Google continues to battle with cybercriminals operating malicious adverts on its search platform to trick folks into downloading booby-trapped copies of widespread free software program purposes. The malicious adverts, which seem above natural search outcomes and sometimes precede hyperlinks to respectable sources of the identical software program, could make trying to find software program on Google a dicey affair.
Google says protecting customers secure is a high precedence, and that the corporate has a staff of hundreds working across the clock to create and implement their abuse insurance policies. And by most accounts, the risk from dangerous adverts resulting in backdoored software program has subsided considerably in comparison with a 12 months in the past.
However cybercrooks are always determining ingenious methods to fly beneath Google’s anti-abuse radar, and new examples of dangerous adverts resulting in malware are nonetheless too widespread.
For instance, a Google search earlier this week for the free graphic design program FreeCAD produced the next outcome, which reveals {that a} “Sponsored” advert on the high of the search outcomes is promoting the software program obtainable from freecad-us[.]org. Though this web site claims to be the official FreeCAD web site, that honor belongs to the outcome instantly under — the respectable freecad.org.
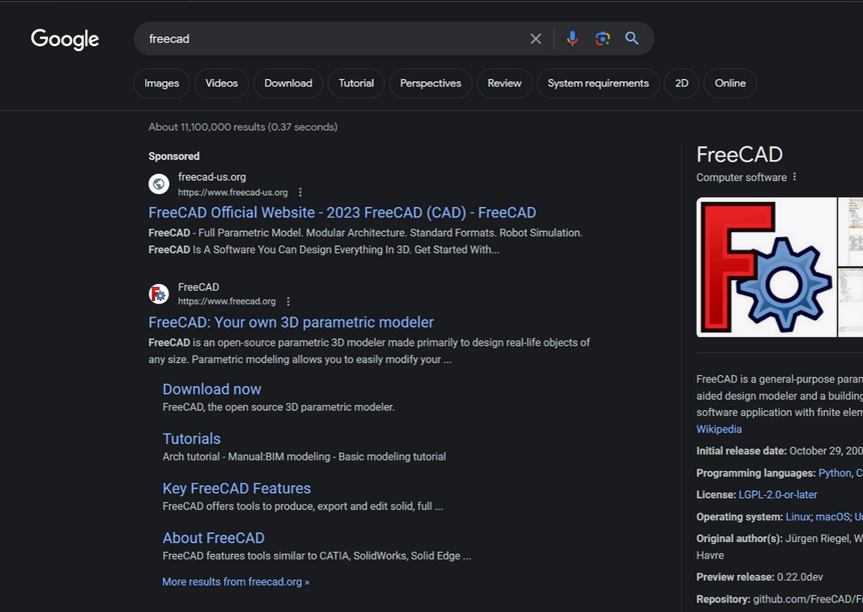
How do we all know freecad-us[.]org is malicious? A overview at DomainTools.com present this area is the latest (registered Jan. 19, 2024) of greater than 200 domains on the Web tackle 93.190.143[.]252 which might be confusingly just like widespread software program titles, together with dashlane-project[.]com, filezillasoft[.]com, keepermanager[.]com, and libreofficeproject[.]com.
A number of the domains at this Netherlands host seem like little greater than software program overview web sites that steal content material from established data sources within the IT world, together with Gartner, PCWorld, Slashdot and TechRadar.
Different domains at 93.190.143[.]252 do serve precise software program downloads, however none of them are prone to be malicious if one visits the websites by means of direct navigation. If one visits openai-project[.]org and downloads a duplicate of the favored Home windows desktop administration software Rainmeter, for instance, the file that’s downloaded has the identical precise file signature as the true Rainmeter installer obtainable from rainmeter.com.
However that is solely a ruse, says Tom Hegel, principal risk researcher on the safety agency Sentinel One. Hegel has been monitoring these malicious domains for greater than a 12 months, and he mentioned the seemingly benign software program obtain websites will periodically flip evil, swapping out respectable copies of widespread software program titles with backdoored variations that can permit cybercriminals to remotely commander the techniques.
“They’re utilizing automation to drag in faux content material, and so they’re rotating out and in of internet hosting malware,” Hegel mentioned, noting that the malicious downloads could solely be supplied to guests who come from particular geographic places, like america. “Within the malicious advert campaigns we’ve seen tied to this group, they’d wait till the domains achieve legitimacy on the various search engines, after which flip the web page for a day or so after which flip again.”
In February 2023, Hegel co-authored a report on this similar community, which Sentinel One has dubbed MalVirt (a play on “malvertising”). They concluded that the surge in malicious adverts spoofing numerous software program merchandise was instantly accountable for a surge in malware infections from infostealer trojans like IcedID, Redline Stealer, Formbook and AuroraStealer.
Hegel famous that the spike in malicious software-themed adverts got here not lengthy after Microsoft began blocking by default Workplace macros in paperwork downloaded from the Web. He mentioned the amount of the present malicious advert campaigns from this group seems to be comparatively low in comparison with a 12 months in the past.
“It seems to be similar marketing campaign persevering with,” Hegel mentioned. “Final January, each Google seek for ‘Autocad’ led to one thing dangerous. Now, it’s like they’re paying Google to get one out of each dozen of searches. My guess it’s nonetheless persevering with due to the up-and-down [of the] domains internet hosting malware after which wanting respectable.”
A number of of the web sites at this Netherlands host (93.190.143[.]252) are at present blocked by Google’s Safebrowsing know-how, and labeled with a conspicuous purple warning saying the web site will attempt to foist malware on guests who ignore the warning and proceed.
Nevertheless it stays a thriller why Google has not equally blocked extra the 240+ different domains at this similar host, or else eliminated them from its search index totally. Particularly contemplating there’s nothing else however these domains hosted at that Netherlands IP tackle, and since they’ve all remained at that tackle for the previous 12 months.
In response to questions from KrebsOnSecurity, Google mentioned sustaining a secure adverts ecosystem and protecting malware off of its platforms is a precedence throughout Google.
“Unhealthy actors usually make use of subtle measures to hide their identities and evade our insurance policies and enforcement, typically exhibiting Google one factor and customers one thing else,” Google mentioned in a written assertion. “We’ve reviewed the adverts in query, eliminated those who violated our insurance policies, and suspended the related accounts. We’ll proceed to watch and apply our protections.”
Google says it eliminated 5.2 billion adverts in 2022, and restricted greater than 4.3 billion adverts and suspended over 6.7 million advertiser accounts. The corporate’s newest advert security report says Google in 2022 blocked or eliminated 1.36 billion commercials for violating its abuse insurance policies.
A number of the domains referenced on this story had been included in Sentinel One’s February 2023 report, however dozens extra have been added since, corresponding to these spoofing the official obtain websites for Corel Draw, Github Desktop, Roboform and Teamviewer.
This October 2023 report on the FreeCAD consumer discussion board got here from a consumer who reported downloading a duplicate of the software program from freecadsoft[.]com after seeing the positioning promoted on the high of a Google search outcome for “freecad.” Virtually a month later, one other FreeCAD consumer reported getting stung by the identical rip-off.
“This acquired me,” FreeCAD discussion board consumer “Matterform” wrote on Nov. 19, 2023. “Please depart a report with Google so it could possibly flag it. They paid Google for sponsored posts.”
Sentinel One’s report didn’t delve into the “who” behind this ongoing MalVirt marketing campaign, and there are valuable few clues that time to attribution. All the domains in query had been registered by means of webnic.cc, and several other of them show a placeholder web page saying the positioning is prepared for content material. Viewing the HTML supply of those placeholder pages reveals lots of the hidden feedback within the code are in Cyrillic.
Making an attempt to trace the crooks utilizing Google’s Advert Transparency instruments didn’t lead far. The advert transparency document for the malicious advert that includes freecad-us[.]org (within the screenshot above) reveals that the promoting account used to pay for the advert has solely run one earlier advert by means of Google search: It marketed a marriage images web site in New Zealand.
The obvious proprietor of that images web site didn’t reply to requests for remark, but it surely’s additionally probably his Google promoting account was hacked and used to run these malicious adverts.