruments might maybe despair of catching all the pieces an attacker would possibly throw at them. We’d encourage that defender to take a look at the desk above and keep in mind that the supporting solid might change, however the “stars” of the Artifacts galaxy all shine on. The desk above reveals each artifact that appeared in over 10.00 p.c of instances over the course of 4 years. Maintaining a relentless eye out for these packages is each doable and helpful. Take into account creating and making use of a default-block coverage for functions in your methods; this requires a good quantity of labor up entrance, however saves hassle as attackers broaden their tool-usage repertoire.
Conclusion
It has been a rare reward to the AAR evaluation and writing group to see how the statistics modified as we integrated the big tranche of information from Sophos X-Ops’ MDR group with the years-deep database from our IR colleagues. The method of interrogating the information led us to each exceptional panorama adjustments – who knew that LOLbins may very well be thrilling? – and to patterns reminiscent of RDP abuse that stay immune to finest practices reminiscent of vigilant monitoring.
Above all, although, we stay bemused by the variety of instances that hinged on fundamentals – not simply the three immortalized within the Sophos “haiku”
however easy sample consciousness which may have prevented prospects from ever turning into a part of a dataset reminiscent of this. It’s our hope {that a} shut, tight snapshot of the latest Energetic Adversary Report panorama aids practitioners to sharpen their concentrate on the basics that may preserve us all safer and safer.
Acknowledgements
The authors want to thank Chester Wisniewski, Anthony Bradshaw, and Matt Wixey for his or her contributions to the AAR course of.
Appendix: Demographics and methodology
For this report, we targeted on 190 instances that may very well be meaningfully parsed for helpful info on the state of the adversary panorama as of the primary half of 2024. Defending the confidential relationship between Sophos and our prospects is after all our first precedence, and the information herein has been vetted at a number of levels throughout this course of to make sure that no single buyer is identifiable by this knowledge – and that no single buyer’s knowledge skews the mixture inappropriately. When unsure a couple of particular case, we excluded that buyer’s knowledge from the dataset.
We should always make point out of a multi-year case that concerned our MDR group. That case, which concerned nation-state exercise in a number of areas, has been coated elsewhere as “Crimson Palace.” Although fascinating and in some ways a bellwether for particular assault techniques we’ve seen elsewhere since, it’s in a number of methods such an outlier to the overwhelming majority of the Energetic Adversary dataset that we’ve chosen to depart its numbers out of the report.
Determine A1: Right here, there, and all over the place — it’s Sophos X-Ops MDR and IR world wide (Map technology courtesy mapchart.web)
The next 48 nations and different areas are represented within the 1H24 knowledge analyzed for this report:
| Angola | Honduras | Poland |
| Argentina | Hong Kong | Qatar |
| Australia | India | Romania |
| Austria | Israel | Saudi Arabia |
| Bahamas | Italy | Singapore |
| Bahrain | Japan | Slovenia |
| Belgium | Kenya | Somalia |
| Botswana | Kuwait | South Africa |
| Brazil | Malaysia | Spain |
| Canada | Mexico | Sweden |
| Chile | Netherlands | Switzerland |
| Colombia | New Zealand | Taiwan |
| Egypt | Nigeria | Thailand |
| Finland | Panama | United Arab Emirates |
| France | Papua New Guinea | United Kingdom |
| Germany | Philippines | United States of America |
Industries
The next 29 industries are represented within the 1H24 knowledge analyzed for this report:
| Promoting | Monetary | MSP/Internet hosting |
| Agriculture | Meals | Non-profit |
| Structure | Authorities | Pharmaceutical |
| Communication | Healthcare | Actual property |
| Building | Hospitality | Retail |
| Training | Data Expertise | Companies |
| Electronics | Authorized | Transportation |
| Vitality | Logistics | Utilities |
| Engineering | Manufacturing | Wholesale |
| Leisure | Mining |
Methodology
The info on this report was captured over the course of particular person investigations undertaken by Sophos’ X-Ops Incident Response and MDR groups. For this second report of 2024, we gathered case info on all investigations undertaken by the groups within the first half of the yr and normalized it throughout 63 fields, analyzing every case to make sure that the information obtainable was acceptable intimately and scope for combination reporting as outlined by the main focus of the proposed report. We additional labored to normalize the information between our MDR and IR reporting processes.
When knowledge was unclear or unavailable, the authors labored with particular person IR and MDR case results in clear up questions or confusion. Incidents that might not be clarified sufficiently for the aim of the report, or about which we concluded that inclusion risked publicity or different potential hurt to the Sophos-client relationship, had been put aside. We then dissected every remaining case’s timeline to achieve additional readability on such issues as preliminary ingress, dwell time, exfiltration, and so forth. We retained 190 instances, and people are the muse of the report.










