BLACK HAT ASIA – Singapore – While you’re in an setting the place the overwhelming majority of community visitors is assessed as posing a extreme cybersecurity menace, deciding what to be involved about turns into not a needle in a haystack state of affairs, however a needle in a needlestack drawback.
That is the phrase this week at Black Hat Asia, the place Neil Wyler, international lead of lively menace assessments at IBM X-Pressure, and Bart Stump, senior techniques engineer for NetWitness, took to the stage to offer attendees a glance contained in the occasion’s enterprise-grade community operations middle (NOC). The duo oversaw the NOC’s design and led the safety workforce for the present, which ran from Could 9-12. The multi-vendor community supported attendee Wi-Fi entry; inside operations reminiscent of registration; the wants of enterprise corridor stands; and the communications necessities of technical trainings, briefings, keynotes, and vendor demonstrations.
“Once we talk about the visitors, attempt to clarify to others that at Black Hat it is dangerous on a regular basis – all or a lot of the visitors is malicious,” Wyler defined. “That sounds scary, however for this crowd that visitors is regular. There are folks demoing assaults, there are crimson groups trainings occurring, and so forth., and that implies that we do not actually block something. We let that visitors fly as a result of we do not wish to take down a demo on stage or on the expo flooring. Except we see a direct assault on our infrastructure, say the registration system, we let it go.”
So, with the intention to ferret out the precise dangerous, dangerous visitors, the NOC depends on quite a lot of dashboards that permit a real-time view of every little thing flowing by way of the community, with the power to seize stats on every little thing from machine profiles to which cloud apps attendees are connecting to. It additionally captures uncooked packet information so NOC analysts can return and rebuild classes within the occasion one thing appears abnormally suspicious, to take a look at “each single factor somebody is doing with each packet, in a approach we will not utilizing simply logs,” Wyler famous.
One of many extra uncommon dashboards put in place for the occasion provided a warmth map of the place Wi-Fi, Bluetooth, and even peer-to-peer wi-fi connections had been getting used, providing a fast take a look at the place folks had been congregating and the place there may be cyber-issues afoot.
“It is an attention-grabbing perspective,” defined Stump. “The underside left nook of the map is definitely the present flooring, and after the enterprise corridor opened up, that bought extra crimson. You may see when breaks are occurring and after they put the drinks out as a result of folks migrate. And general, it is a fast visualization for us to see the place potential points may be coming from, the place we should always focus our consideration.”
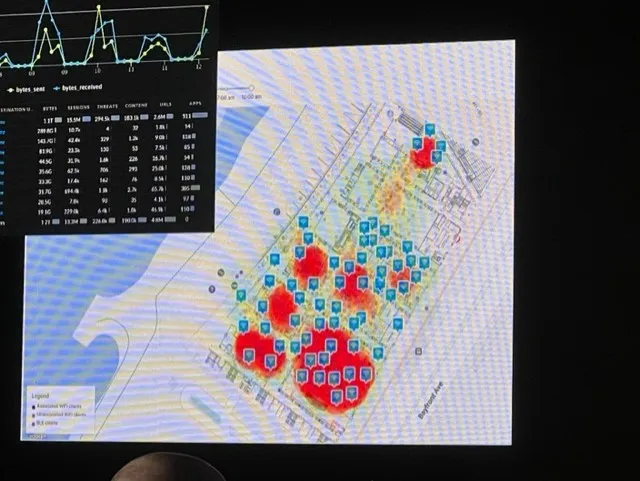
In all, the NOC tracked 1,500 whole distinctive units connecting to the community throughout cell phones, Web of issues (IoT) gear, and different endpoints, with DNS queries at their highest for the occasion since 2018. About three-quarters (72%) of that visitors was encrypted – a refreshingly excessive quantity, the researchers famous. And curiously, a site known as Hacking Clouds hosted probably the most person classes – extra even than the present’s normal Wi-Fi community for attendees.
When it comes to the apps getting used, TikTok made an look within the High 10 for the primary time, the workforce noticed. Different prime apps included Workplace 365 (no shock there), Groups, Gmail, Fb, and WhatsApp.
Attention-grabbing NOC Happenings
A couple of attention-grabbing incidents emerged from the information through the occasion, the duo famous. In a single case, a person was producing a lot malicious exercise that the entire NOC techniques alerted without delay.
“One specific particular person was so noisy that each NOC vendor accomplice noticed their exercise on the identical time,” Wyler mentioned. “We’re speaking SQL injection on public-facing web sites, WordPress compromises, heaps and plenty of scanning for vulnerabilities and open ports. It was like they realized one thing this week and went, ‘let me see if it really works. I’ve heard about Log4j, let me see what’s on the market.’ They took a coaching class and now they’re spreading their wings and flying.”
After the particular person moved from attacking restaurant chain web sites to probing cost websites, it was clear the exercise wasn’t demo-related, so the workforce pinpointed the particular person and despatched the person a cease-and-desist e-mail.
“We discovered they had been sitting within the hallway searching on the Bay, simply attacking firm after firm after firm,” Wyler mentioned. “We defined that it is nonetheless unlawful to do what they’re doing, so please discontinue trying to execute vulnerabilities on public-facing web sites. This can be a violation of the Black Hat Code of Conduct and we are going to come discover you if it would not cease – love, the NOC. They bought that and every little thing stopped.”
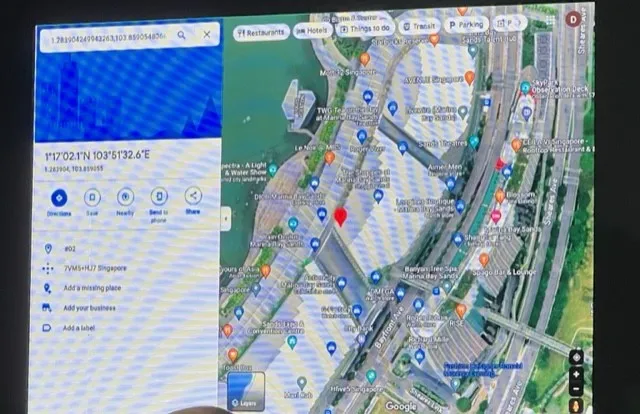
Different incidents concerned VPN points, together with one which was transmitting the person’s location info in clear textual content. The workforce captured the information, plugged it into Google Maps and generated a view of precisely the place the particular person had been through the day.
One more concern concerned an endpoint detection and response (EDR) vendor that was sending the entire utilization information it was accumulating on the endpoints of its customers in clear textual content again to its servers; and, one antivirus vendor was discovered sending unencrypted SMTP emails containing pricing quotes and different info in an unencrypted style, together with login credentials — permitting simple harvesting.
“An attacker may have pulled down quotes, modified quotes, gathered inside work info and buyer info, undoubtedly not good,” mentioned Stump. “It might be used to craft phishes or to control pricing.”
In all circumstances, the workforce labored with the problematic entities to resolve the problems. The NOC, fairly merely, is on the case, in response to Stump.
“Individuals typically say that at Black Hat, you should not even get on the community as a result of it is harmful,” mentioned Stump. “However our aim is definitely to go away attendees safer than after they arrived. And that is why we do issues like letting folks know they’re sending passwords in clear textual content, or after we see cryptomining exercise, we’ll alert them. We’re dedicated to that.”










