Cybercriminals are utilizing a wider-than-ever vary of malicious paperwork to unfold malware and acquire preliminary entry to focus on techniques, in line with HP Wolf Safety.
Alex Holland, principal menace researcher within the HP Safety Lab, informed Infosecurity that menace actors have not too long ago shifted their focus.
They’re now prioritizing script-based phishing methods over approaches based mostly on conventional malicious paperwork, he stated forward of the launch of HP Wolf Safety’s Risk Insights Report Q2 2024.
Leveraging Archive Recordsdata in Phishing Campaigns
“For the previous two years, we’ve got seen a motion away from utilizing maldocs, Microsoft Workplace paperwork containing malicious macros, in the direction of leveraging interpreted script languages, akin to VBScript and JavaScript,” Holland defined.
Sometimes, menace actors would mix this living-off-the-land phishing method with delivering encrypted archive recordsdata.
“With this method, as a substitute of sending an hooked up doc that features a malicious macro infecting the goal system, menace actors would ship an archive file that features hidden malicious VBScript or JavaScript code alongside the file that the sufferer needs to obtain.”
HP Wolf Safety’s quarterly report reveals that 39.23% of malware deliveries got here from an archive file within the second quarter of 2024, in comparison with 27.89% within the earlier reported interval.
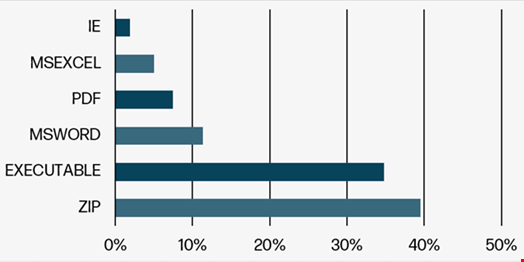
This method, which Holland considers of a better sophistication degree than conventional phishing methods, is made attainable by the excessive variety of archive file codecs that can be utilized.
“Though most individuals would solely know the principle codecs, akin to WinZip, 7-zip or WinRar, we’ve got present in our newest report that menace actors have used 50 completely different archive file codecs to deploy phishing campaigns,” Holland famous.
He added that that is partly as a result of Home windows 11 helps extra archive file codecs than its predecessors.
“We suggest that organizations lock down archive file codecs they’re not utilizing to cut back the assault floor,” he stated.
Proof of AI-Generated Malicious Code
Different findings from the report embrace:
- Phishing campaigns utilizing an intensive vary of vectors to contaminate victims, together with malicious PDF paperwork and SVG pictures
- One malvertising marketing campaign utilizing ChromeLoader, a malicious browser extension that targets Google Chrome and different Chromium-based browsers to redirect customers to undesirable web sites, typically these selling ads or malicious content material
- HP Wolf’s first proof of generative AI being utilized in a malicious marketing campaign
This latter discovering refers to a marketing campaign concentrating on French audio system utilizing VBScript and JavaScript that HP Safety Lab researchers consider to have been written with the assistance of GenAI.
Patrick Schläpfer, one other principal menace researcher within the HP Safety Lab, defined how his crew made this evaluation: “The construction of the scripts, feedback explaining every line of code, and the selection of native language perform names and variables are sturdy indications that the menace actor used GenAI to create the malware.”
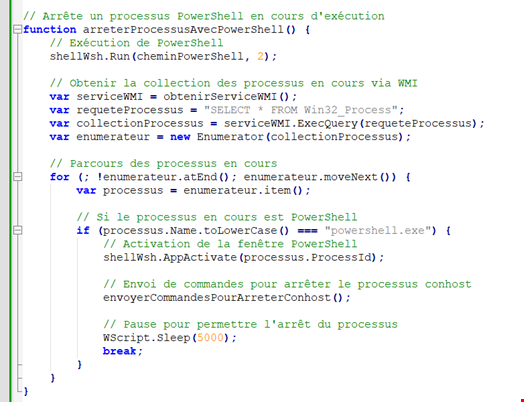
“The assault infects customers with the freely accessible AsyncRAT malware, an easy-to-obtain infostealer that may report sufferer’s screens and keystrokes. The exercise reveals how GenAI is decreasing the bar for cybercriminals to contaminate endpoints,” Schläpfer stated.










