
As has been broadly documented, distributed denial of service, or DDoS, assaults rose precipitously final yr. A microcosm of this upward pattern concerned exploits focusing on public info websites and tied to political occasions, together with the conflict in Ukraine and the midterm elections within the U.S.
In response to the rise in politically motivated DDoS assaults, Google is providing a free service known as Challenge Protect to authorities websites, information and impartial journalists, websites associated to elections and voting, and websites that cowl human rights (Determine A).
Determine A
SEE: Learn right here to study why it’s “shields up” time for all enterprises — public or non-public sector.
Community safety agency Cloudflare reported DDoS assault site visitors worldwide elevated by 79% year-over-year in This fall 2022. It famous that a lot of the assaults have been small, however standouts have been terabit-strong DDoS assaults within the a whole lot of hundreds of thousands of packets per second, with large-scale assaults powered by botnets.
Microsoft famous in a February weblog put up that 42% of all DDoS assaults final yr occurred within the U.S. Examples within the U.S. and different nations of politically motivated assaults final yr embody:
- Russian state actors launched a DDoS assault in opposition to U.S. Congress web sites in July.
- In November 2022, the European Parliament’s web site was attacked by pro-Russia hacker group, Killnet.
- Cybersecurity agency Radware reported DDoS assaults by Malaysian hacktivists in opposition to Israel and India as a response to political occasions.
- CNN, Rappler, ABS-CBN, and VERA Information have been hit by politically motivated DDoS assaults, in line with Radware.
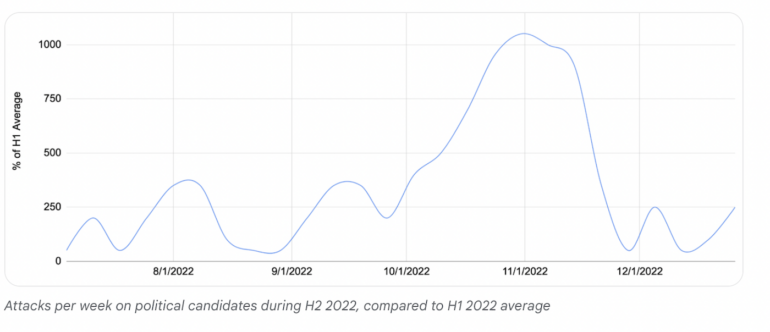
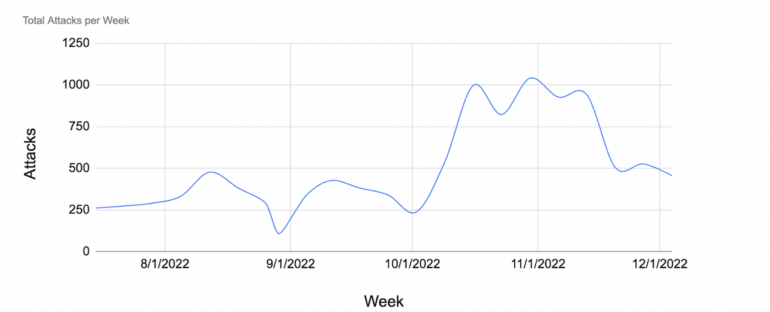
In its personal report utilizing knowledge from Challenge Protect, Google famous that in final yr’s election cycle within the U.S., assaults in opposition to web sites that self-identified as providing election info on their Challenge Protect software noticed a surge in assaults:
- The corporate reported a 400% rise in DDoS assaults on its prospects throughout final yr’s election season within the U.S.
- Within the second half of 2022, Challenge Protect noticed over 25,000 such assaults in opposition to prospects, lots of them 100,000 queries per second in dimension.
“One factor we noticed in Ukraine have been focused assaults to carry down vital infrastructure web sites and different websites that assist Ukraine communities get entry to info. Identical factor we see prolonged into our elections right here: to disclaim customers entry to info,” mentioned Muninder Sambi, vice chairman, networking and safety at Google Cloud.
“These can occur from wherever on the earth,” Sambi mentioned. “All you want is public entry to the positioning. Additionally in case you don’t have the technical prowess, you should buy them from the darkish internet by DDoS for rent,” he added. (Determine B)
Determine B
What’s Challenge Protect?
Challenge Protect, created by Google Cloud and Jigsaw and powered by Google Cloud Armor, filters out malicious site visitors utilizing Google’s infrastructure and DDoS instruments.
SEE: Cybersecurity: A la carte or a complete suite of options?
Sambi mentioned the know-how challenges each the most typical DDoS assault: brute drive exploits that overload goal servers with queries, primarily shutting them down. He added that Challenge Protect can also be automated, and pushed by a machine learning-powered again finish that permits a “protection in depth” technique.
In response to Google, to detect, deflect and mitigate assaults, Challenge Protect includes the Google Cloud Armor community safety system — which incorporates such options as an ML mechanism to detect and block software layer DDoS assaults, and bot administration on the cloud edge. It additionally makes use of cloud-based content material supply networks and load-balancing applied sciences.
“Final yr we stopped an assault, among the many largest that has ever occurred, that delivered 47 million requests per second, focused to one among our prospects,” Sambi mentioned. “And with out requiring the shopper to configure something, utilizing full automation, we have been capable of defend in opposition to it.”
He added {that a} excessive degree of automation with no buyer protection cooperation wanted was an necessary side of the product. “Loads of our prospects say it’s actually laborious to handle a DDoS answer and to know what constitutes official assaults. Additionally, adversaries are getting bolder and utilizing AI and machine studying instruments to infiltrate internet companies throughout the globe in a method they will bypass DDoS mechanisms. So, with our ML again finish we are able to inform which incoming requests are official or not.”
How Challenge Protect mitigates DDoS assaults
Challenge Protect is what is called a reverse proxy. The platform’s servers obtain site visitors requests on an internet site’s behalf after which ship site visitors to the servers of the web site that’s utilizing the safety product. Google mentioned Challenge Protect protects in opposition to DDoS by filtering dangerous site visitors and by caching variations of an internet site’s content material to serve to the positioning’s guests. This caching reduces site visitors requests to a website’s server, absorbing potential DDoS assaults.
Moreover, Challenge Protect incorporates these extra options to guard shoppers in opposition to DDoS assaults:
Load balancing helps scale back influence of DDoS assaults
Load balancing distributes community site visitors to stop failure attributable to overloading a specific useful resource, in line with IBM. It improves the efficiency and availability of purposes, web sites, databases, and different computing assets, per the corporate. However, as a result of it distributes site visitors to completely different nodes it additionally reduces the drive of a DDoS assault in the identical method a number of route choices for autos helps mitigate site visitors jams throughout rush hour.
CDNs protects in opposition to DDoS by shifting content material to the sting cloud
Content material supply networks assist cache content material on the community edge, which improves web site efficiency. By caching content material on the edge, nearer the tip consumer, the content material supplier is ready to “carry” much less throughout networks, a lot as a hiker who caches their provides alongside a route has much less to hold alongside the best way. In response to Cloudflare, CDN additionally helps stop interruptions in service, and mitigates interruptions attributable to DDoS assaults.
Sambi mentioned each CDN and cargo balancing are already utilized by most Google Cloud prospects.
“At any time when a buyer of ours builds an internet service in Google Cloud, or another cloud, and desires international attain, they use a CDN providing to allow them to ship the perfect buyer expertise for preliminary web page loading,” he mentioned. “Clients use loading balancing to supply auto-scaling of the web site when site visitors on the web site will increase lots.
“Lots of our prospects consider safety as an afterthought, however one among our methods is ensuring safety is embedded, not bolted on. That’s why the Google Cloud Armor infrastructure is absolutely built-in into our load balancer in addition to CDN, impartial of the place the consumer or site visitors comes from, so we’re capable of defend in opposition to DDoS assaults.”
Google says Challenge Protect stops nearly all DDoS assaults
Google Cloud claims 95% efficacy of Challenge Protect in defending in opposition to DDoS assaults. It derives that share from its metrics protecting probe makes an attempt in opposition to all of its prospects in periods of time throughout which Google Cloud’s system labeled web sites as “below assault.” Within the context of Google Cloud, this could imply, amongst different elements, proof of abusive site visitors patterns from a number of shoppers.
What’s to return? Consultants say extra political DDoS assaults
“In 2023, the democratization of DDoS and patriotic hacktivism will proceed to drive a rise in smaller, extra frequent assaults – a pattern we’re already seeing within the elevated frequency of decrease quantity assaults in [Europe, the Middle East and Africa]. On the identical time, count on the cybercrime underground to grow to be even higher organized and funded in its pursuit of hard-hitting assaults,” mentioned Google Cloud in an announcement launched Monday.
Microsoft, in its weblog, additionally reported politically motivated cybercrime growing this yr, with DDoS assaults changing into used as distractions to cover extortion and knowledge theft. The corporate sees new IoT DDoS botnets rising.
“As geopolitical tensions proceed to emerge globally, we are going to probably proceed to see DDoS getting used as a main software for cyberattacks by hacktivists,” it mentioned.
Who can apply for Challenge Protect?
Information, human rights, and election monitoring web sites are eligible to use, in line with Google, which mentioned authorities entities below exigent circumstances and never topic to sanctions are additionally eligible. Challenge Protect individually critiques purposes and invitations eligible candidates on a rolling foundation, in line with the corporate, which explains pricing for its paid model right here.
Learn how to study extra about Google Cloud
In case you are considering studying extra about cloud computing, stand up to hurry with the Google Cloud platform with a whole Google Cloud eBook and video course bundle. Test it out right here.










