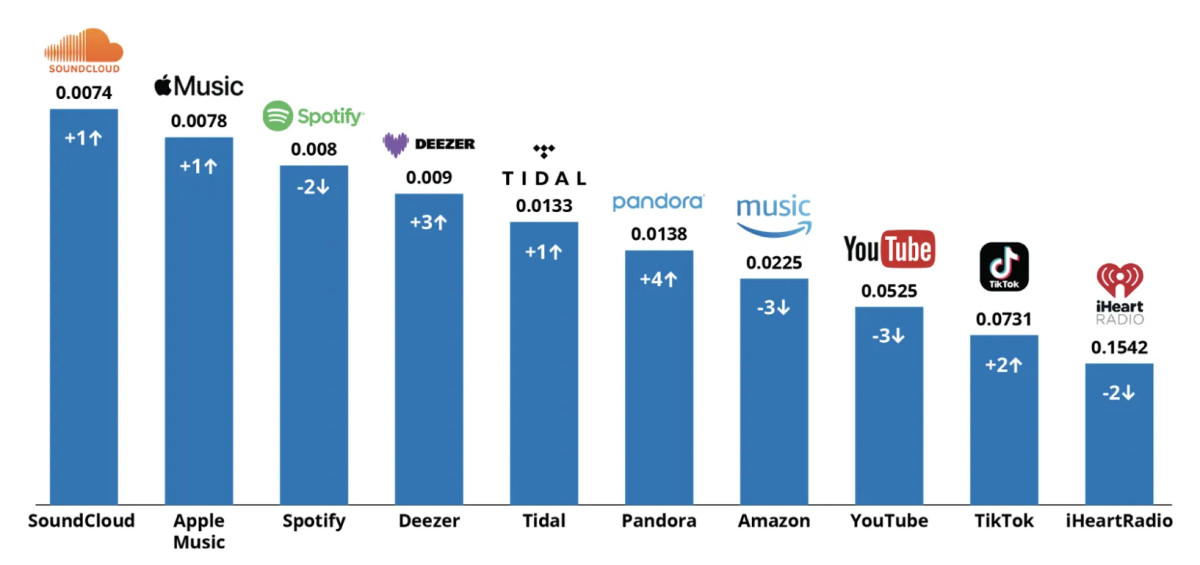
The Trigona ransomware menace actors are waging a marketing campaign towards Microsoft SQL database servers as a result of lots of them have exterior connections and weak passwords, leaving them open targets for brute pressure or dictionary assaults.
These weak MS-SQL servers had been designated as “poorly managed” by AhnLab Safety’s new alert about Trigona’s nefarious actions.
“If a menace actor manages to log in, management over the system can be handed to them, permitting them to put in malware or execute malicious instructions,” the report stated.
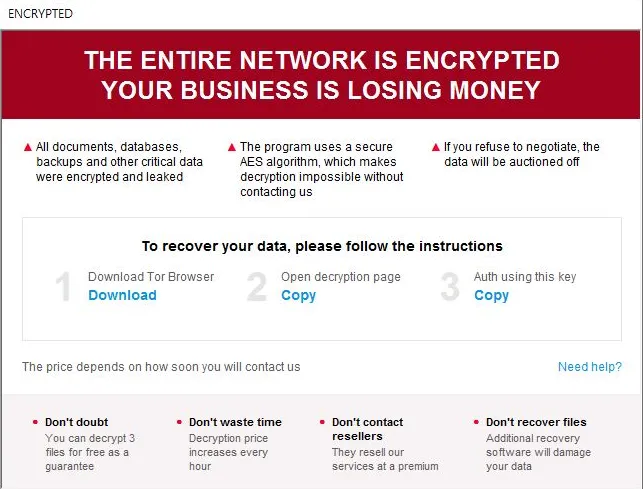
They’re fashionable repeat targets too, and never only for Trigona: In a single occasion noticed by AhnLab researchers, credentials for a breached MS-SQL server had been compromised by a number of menace actors, leaving traces of varied ransomware strains, Remcos RAT, and coinminers, the report stated.Moreover, MS-SQL will be put in on each Home windows SQL servers and desktop environments.
“For instance, there are instances the place MS-SQL is put in alongside sure enterprise useful resource planning (ERP) and work-purpose options throughout their set up course of,” the Trigona ransomware report added. “Due to this, Home windows servers and Home windows desktop environments can each be focused for MS-SQL server assaults.”
AhnLab Safety famous Trigona is a comparatively new ransomware group, first noticed final October.