Software program provide chain safety continues to be a crucial subject to the cybersecurity and software program trade, and for good purpose — from continued assaults towards giant software program distributors to attackers’ malicious concentrate on the open-source software program ecosystem by attackers it’s entrance and middle for many CISOs and safety practitioners. Fortunately, organizations proceed to provide stable steering to assist practitioners mitigate software program provide chain dangers. The most recent publication, “Securing the Software program Provide Chain: Really helpful Practices for Managing Open-Supply Software program and Software program Payments of Materials,” comes from the US Nationwide Safety Company (NSA).
It additionally builds on earlier publications such because the White Home Cybersecurity Government Order (EO) and memos and forthcoming necessities for Federal companies, such because the Workplace of Administration and Finances’s (OMB) memos 22-18 and 23-16, which require software program suppliers promoting to the US federal authorities to self-attest to aligning with publications such because the Nationwide Institute of Requirements and Know-how’s (NIST) Safe Software program Growth Framework (SSDF) and even offering SBOMs in some instances.
Whereas the NSA steering factors to earlier publications from the White Home, NIST, and OMB, this publication is related to all organizations producing and consuming software program, leveraging OSS, and seeking to embrace artifacts comparable to SBOMs. Listed here are a few of the key areas of the steering, together with suggestions and takeaways from the doc.
Construction of the NSA steering on SBOMs
The NSA steering focuses on 4 key areas, as outlined within the desk under, and aligned with their respective SSDF Actions. (Space 1 is omitted as it’s merely an introduction):
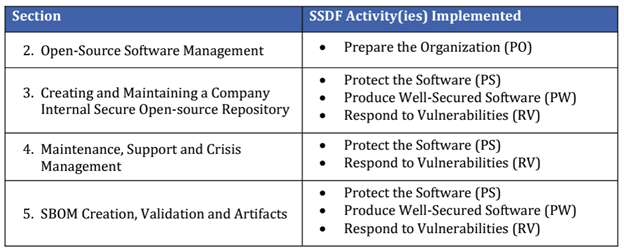
Courtesy of the US Nationwide Safety Company
US Nationwide Safety Company
Open-source software program administration
This part of the NSA steering defines key roles and tasks for builders and suppliers, amongst others. It notes that builders have tasks comparable to figuring out potential OSS options to make use of and integrating OSS options into product software program, in addition to monitoring updates to these elements. Suppliers are these producing a services or products and performing actions comparable to monitoring for license modifications or vulnerabilities of OSS elements included in merchandise, because of the dangers they may move on to downstream customers.
The NSA lays out major concerns for utilizing OSS, comparable to evaluating OSS elements for vulnerabilities in sources such because the NVD and different vulnerability databases and guaranteeing that susceptible elements aren’t being included in merchandise. It additionally recommends organizations stay conscious of licensing concerns comparable to license compliance, in addition to export controls, such because the evolving EU laws which can influence the incorporation of OSS into merchandise.