Mitigations
OWASP recommends particular mitigations along with these mentioned above, together with strict surroundings isolation for NHIs, making use of the precept of least privilege, implementing environment-specific entry controls, and segregating infrastructure for delicate sources. Once more, the theme right here is mitigating systemic impacts and limiting them to particular environments by these mitigating controls and measures.
NHI threat No. 9: Reusing NHIs
Credential reuse has lengthy been one thing practitioners have cautioned towards however has nonetheless made its manner into varied compliance frameworks, greatest practices guides, and extra. That’s the reason it’s unsurprising to see it listed right here as a threat issue for NHIs.
OWASP
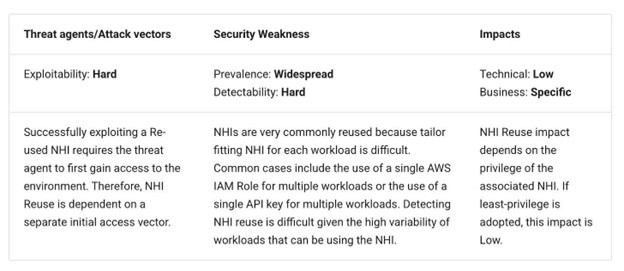
Because the desk above mentions, tailoring granular permissions for every NHI might be sophisticated, so organizations could default to reusing NHIs with broad permissions. This makes them compelling targets for exploitation with widespread ramifications for influence if compromised.
OWASP discusses how NHIs, reminiscent of service accounts, API keys, and machine credentials, are basic to fashionable functions, companies, authentication, and authorization.
Suppose organizations are reusing NHIs throughout a number of functions and companies. In that case, the potential for influence is important — it could actually result in vulnerability/assault chaining and widespread influence for a corporation if one of many NHIs that’s reused is compromised, particularly whether it is overprivileged (NHI5). There’s a lack of surroundings isolation (NHI8).
OWASP supplies examples reminiscent of reusing Kubernetes service accounts, sharing API keys between functions, and reusing cloud credentials reminiscent of AWS IAM Roles throughout completely different companies and sources.
Mitigations
To mitigate these dangers, OWASP recommends assigning distinctive NHIs to every software or service and the surroundings, implementing the precept of least privilege, and auditing and reviewing the usage of NHIs.
NHI threat No. 10: Human use of NHI
NHIs, reminiscent of service accounts, API tokens, workload identities, and secrets and techniques, allow programmatic entry to functions and companies. That mentioned, as OWASP discusses, it isn’t unusual for builders or customers to misuse NHIs for handbook duties quite than the unique intent of automated actions and workflows.
OWASP
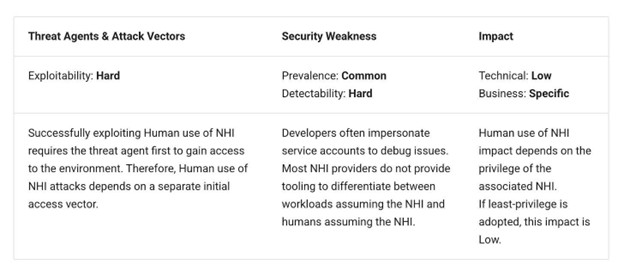
This poses a number of dangers as a result of human actions may very well be perceived as programmatic, limiting auditing and monitoring, protecting up actions by benign insiders, and even insider threats, and, most notably, potential attackers.
OWASP cites instance eventualities reminiscent of directors utilizing service account credentials, builders executing instructions with NHIs, sharing API tokens amongst workforce members, and even attackers leveraging NHIs for persistence.
Mitigations
The ultimate set of mitigations for the least threat within the OWASP NHI Prime 10 entails utilizing devoted identities, auditing and monitoring NHI exercise (one we’ve seen a number of instances), utilizing context-aware entry controls, and educating builders and directors on the chance of human use of NHIs. These measures present technical and cultural controls to restrict the human use of NHIs and their related dangers.










