The Russia-based cybercrime group dubbed “Fin7,” identified for phishing and malware assaults which have price sufferer organizations an estimated $3 billion in losses since 2013, was declared lifeless final 12 months by U.S. authorities. However specialists say Fin7 has roared again to life in 2024 — organising hundreds of internet sites mimicking a variety of media and expertise corporations — with the assistance of Stark Industries Options, a sprawling internet hosting supplier that could be a persistent supply of cyberattacks in opposition to enemies of Russia.
In Might 2023, the U.S. lawyer for Washington state declared “Fin7 is an entity no extra,” after prosecutors secured convictions and jail sentences in opposition to three males discovered to be high-level Fin7 hackers or managers. This was a daring declaration in opposition to a bunch that the U.S. Division of Justice described as a felony enterprise with greater than 70 folks organized into distinct enterprise models and groups.
The primary indicators of Fin7’s revival got here in April 2024, when Blackberry wrote about an intrusion at a big automotive agency that started with malware served by a typosquatting assault concentrating on folks looking for a well-liked free community scanning instrument.
Now, researchers at safety agency Silent Push say they’ve devised a solution to map out Fin7’s quickly regrowing cybercrime infrastructure, which incorporates greater than 4,000 hosts that make use of a variety of exploits, from typosquatting and booby-trapped advertisements to malicious browser extensions and spearphishing domains.
Silent Push stated it discovered Fin7 domains concentrating on or spoofing manufacturers together with American Specific, Affinity Vitality, Airtable, Alliant, Android Developer, Asana, Bitwarden, Bloomberg, Cisco (Webex), CNN, Costco, Dropbox, Grammarly, Google, Goto.com, Harvard, Lexis Nexis, Meta, Microsoft 365, Midjourney, Netflix, Paycor, Quickbooks, Quicken, Reuters, Areas Financial institution Onepass, RuPay, SAP (Ariba), Trezor, Twitter/X, Wall Avenue Journal, Westlaw, and Zoom, amongst others.
Zach Edwards, senior menace analyst at Silent Push, stated lots of the Fin7 domains are innocuous-looking web sites for generic companies that generally embrace textual content from default web site templates (the content material on these websites usually has nothing to do with the entity’s said enterprise or mission).
Edwards stated Fin7 does this to “age” the domains and to offer them a optimistic or a minimum of benign popularity earlier than they’re ultimately transformed to be used in internet hosting brand-specific phishing pages.
“It took them six to 9 months to ramp up, however ever since January of this 12 months they’ve been buzzing, constructing a large phishing infrastructure and ageing domains,” Edwards stated of the cybercrime group.
In typosquatting assaults, Fin7 registers domains which are much like these for in style free software program instruments. These look-alike domains are then marketed on Google in order that sponsored hyperlinks to them present up prominently in search outcomes, which is normally above the reputable supply of the software program in query.
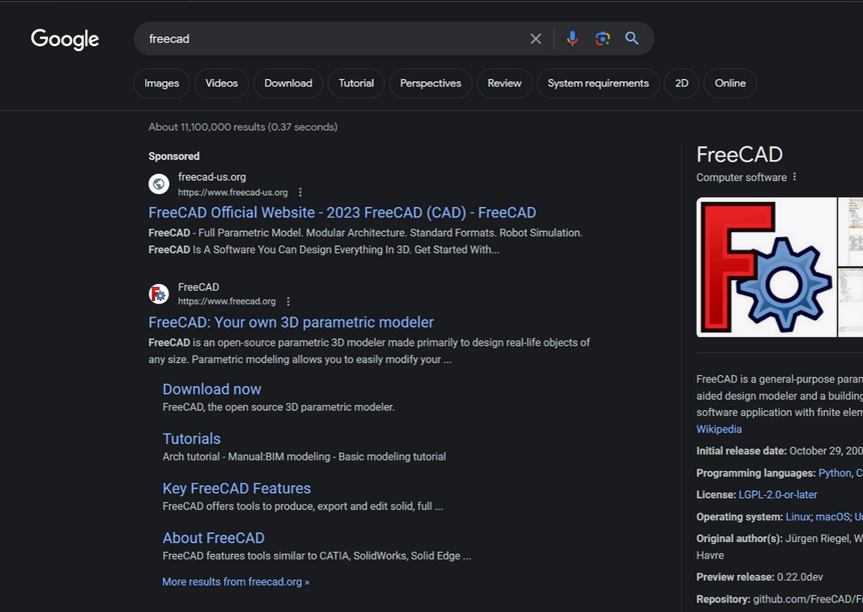
A malicious website spoofing FreeCAD confirmed up prominently as a sponsored end in Google search outcomes earlier this 12 months.
In keeping with Silent Push, the software program at present being focused by Fin7 consists of 7-zip, PuTTY, ProtectedPDFViewer, AIMP, Notepad++, Superior IP Scanner, AnyDesk, pgAdmin, AutoDesk, Bitwarden, Relaxation Proxy, Python, Elegant Textual content, and Node.js.
In Might 2024, safety agency eSentire warned that Fin7 was noticed utilizing sponsored Google advertisements to serve pop-ups prompting folks to obtain phony browser extensions that set up malware. Malwarebytes blogged a few related marketing campaign in April, however didn’t attribute the exercise to any explicit group.
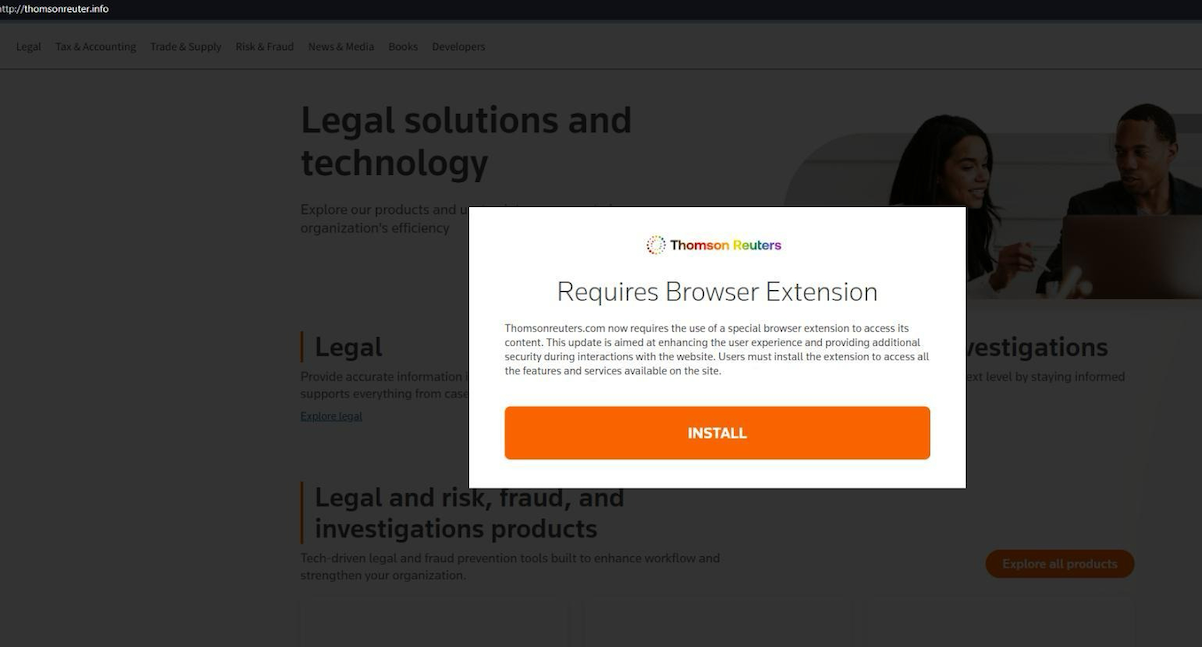
A pop-up at a Thomson Reuters typosquatting area telling guests they should set up a browser extension to view the information content material.
Edwards stated Silent Push found the brand new Fin7 domains after a listening to from a company that was focused by Fin7 in years previous and suspected the group was as soon as once more energetic. Trying to find hosts that matched Fin7’s identified profile revealed only one energetic website. However Edwards stated that one website pointed to many different Fin7 properties at Stark Industries Options, a big internet hosting supplier that materialized simply two weeks earlier than Russia invaded Ukraine.
As KrebsOnSecurity wrote in Might, Stark Industries Options is getting used as a staging floor for wave after wave of cyberattacks in opposition to Ukraine which were tied to Russian navy and intelligence businesses.
“FIN7 rents a considerable amount of devoted IP on Stark Industries,” Edwards stated. “Our analysts have found quite a few Stark Industries IPs which are solely devoted to internet hosting FIN7 infrastructure.”
Fin7 as soon as famously operated behind faux cybersecurity corporations — with names like Combi Safety and Bastion Safe — which they used for hiring safety specialists to assist in ransomware assaults. One of many new Fin7 domains recognized by Silent Push is cybercloudsec[.]com, which guarantees to “develop what you are promoting with our IT, cyber safety and cloud options.”
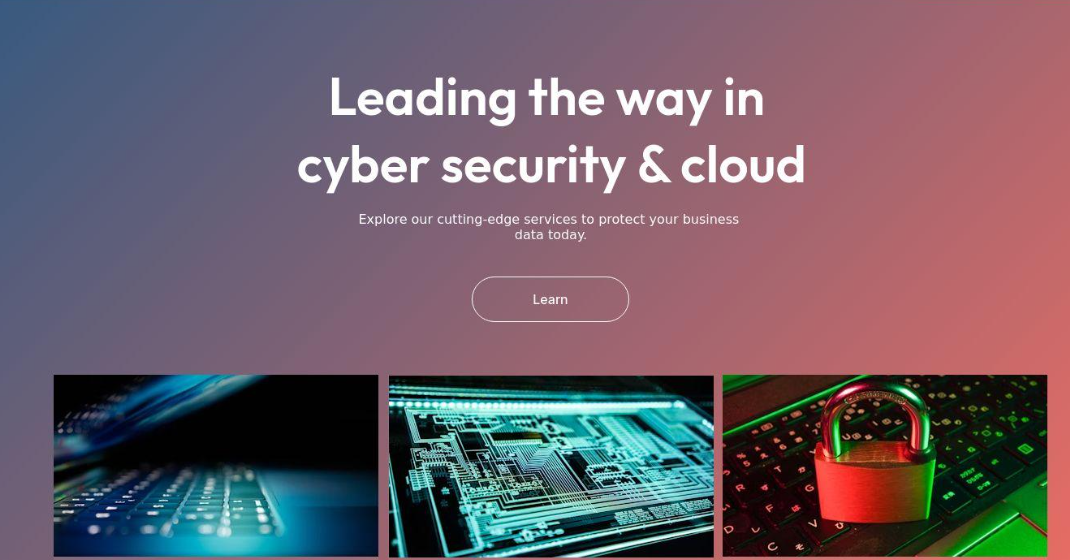
The faux Fin7 safety agency Cybercloudsec.
Like different phishing teams, Fin7 seizes on present occasions, and for the time being it’s concentrating on vacationers visiting France for the Summer season Olympics later this month. Among the many new Fin7 domains Silent Push discovered are a number of websites phishing folks looking for tickets on the Louvre.
“We consider this analysis makes it clear that Fin7 is again and scaling up rapidly,” Edwards stated. “It’s our hope that the regulation enforcement group takes discover of this and places Fin7 again on their radar for added enforcement actions, and that fairly a couple of of our rivals will have the ability to take this pool and broaden into all or a very good chunk of their infrastructure.”
Additional studying:
Stark Industries Options: An Iron Hammer within the Cloud.
A 2022 deep dive on Fin7 from the Swiss menace intelligence agency Prodaft (PDF).










