Attackers have been exploiting a brand new main flaw in Chrome—the sort that can be utilized to run malicious code on a compromised system. Revealed final Friday alongside the discharge of an emergency repair, the vulnerability requires a patch that ought to be now out there to most customers of Chrome and different Chromium browsers (like Edge). This vulnerability is being exploited within the wild so that you’ll wish to replace Chrome pronto.
If the replace has already been pushed to your copy of Chrome, you must see a small notification within the higher proper of your window (as will Edge customers). Click on on the button to use the patch and restart the browser. In any other case, observe these directions to manually confirm your browser model quantity and apply the patch:
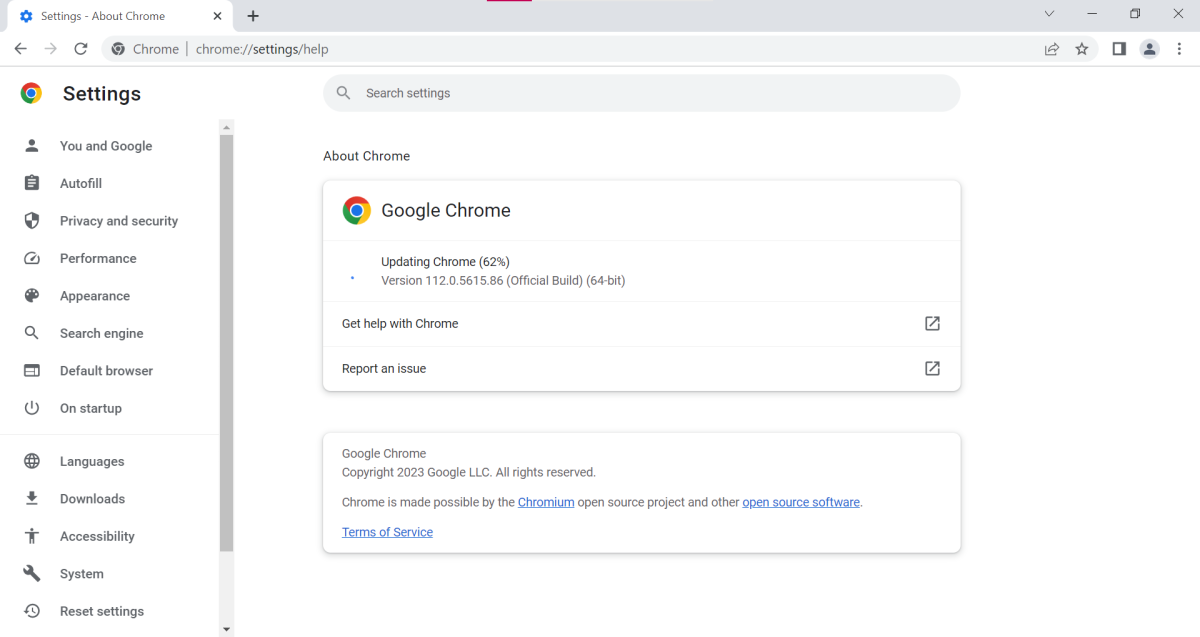
- Chrome: Click on on the three-dot settings icon on the far proper of your menu bar. Then select Assist > About Google Chrome. You may also as a substitute kind chrome://settings/assist into your tackle bar.
- Edge: Click on on the three-dot settings icon on the far proper of your menu bar. Then select Assist and suggestions > About Microsoft Edge. You may also as a substitute kind edge://settings/assist into the tackle bar.
PCWorld
For those who’re not but updated, Chrome ought to robotically start downloading the patch as quickly as you open the About Google Chrome display. It is best to then be up to date to model 112.0.5615.121. Ensure that your model quantity matches your complete string—after we checked one in every of our PCs with Chrome put in, we had been nonetheless on 112.0.5615.86, which meant the patch had not but been utilized. For Edge customers, the identical course of applies, however the remaining model quantity shall be 112.0.1722.48.
This exploit depends on a sort confusion bug in Chrome’s V8 JavaScript engine, which we’ve seen within the wild earlier than. This newest occasion is the primary one in every of 2023. Reported by Clément Lecigne of Google’s Menace Evaluation Group final Tuesday, it impacts Home windows, Linux, and macOS. Particulars of how attackers have been manipulating this bug have but to be unveiled, although, as is common when a high-severity flaw is first uncovered. The delay of a proof provides these affected time to use the repair—which now you already know to do.










