Tens of millions of U.S. authorities workers and contractors have been issued a safe sensible ID card that allows bodily entry to buildings and managed areas, and supplies entry to authorities laptop networks and techniques on the cardholder’s applicable safety degree. However many authorities workers aren’t issued an permitted card reader system that lets them use these playing cards at dwelling or remotely, and so flip to low-cost readers they discover on-line. What may go flawed? Right here’s one instance.

A pattern Frequent Entry Card (CAC). Picture: Cac.mil.
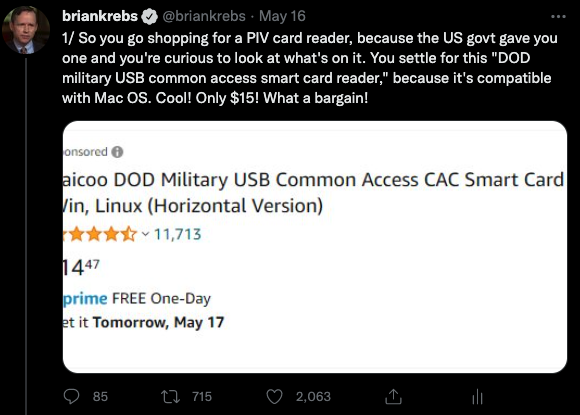
KrebsOnSecurity not too long ago heard from a reader — we’ll name him “Mark” as a result of he wasn’t licensed to talk to the press — who works in IT for a significant authorities protection contractor and was issued a Private Identification Verification (PIV) authorities sensible card designed for civilian workers. Not having a wise card reader at dwelling and missing any apparent steerage from his co-workers on the right way to get one, Mark opted to buy a $15 reader from Amazon that mentioned it was made to deal with U.S. authorities sensible playing cards.
The USB-based system Mark settled on is the primary consequence that presently comes up one when searches on Amazon.com for “PIV card reader.” The cardboard reader Mark purchased was bought by an organization referred to as Saicoo, whose sponsored Amazon itemizing advertises a “DOD Navy USB Frequent Entry Card (CAC) Reader” and has greater than 11,700 largely optimistic rankings.
The Frequent Entry Card (CAC) is the usual identification for lively obligation uniformed service personnel, chosen reserve, DoD civilian workers, and eligible contractor personnel. It’s the principal card used to allow bodily entry to buildings and managed areas, and supplies entry to DoD laptop networks and techniques.
Mark mentioned when he acquired the reader and plugged it into his Home windows 10 PC, the working system complained that the system’s {hardware} drivers weren’t functioning correctly. Home windows steered consulting the seller’s web site for newer drivers.
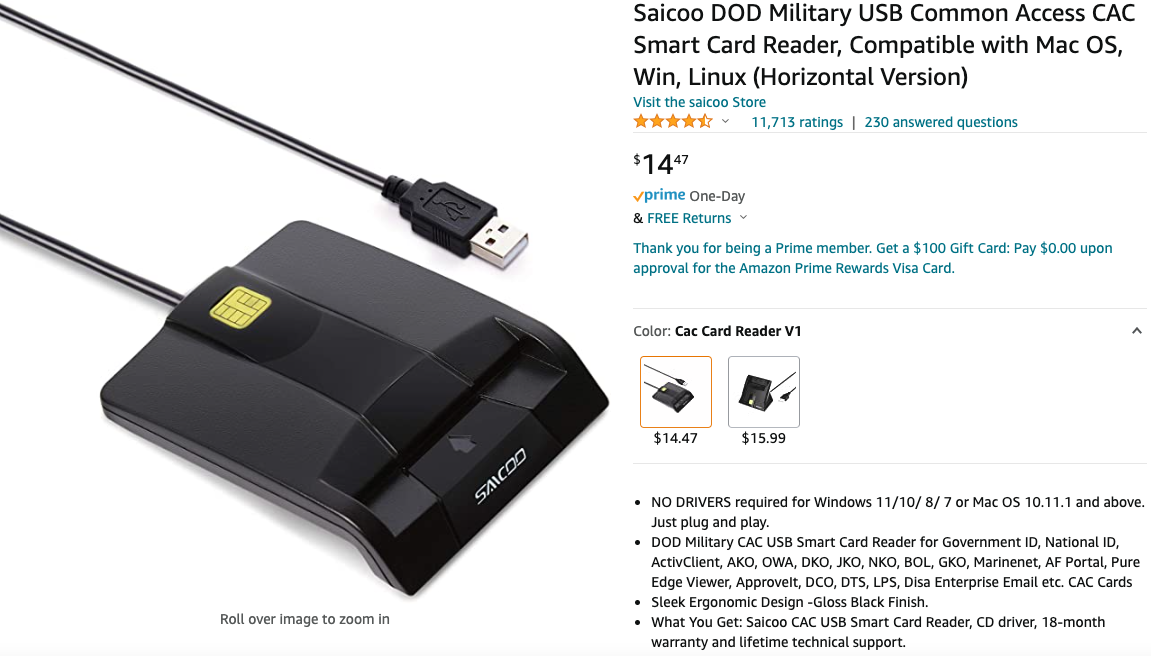
The Saicoo sensible card reader that Mark bought. Picture: Amazon.com
So Mark went to the web site talked about on Saicoo’s packaging and located a ZIP file containing drivers for Linux, Mac OS and Home windows:
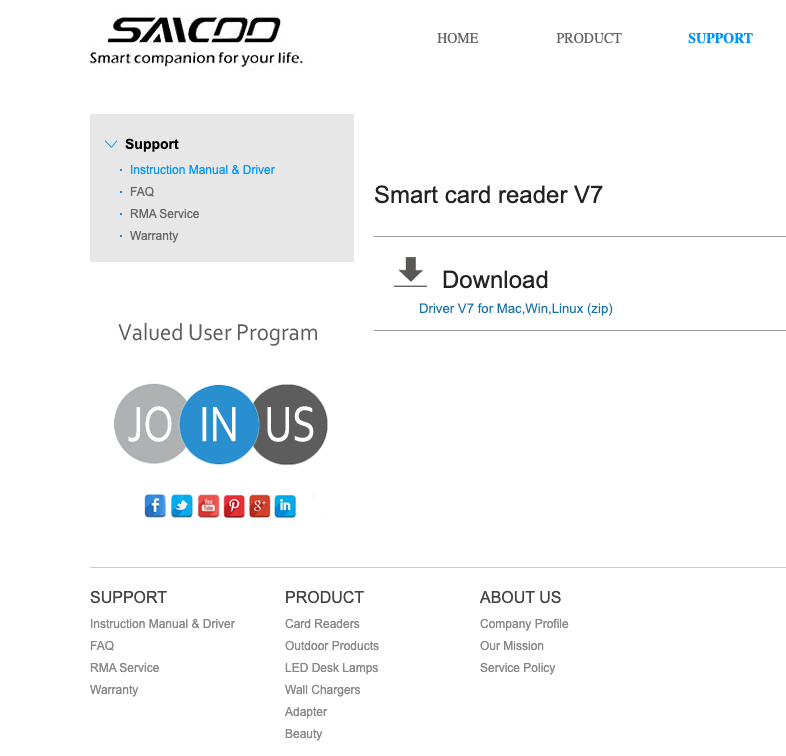
Picture: Saicoo
Out of an abundance of warning, Mark submitted Saicoo’s drivers file to Virustotal.com, which concurrently scans any shared information with greater than 5 dozen antivirus and safety merchandise. Virustotal reported that some 43 completely different safety instruments detected the Saicoo drivers as malicious. The consensus appears to be that the ZIP file presently harbors a malware menace often called Ramnit, a reasonably frequent however harmful malicious program that spreads by appending itself to different information.
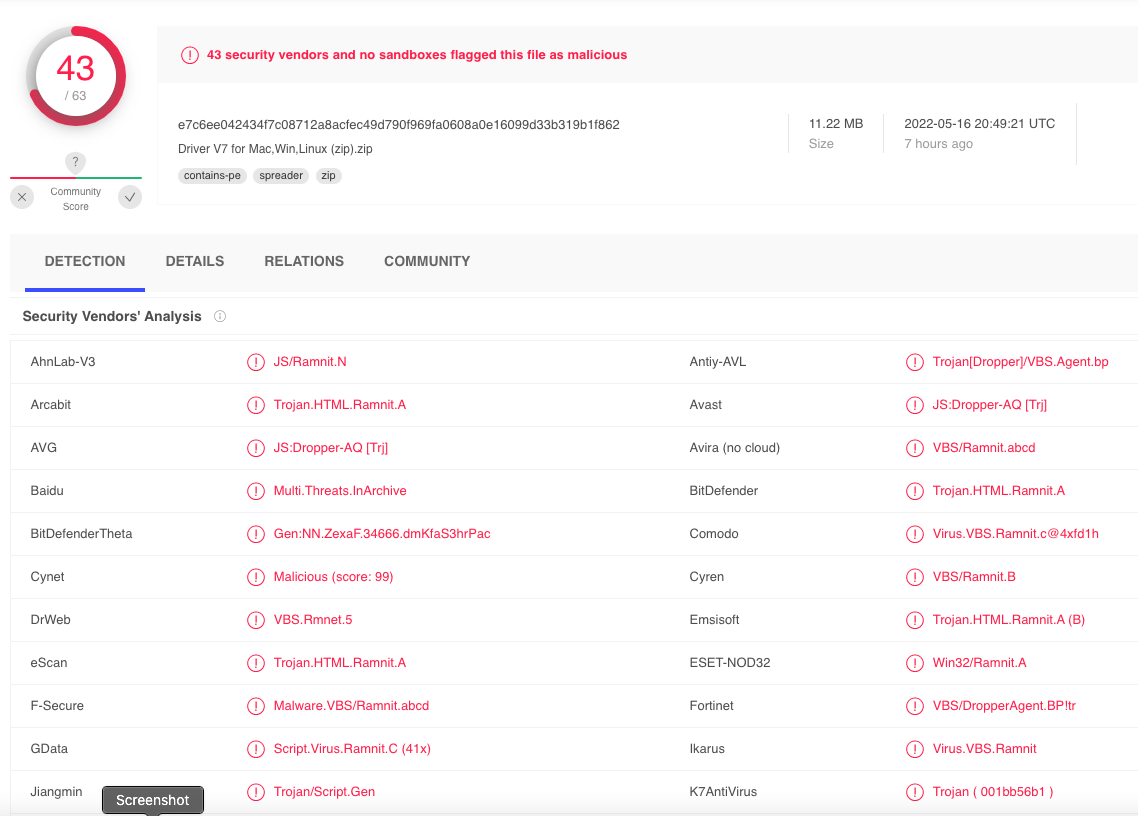
Picture: Virustotal.com
Ramnit is a widely known and older menace — first surfacing greater than a decade in the past — but it surely has advanced over time and remains to be employed in additional subtle knowledge exfiltration assaults. Amazon mentioned in a written assertion that it was investigating the stories.
“Looks like a probably vital nationwide safety danger, contemplating that many finish customers might need elevated clearance ranges who’re utilizing PIV playing cards for safe entry,” Mark mentioned.
Mark mentioned he contacted Saicoo about their web site serving up malware, and acquired a response saying the corporate’s latest {hardware} didn’t require any extra drivers. He mentioned Saicoo didn’t handle his concern that the motive force bundle on its web site was bundled with malware.
In response to KrebsOnSecurity’s request for remark, Saicoo despatched a considerably much less reassuring reply.
“From the small print you provided, concern could most likely attributable to your laptop safety protection system because it appears not acknowledged our not often used driver & detected it as malicious or a virus,” Saicoo’s help group wrote in an electronic mail.
“Really, it’s not carrying any virus as you possibly can belief us, you probably have our reader available, please simply ignore it and proceed the set up steps,” the message continued. “When driver put in, this message will vanish out of sight. Don’t fear.”
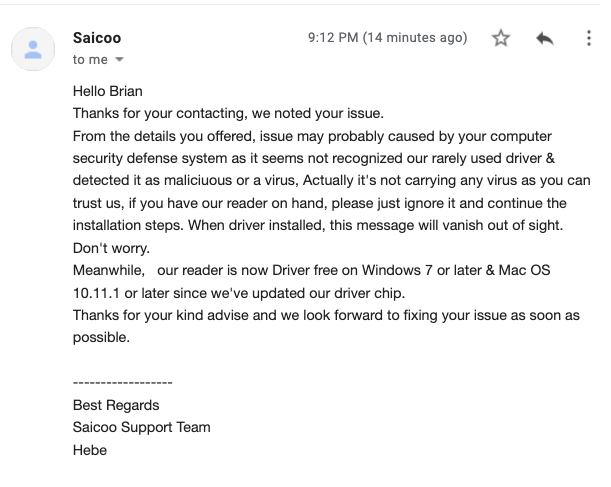
Saicoo’s response to KrebsOnSecurity.
The difficulty with Saicoo’s apparently contaminated drivers could also be little greater than a case of a know-how firm having their web site hacked and responding poorly. Will Dormann, a vulnerability analyst at CERT/CC, wrote on Twitter that the executable information (.exe) within the Saicoo drivers ZIP file weren’t altered by the Ramnit malware — solely the included HTML information.
Dormann mentioned it’s dangerous sufficient that trying to find system drivers on-line is likely one of the riskiest actions one can undertake on-line.
“Doing an online seek for drivers is a VERY harmful (when it comes to legit/malicious hit ratio) search to carry out, based mostly on outcomes of any time I’ve tried to do it,” Dormann added. “Mix that with the obvious due diligence of the seller outlined right here, and effectively, it ain’t a fairly image.”
However by all accounts, the potential assault floor right here is gigantic, as many federal workers clearly will buy these readers from a myriad of on-line distributors when the necessity arises. Saicoo’s product listings, for instance, are replete with feedback from clients who self-state that they work at a federal company (and several other who reported issues putting in drivers).
A thread about Mark’s experience on Twitter generated a powerful response from a few of my followers, a lot of whom apparently work for the U.S. authorities in some capability and have government-issued CAC or PIV playing cards.
Two issues emerged clearly from that dialog. The primary was common confusion about whether or not the U.S. authorities has any type of record of permitted distributors. It does. The Basic Companies Administration (GSA), the company which handles procurement for federal civilian businesses, maintains a listing of permitted card reader distributors at idmanagement.gov (Saicoo is just not on that record). [Thanks to @MetaBiometrics and @shugenja for the link!]
The opposite theme that ran via the Twitter dialogue was the fact that many individuals discover shopping for off-the-shelf readers extra expedient than going via the GSA’s official procurement course of, whether or not it’s as a result of they had been by no means issued one or the reader they had been utilizing merely not labored or was misplaced and so they wanted one other one rapidly.
“Virtually each officer and NCO [non-commissioned officer] I do know within the Reserve Element has a CAC reader they purchased as a result of they needed to get to their DOD electronic mail at dwelling and so they’ve by no means been issued a laptop computer or a CAC reader,” said David Dixon, an Military veteran and creator who lives in Northern Virginia. “When your boss tells you to test your electronic mail at dwelling and also you’re within the Nationwide Guard and you reside 2 hours from the closest [non-classified military network installation], what do you assume goes to occur?”
Apparently, anybody asking on Twitter about the right way to navigate buying the correct sensible card reader and getting all of it to work correctly is invariably steered towards militarycac.com. The web site is maintained by Michael Danberry, a embellished and retired Military veteran who launched the positioning in 2008 (its textual content and link-heavy design very a lot takes one again to that period of the Web and webpages usually). His web site has even been formally advisable by the Military (PDF). Mark shared emails displaying Saicoo itself recommends militarycac.com.

Picture: Militarycac.com.
“The Military Reserve began utilizing CAC logon in Could 2006,” Danberry wrote on his “About” web page. “I [once again] turned the ‘Go to man’ for my Military Reserve Middle and Minnesota. I believed Why cease there? I may use my web site and data of CAC and share it with you.”
Danberry didn’t reply to requests for an interview — little question as a result of he’s busy doing tech help for the federal authorities. The pleasant message on Danberry’s voicemail instructs support-needing callers to depart detailed details about the problem they’re having with CAC/PIV card readers.
Dixon mentioned Danberry has “completed extra to maintain the Military working and linked than all of the G6s [Army Chief Information Officers] put collectively.”
In some ways, Mr. Danberry is the equal of that little recognized software program developer whose tiny open-sourced code mission finally ends up turning into broadly adopted and ultimately folded into the material of the Web. I ponder if he ever imagined 15 years in the past that his web site would someday grow to be “crucial infrastructure” for Uncle Sam?










